OAuth phishing is a new and increasingly dangerous form of phishing attacks that enables silent account takeover without stealing passwords. Unlike traditional phishing, OAuth phishing abuses legitimate authorization mechanisms to gain persistent access to user accounts.
Because OAuth phishing attacks rely on real consent screens and trusted platforms, victims often do not realize they have been compromised. This article explains what OAuth phishing is, how OAuth-based phishing attacks work, and why this technique is becoming one of the hardest phishing threats to detect.
Quick Navigation
What Is OAuth Phishing in Modern Phishing Attacks?
OAuth Phishing Definition Explained
OAuth phishing is a phishing attack where attackers trick users into granting access to malicious applications through OAuth authorization flows.
Instead of stealing credentials, OAuth phishing attacks:
-
Request app permissions
-
Abuse trusted login providers
-
Gain long-term account access
This approach builds on the phishing foundation explained in What Is Phishing? A Complete Beginner’s Guide
How OAuth Phishing Attacks Work Step by Step
OAuth-Based Phishing Attack Process Explained
A typical OAuth phishing attack follows this sequence:
-
The victim receives a phishing message
-
A link leads to a legitimate OAuth consent page
-
The user approves permissions
-
The attacker gains ongoing access
This process aligns with early manipulation stages of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Why OAuth Phishing Is Different From Traditional Phishing
OAuth Phishing vs Credential Phishing Attacks
Unlike credential phishing:
-
OAuth phishing does not steal passwords
-
OAuth phishing bypasses MFA
-
OAuth phishing grants persistent access
These differences make OAuth-based phishing far more subtle and dangerous.
Why OAuth Phishing Attacks Are So Hard to Detect
OAuth Phishing and Legitimate Authorization
OAuth phishing attacks appear legitimate because:
-
Login pages are real
-
Domains are trusted
-
Users knowingly approve access
This explains why OAuth phishing often bypasses security controls, as discussed in How Social Engineering Attacks Bypass Technical Security
OAuth Phishing and Multi-Factor Authentication
How OAuth Phishing Bypasses MFA
OAuth phishing bypasses MFA because:
-
MFA protects logins, not app permissions
-
OAuth tokens remain valid
-
No suspicious login occurs
This makes OAuth phishing a silent threat even in well-secured environments.
Common OAuth Phishing Attack Scenarios
OAuth Phishing Using Fake Productivity Apps
Attackers create fake apps that claim to:
-
Improve productivity
-
Integrate with email or calendars
-
Automate workflows
Once approved, these apps gain access without further interaction.
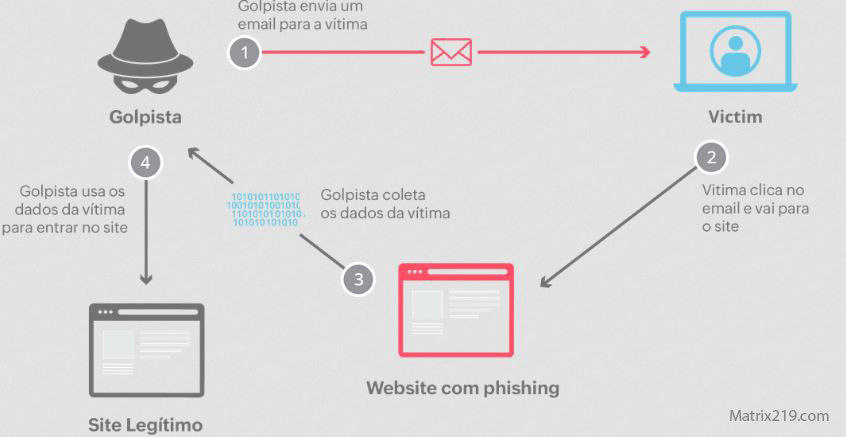
OAuth Phishing Through Email and Collaboration Tools
OAuth phishing attacks are often delivered via:
-
Email invitations
-
Shared document links
-
Collaboration platform messages
These delivery methods mirror patterns seen in Email Phishing Examples and How to Spot Them
Email Phishing Examples
Why OAuth Phishing Is Increasing Rapidly
Growth Factors Behind OAuth-Based Phishing Attacks
OAuth phishing is increasing because:
-
Cloud services rely heavily on OAuth
-
Users trust single sign-on flows
-
App permissions are poorly understood
This trend reflects how phishing adapts faster than defenses, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
OAuth Phishing Red Flags Users Miss
Warning Signs of OAuth Phishing Attacks
Common OAuth phishing red flags include:
-
Apps requesting excessive permissions
-
Unexpected consent prompts
-
Vague app descriptions
These subtle indicators are often overlooked.
How to Defend Against OAuth Phishing Attacks
Preventing OAuth-Based Phishing
Effective defense includes:
-
Reviewing app permissions regularly
-
Restricting third-party app access
-
Educating users about OAuth consent risks
-
Monitoring unusual API activity
Security must extend beyond passwords.
External Perspective on OAuth Phishing Risks
Cloud security guidance increasingly warns that OAuth abuse is a leading cause of account compromise, as emphasized in Google OAuth Security Guidance
Frequently Asked Questions (FAQ)
What is OAuth phishing in simple terms?
OAuth phishing tricks users into granting access to malicious apps instead of stealing passwords.
Can OAuth phishing bypass MFA?
Yes. OAuth phishing bypasses MFA because it abuses permission grants, not logins.
Are OAuth phishing attacks easy to spot?
No. They use legitimate consent screens and trusted platforms.
Can revoking passwords stop OAuth phishing?
No. Access persists until malicious app permissions are revoked.
Who is most at risk from OAuth phishing?
Users of cloud services and collaboration platforms.
Conclusion
OAuth phishing represents a shift in phishing attacks—from stealing credentials to abusing trust in authorization systems. By exploiting legitimate OAuth flows, attackers gain persistent, silent access that traditional security controls struggle to detect.
Understanding OAuth phishing is essential for defending modern cloud environments. In OAuth-based phishing, awareness of permissions matters as much as password security.