Quick Navigation
Is There a Code to Check If Your Phone Is Hacked?
Concerns about phone hacking have increased sharply in recent years. Shortcodes, secret menus, and viral “check codes” are often shared online with claims that they can instantly reveal spyware or hacking activity. These claims sound convincing, but they rarely reflect how modern mobile operating systems actually work.
This article explains what a “code to check if phone is hacked” really means, what such codes can and cannot do, and how spyware is realistically detected. The goal is to replace myths with accurate, practical understanding.
code to check if phone is hacked: separating myth from reality
The idea of dialing a code to instantly detect hacking is appealing. Unfortunately, it oversimplifies a complex security problem.
Where these codes come from
Most commonly shared codes are:
-
Network diagnostic codes
-
Device information shortcuts
-
Call forwarding status checks
They were never designed as security scanners.
Why people believe these codes work
When a code displays technical information, it feels authoritative. Unfamiliar output is often interpreted as evidence of hacking.
In reality, the data shown is usually normal system behavior.
The fundamental limitation of dial codes
Dial codes can query system settings. They cannot scan installed apps, inspect permissions, or analyze background processes.
Spyware detection requires deeper access than these codes provide.
What dial codes can actually tell you
Some codes do have limited diagnostic value, but their scope is narrow.
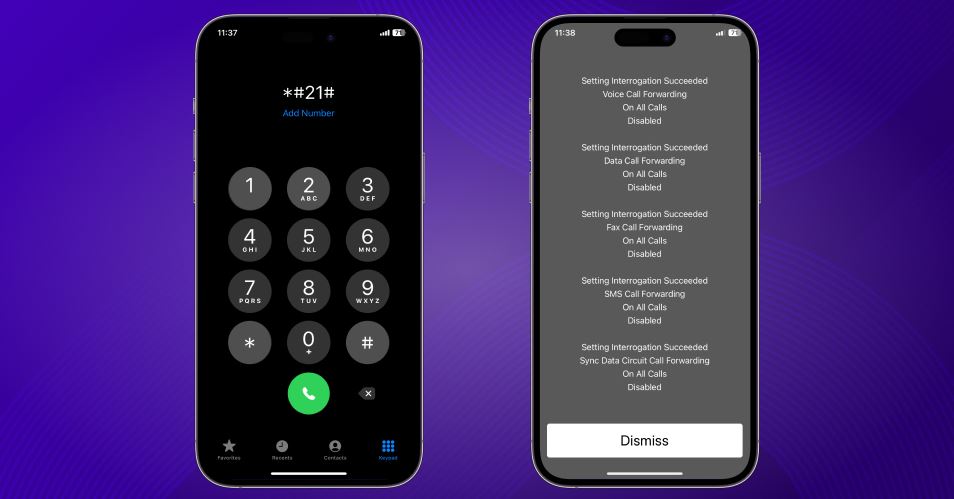
Call forwarding inspection codes
Certain codes display whether calls or messages are being forwarded. Unexpected forwarding may indicate misconfiguration or carrier-level changes.
However, forwarding alone does not confirm spyware.
Device status and network information
Some codes show signal strength, network type, or hardware identifiers. These values are informational, not diagnostic.
They do not reveal malicious activity.
Why results are often misinterpreted
Normal carrier settings, voicemail configurations, or roaming behavior can appear suspicious to non-technical users.
This misunderstanding fuels false positives.
How spy apps actually operate on modern phones
Understanding spyware behavior clarifies why simple codes are ineffective.
Permission-based surveillance
Modern spy apps rely on permissions. They request access to:
-
Microphone
-
Location
-
Messages
-
Accessibility services
If granted, they operate within OS rules.
Stealth through legitimate system features
Many surveillance apps hide behind system-level privileges or accessibility functions.
They avoid detection by behaving like normal services.
Platform security restrictions
Android and iOS restrict app visibility and sandbox processes. One app cannot inspect another app’s behavior freely.
This is a core design principle of mobile security.
Common signs often mistaken for hacking
Many symptoms attributed to hacking have benign explanations.
Battery drain and heat
Background syncing, poor signal, or aging batteries often cause rapid drain and heat.
These are not reliable indicators on their own.
Data usage spikes
Cloud backups, app updates, or media streaming can increase data usage unexpectedly.
Spyware is only one of many possibilities.
Random pop-ups or ads
Adware and aggressive apps are different from targeted spyware.
Confusing them leads to incorrect conclusions.
This confusion overlaps with mobile malware misconceptions.
Reliable ways to assess phone compromise
Effective detection relies on systematic evaluation.
Reviewing app permissions manually
Checking which apps have access to sensitive permissions is one of the most effective steps.
Unrecognized apps with extensive privileges are a red flag.
Inspecting installed apps list
Spy apps often disguise their names. Sorting apps by install date or permission usage can expose anomalies.
This process supports mobile security auditing.
Monitoring system behavior patterns
Repeated crashes, persistent accessibility services, or inability to revoke permissions may indicate deeper compromise.
Patterns matter more than isolated events.
Built-in security tools and platform protections
Modern operating systems include security features that outperform dial codes.
Android security features
Android provides app permission controls, Play Protect scanning, and security updates.
These tools actively monitor app behavior.
iOS security model
iOS enforces stricter sandboxing and limits background activity. Spyware typically requires device compromise or configuration profiles.
Unauthorized profiles are a significant warning sign.
Limitations of built-in protections
No system is infallible. Social engineering remains a common attack vector.
User awareness complements technical controls.
Professional observation from real investigations
In multiple device security assessments, users frequently cited dial codes as evidence of hacking. In nearly all cases, no spyware was present. Instead, misinterpreted network settings or legitimate system services triggered concern.
In contrast, confirmed spyware cases consistently involved:
-
Physical device access by another person
-
Explicit permission approval
-
Installation from untrusted sources
This pattern highlights a critical insight. Spyware depends more on access and permissions than on hidden exploits.
What to do if you strongly suspect spyware
When suspicion persists, structured action is required.
Revoke unnecessary permissions
Remove sensitive permissions from apps that do not clearly need them.
This step alone disables many surveillance tools.
Uninstall unknown or suspicious apps
If an app cannot be identified or justified, remove it.
Legitimate apps tolerate removal; spyware often resists.
Factory reset as a last resort
A full reset removes most consumer-grade spyware. Devices should be updated and restored carefully afterward.
This aligns with device incident response basics.
Why “secret codes” continue to circulate
Despite their ineffectiveness, these codes remain popular.
Simplicity versus reality
Users prefer simple solutions to complex problems. Codes promise certainty without effort.
Security rarely works that way.
Social media amplification
Short, alarming content spreads faster than nuanced explanations.
Accuracy is often sacrificed for engagement.
False sense of control
Codes provide action, even if the action is meaningless.
Understanding replaces anxiety with informed judgment.
For general background context, mobile phone security overview explains how mobile security actually functions at a system level.
Frequently Asked Questions (FAQ)
Is there a code to check if phone is hacked?
No, dial codes cannot reliably detect spyware or hacking.
Can spy apps hide from normal users?
Yes, many rely on permissions and system features to remain unnoticed.
Do call forwarding codes show hacking?
They only show forwarding status, not spyware presence.
What is the most reliable way to detect spy apps?
Reviewing permissions, installed apps, and system behavior patterns.
Closing perspective
There is no magic code that can confirm whether a phone is hacked. Real spyware detection depends on understanding permissions, access, and behavior rather than secret shortcuts. By replacing myths with accurate knowledge, users gain real control over their device security instead of relying on false reassurance.





