Common phishing email templates used by attackers follow predictable patterns designed to manipulate trust, urgency, and routine behavior. While the wording may change, the structure of phishing emails remains remarkably consistent across industries and attack campaigns.
Understanding common phishing email templates helps users and organizations recognize attacks before interacting with them. This article breaks down the most frequently used phishing email templates, explains how attackers design them, and shows why these phishing email patterns continue to succeed.
Quick Navigation
Phishing Email Templates That Impersonate Account Security Alerts
Account Security Phishing Email Template Explained
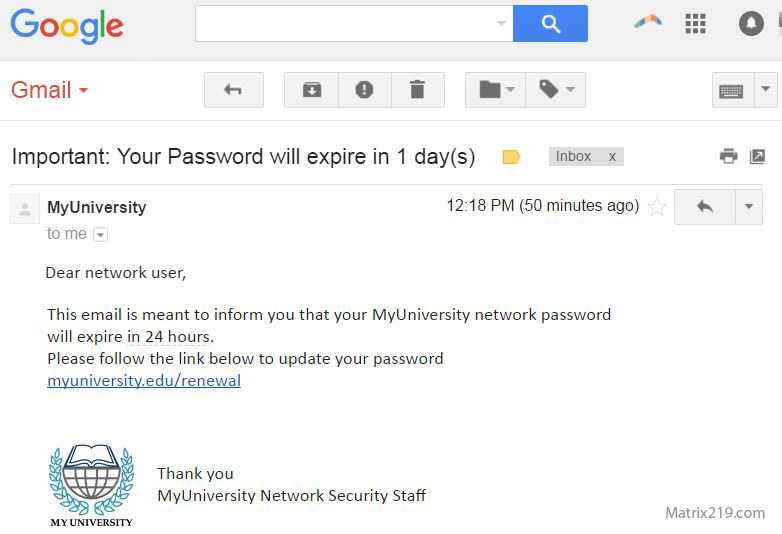
One of the most common phishing email templates claims there is a security issue with an account.
This phishing email template typically:
-
Warns of suspicious activity
-
Threatens account suspension
-
Demands immediate action
These phishing emails rely heavily on fear and urgency to bypass verification, a tactic explained in The Role of Trust, Fear, and Urgency in Social Engineering
Phishing Email Templates Using Fake Password Reset Requests
Password Reset Phishing Email Template Breakdown
Another widely used phishing email template involves fake password reset messages.
This phishing email template:
-
Mimics login services
-
Includes reset links
-
Pushes fast action
Victims are redirected to credential harvesting pages, aligning with techniques described in Credential Harvesting Attacks Explained
Phishing Email Templates That Imitate Invoice and Payment Requests
Invoice Phishing Email Template Explained
Invoice-based phishing email templates target finance-related workflows.
These phishing email templates often:
-
Appear to come from vendors
-
Reference outstanding payments
-
Attach fake invoices or links
This template is commonly used in business-focused phishing attacks, including Business Email Compromise (BEC) Attacks Explained
Phishing Email Templates That Exploit Package Delivery Notifications
Delivery Notification Phishing Email Template Explained
Delivery-themed phishing email templates claim problems with shipments or packages.
These phishing email templates include:
-
Tracking links
-
Delivery failure notices
-
Requests to confirm information
Because package notifications feel routine, users often act without scrutiny.
Phishing Email Templates That Impersonate Executives or Management
Executive Impersonation Phishing Email Template Explained
Some phishing email templates impersonate executives or managers.
These phishing email templates:
-
Use authority-based language
-
Demand confidentiality
-
Request urgent actions
This approach directly supports attacks such as CEO Fraud: How Executives Are Targeted by Phishing
Phishing Email Templates Using Document Sharing and Collaboration Tools
Document Sharing Phishing Email Template Explained
Attackers frequently use phishing email templates that claim a document has been shared.
These phishing email templates often:
-
Reference cloud platforms
-
Use familiar collaboration language
-
Prompt immediate review
These templates blend into modern work environments and reflect patterns seen in Email Phishing Examples and How to Spot Them
Why Phishing Email Templates Are Reused by Attackers
Why Repeating Phishing Email Templates Works
Phishing email templates are reused because:
-
They are proven effective
-
Minor changes evade filters
-
Human behavior remains predictable
This explains why phishing continues to outperform technical attacks, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
How Phishing Email Templates Bypass Security Controls
Phishing Email Template Design and Security Evasion
Phishing email templates bypass defenses by:
-
Avoiding malware
-
Using legitimate language
-
Triggering valid user actions
This aligns with how social engineering bypasses technical security, as explained in How Social Engineering Attacks Bypass Technical Security
Phishing Email Template Red Flags Users Commonly Miss
Warning Signs Inside Phishing Email Templates
Common phishing email template red flags include:
-
Generic greetings
-
Unexpected requests
-
Urgent tone
-
Slight sender address variations
These indicators overlap with warning signs covered in Common Social Engineering Red Flags Most Users Miss
common phishing email templates
How Organizations Can Train Against Phishing Email Templates
Defending Against Common Phishing Email Templates
Effective defense includes:
-
Teaching employees template patterns
-
Simulating real phishing email templates
-
Encouraging pause-and-verify behavior
Training users to recognize structure is more effective than memorizing examples.
External Perspective on Phishing Email Templates
Cybersecurity awareness programs consistently emphasize that recognizing phishing email templates is key to preventing account compromise, as highlighted in CISA Phishing Awareness Resources
❓ Frequently Asked Questions (FAQ)
What are phishing email templates?
They are reusable message structures attackers use to trick recipients into unsafe actions.
Do phishing email templates change often?
The wording changes, but the core structure stays the same.
Are phishing email templates easy to detect?
They can be, once users understand common patterns.
Do attackers reuse the same phishing email templates?
Yes. Successful templates are reused across campaigns.
Is recognizing templates better than spotting keywords?
Yes. Structure-based recognition is more reliable than keyword detection.
Conclusion
Common phishing email templates used by attackers reveal how phishing succeeds by repeating proven psychological patterns. While tools evolve, attackers rely on familiar structures that manipulate trust, urgency, and routine behavior.
Understanding these phishing email templates helps users recognize attacks early and respond safely. In phishing defense, recognizing patterns is more powerful than spotting individual scams.





