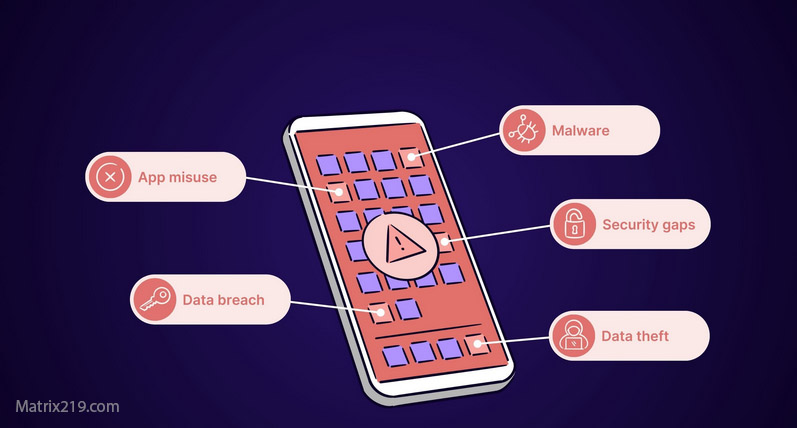
Sharing sensitive documents online without proper security measures can lead to data breaches, identity theft, or corporate espionage. Whether for business or personal purposes, protecting confidential files ensures privacy and compliance with legal requirements.
Common Risks of Sharing Documents Online
-
Unauthorized Access: Files may be intercepted by hackers or unauthorized users.
-
Data Leaks: Accidental sharing through email or public links.
-
Malware Threats: Files can be corrupted or compromised during transfer.
-
Compliance Violations: Mishandling sensitive information may breach regulations like GDPR or HIPAA.
Best Practices for Secure Document Sharing
1. Use Encrypted Platforms
Platforms like Tresorit, Sync.com, or Google Workspace with encryption enabled ensure that files are encrypted both during transfer and at rest.
2. Password-Protect Files
Apply strong, unique passwords to confidential documents, ensuring only authorized recipients can access them.
3. Enable Two-Factor Authentication (2FA)
2FA adds an extra security layer, requiring verification through email, SMS, or authentication apps before accessing shared documents.
4. Limit File Access
Set permissions such as view-only, restricted download, or expiration dates to control who can see or edit documents.
5. Use Secure File Transfer Methods
Avoid sending sensitive files via standard email. Consider secure cloud storage links or encrypted messaging platforms for safer delivery.
6. Regularly Audit Access
Review shared documents and revoke permissions when access is no longer needed to prevent data leaks.
Tools for Secure Document Sharing
-
Dropbox Business (with encryption enabled)
-
Microsoft OneDrive for Business (with sensitivity labels)
-
Box (enterprise security features)
-
Proton Drive (privacy-focused cloud storage)
-
Secure email services like ProtonMail or Tutanota
Conclusion
Securely sharing confidential documents online requires a combination of encrypted platforms, strong passwords, limited access permissions, and consistent monitoring. By following these best practices and using reliable tools, individuals and organizations can protect sensitive information from unauthorized access, maintain privacy, and comply with data protection regulations.