Common social engineering red flags are often subtle, easy to overlook, and intentionally designed to feel normal. Unlike obvious scams, modern social engineering attacks blend into everyday communication, making victims believe nothing unusual is happening.
Attackers rely on small behavioral cues rather than technical tricks. These cues rarely trigger alarms, yet they consistently precede successful compromise. This article highlights the most common social engineering warning signs users miss, explains why they work, and shows how recognizing them early can stop attacks before damage occurs.
Quick Navigation
Red Flag 1: Urgency That Overrides Normal Process
One of the strongest indicators of social engineering is artificial urgency.
Examples include:
-
“This must be done immediately”
-
“You will lose access if you delay”
-
“I need this resolved right now”
Urgency pushes victims to act before verifying legitimacy. This tactic is deeply rooted in the psychological manipulation explained in The Psychology Behind Social Engineering Attacks
Red Flag 2: Authority Without Verification
Attackers often impersonate:
-
Executives
-
IT staff
-
Vendors
-
Government representatives
Requests framed as coming from authority figures discourage questioning. This pattern frequently appears during the engagement phase of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Red Flag 3: Requests That Break Normal Procedure
Social engineering often requires victims to:
-
Skip verification steps
-
Ignore policy
-
Bypass approval processes
Any request that asks you to “make an exception” should raise suspicion, especially when combined with urgency or authority.
Red Flag 4: Emotional Pressure Over Logical Explanation
Attackers favor emotional triggers such as:
-
Fear of consequences
-
Desire to help
-
Avoidance of conflict
When emotions dominate the interaction, rational evaluation decreases. This explains why social engineering frequently outperforms malware, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
Red Flag 5: Overly Polished or Unusual Communication
Some attacks use:
-
Perfectly written messages
-
Unusual formality
-
Language inconsistent with normal contacts
Others intentionally include minor errors to lower suspicion. Both extremes can indicate manipulation rather than authenticity.
Red Flag 6: Unexpected Contact Channels
Receiving requests through:
-
Personal email accounts
-
Messaging apps
-
Social media platforms
Instead of official channels is a strong warning sign. Attackers exploit informal platforms to avoid scrutiny and logging.
Red Flag 7: Requests for Information You “Should Already Have”
Legitimate staff rarely ask for:
-
Passwords
-
Full authentication details
-
Security codes
Requests for such information indicate deception, reinforcing the definition outlined in What Is Social Engineering in Cybersecurity? (Updated Definition)
Why Users Miss These Red Flags
Red flags are missed because:
-
Attacks mimic routine tasks
-
Victims are busy or distracted
-
Trust has already been established
This dynamic supports the idea that humans are often the weakest layer in security, as explored in Why Humans Are the Weakest Link in Cybersecurity
How Attackers Combine Multiple Red Flags
Successful attacks rarely rely on one signal.
Attackers layer:
-
Urgency + authority
-
Trust + emotional pressure
-
Familiarity + abnormal requests
Each layer increases compliance while reducing suspicion.
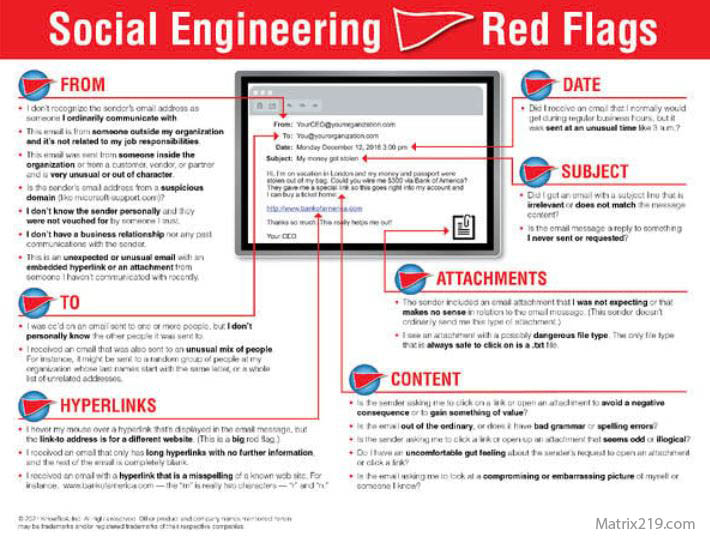
Social Engineering Red Flags
External Insight on Warning Signs
Security awareness research shows that most victims recall noticing something “felt off” only after the attack succeeded, a pattern supported by guidance from SANS Security Awareness Red Flags
Frequently Asked Questions (FAQ)
Are red flags always obvious?
No. Modern social engineering red flags are often subtle and designed to feel routine.
Is urgency always a sign of an attack?
Not always, but urgency combined with requests to bypass verification is a strong indicator.
Can experienced users still miss red flags?
Yes. Stress, workload, and familiarity reduce skepticism even in experienced professionals.
Should users challenge authority-based requests?
Yes. Legitimate organizations support verification, even for executives.
What is the best response to a suspected red flag?
Pause, verify through an independent channel, and report the interaction.
Conclusion
Common social engineering red flags are missed because they exploit trust, routine, and emotional response rather than technical flaws. Attackers design interactions to feel normal, not suspicious.
Learning to recognize these warning signs shifts defense from reaction to prevention. In social engineering, noticing small inconsistencies early often prevents major compromise later.





