Explore practical cybersecurity knowledge focused on protecting accounts, devices, and digital identities. This category covers ethical hacking concepts, privacy protection, social engineering awareness, and real-world security fixes to help individuals and businesses stay safe online.
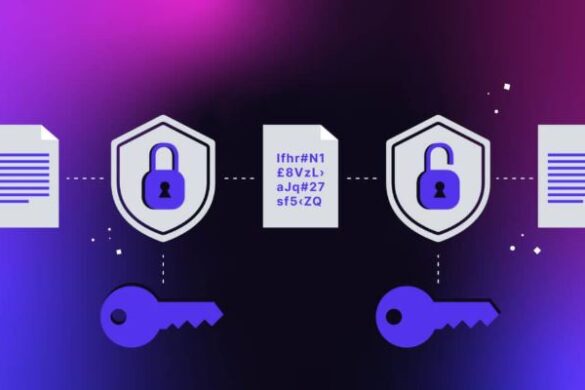
In today’s digital environment, protecting sensitive data is essential for ensuring privacy, security, and trust. As information is increasingly stored, transmitted, and processed electronically, it …