Windows is the most widely used operating system in the world, powering millions of personal computers, laptops, and business systems. This popularity, however, makes it a prime target for hackers, malware developers, and cybercriminals. Without proper security measures, a Windows system can quickly fall victim to viruses, ransomware, phishing attacks, and unauthorized access.
In this comprehensive guide, we’ll explore best practices, tools, and strategies for securing your Windows system, whether you’re an individual user or managing a business network.
Why Windows Security Matters
Most Targeted OS
Due to its large user base, Windows is the most attacked operating system globally.
Data Privacy Concerns
Personal files, login credentials, and financial data are often stored on Windows systems, making them attractive targets.
Business Continuity
A single attack on a Windows server or workstation can disrupt operations, cause downtime, and lead to financial losses.
Regulatory Compliance
Organizations using Windows must secure data to comply with GDPR, HIPAA, PCI DSS, and ISO 27001 standards.
Common Security Risks for Windows Systems
Malware and Ransomware
Viruses, worms, and ransomware can encrypt or steal files, demanding payment for recovery.
Phishing Attacks
Users may be tricked into downloading malicious files or revealing login credentials.
Weak Passwords
Simple or reused passwords allow attackers to gain easy access.
Outdated Software
Unpatched systems contain known vulnerabilities that attackers exploit.
Unauthorized Access
Lack of user account restrictions or poor configurations may lead to intrusions.

Step-by-Step Guide to Securing Your Windows System
1. Keep Your System Updated
-
Enable Windows Update for automatic patching.
-
Regularly update drivers and third-party applications.
-
Install critical security patches immediately.
2. Use a Strong Antivirus and Anti-Malware Solution
-
Microsoft Defender (built-in) offers decent protection, but pairing it with third-party solutions like Bitdefender, Kaspersky, or Malwarebytes enhances security.
-
Enable real-time scanning and schedule regular scans.
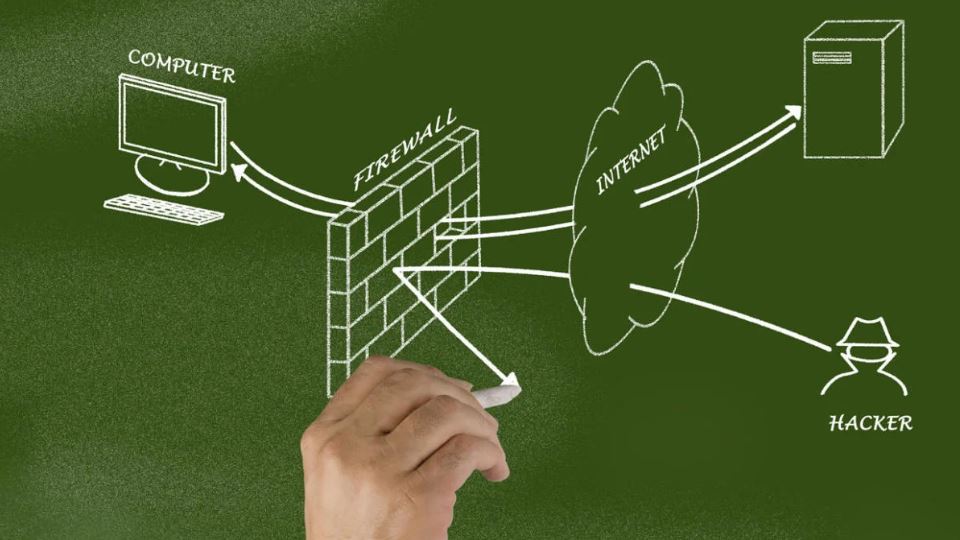
3. Enable a Firewall
-
Windows Firewall (now called Windows Defender Firewall) blocks unauthorized network access.
-
Configure inbound and outbound rules for sensitive applications.
-
For advanced users, consider third-party firewalls for more granular control.
4. Strong Passwords and Multi-Factor Authentication (MFA)
-
Create complex passwords with letters, numbers, and symbols.
-
Avoid using the same password across multiple accounts.
-
Enable Windows Hello (fingerprint, face recognition, or PIN) for stronger login security.
-
Use MFA for Microsoft accounts and cloud services.
5. Secure Your User Accounts
-
Do not use an Administrator account for daily tasks.
-
Create a Standard User account for regular use.
-
Disable guest accounts.
-
Limit administrative privileges only to trusted users.
6. Encrypt Your Data
-
Use BitLocker Drive Encryption to secure your hard drives.
-
Enable Encrypting File System (EFS) for specific folders.
-
Store encryption recovery keys securely offline.
7. Backup Your Files Regularly
-
Use Windows Backup and Restore or third-party tools.
-
Maintain both local backups (external HDD/SSD) and cloud backups.
-
Follow the 3-2-1 rule: 3 copies, 2 media types, 1 offsite copy.
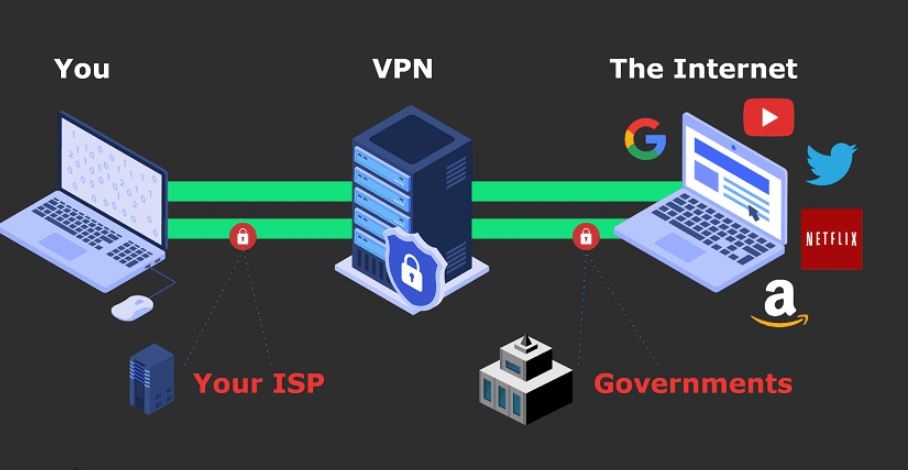
8. Secure Your Internet Connection
-
Use a Virtual Private Network (VPN) when on public Wi-Fi.
-
Change router default credentials.
-
Enable WPA3 encryption on Wi-Fi networks.
-
Disable unused network adapters.
9. Disable Unnecessary Services and Features
-
Turn off Remote Desktop if not needed.
-
Disable file and printer sharing on public networks.
-
Stop unused services (e.g., Bluetooth if not in use).
10. Manage Software and Downloads
-
Download apps only from Microsoft Store or trusted sources.
-
Avoid pirated software—it often contains malware.
-
Use application whitelisting to block unauthorized programs.
Advanced Security Measures
Windows Defender Exploit Guard
Protects against exploits, ransomware, and malicious scripts.
Secure Boot & UEFI
Prevents unauthorized software from loading during system startup.
Windows Sandbox
Run suspicious apps in an isolated environment.
Device Guard and Credential Guard
Prevent unauthorized code execution and protect login credentials from theft.
Security Best Practices for Businesses
Centralized Patch Management
Use Windows Server Update Services (WSUS) or Microsoft Endpoint Manager.
Group Policy Management
Restrict access, enforce password complexity, and disable risky features via Group Policies.
Data Loss Prevention (DLP)
Prevent sensitive data from being copied, emailed, or uploaded without authorization.
Endpoint Detection and Response (EDR)
Deploy tools like Microsoft Defender for Endpoint for proactive threat detection.
Common Mistakes to Avoid
-
Ignoring software updates.
-
Using “123456” or “password” as credentials.
-
Disabling firewalls or antivirus for performance.
-
Sharing accounts between multiple users.
-
Leaving laptops unattended without a lock screen.
Real-World Examples
WannaCry Ransomware (2017)
Exploited outdated Windows systems, causing billions in damages. Lesson: Always patch your system.
SolarWinds Attack (2020)
Showed the risks of compromised software updates. Lesson: Use trusted vendors and verify digital signatures.
Future of Windows Security
AI-Powered Security Tools
Windows will integrate deeper AI monitoring for malware detection.
Zero-Trust Architecture
Future security will assume no device or user is trusted until verified.
Hardware-Based Security
Features like TPM (Trusted Platform Module) will become mandatory for encryption and authentication.

Conclusion
Securing your Windows system requires a proactive, layered defense strategy. From applying regular updates and enabling firewalls to using strong authentication and encryption, each step significantly reduces risks.
By following the best practices outlined in this guide, you can protect your system against evolving threats and ensure your personal and business data remains safe.