QR code phishing, also known as quishing, is a rapidly growing form of phishing attacks that exploits trust in QR codes. As QR codes become common for payments, menus, logins, and device pairing, attackers abuse this convenience to redirect victims to malicious destinations.
Quishing attacks bypass many traditional security controls because QR codes are scanned by phones, not analyzed by email filters or browsers. This article explains what QR code phishing is, how quishing attacks work, why they are increasing, and how users can recognize and avoid these threats.
Quick Navigation
What Is QR Code Phishing in Phishing Attacks?
QR Code Phishing Definition Explained
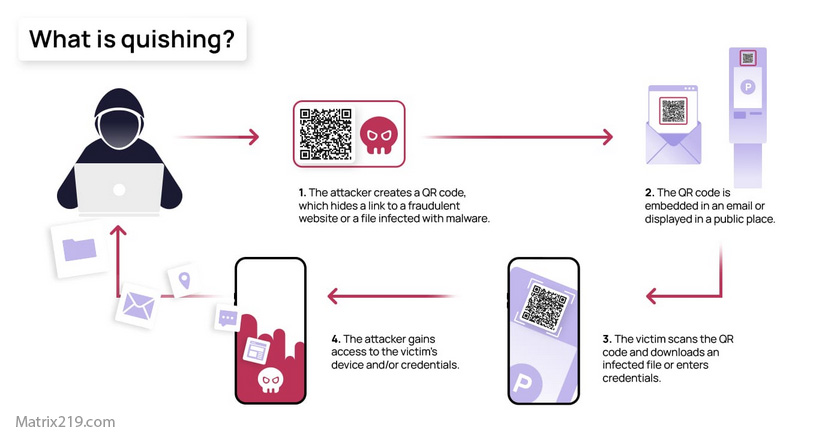
QR code phishing (quishing) is a phishing attack where attackers embed malicious links or actions inside QR codes.
In QR code phishing attacks, attackers:
-
Replace legitimate QR codes
-
Distribute fake QR codes
-
Redirect users to phishing websites
Instead of clicking a link, victims scan a code—lowering suspicion and speeding up compromise.
This definition builds on the phishing basics explained in What Is Phishing? A Complete Beginner’s Guide
How QR Code Phishing Attacks Work Step by Step
QR Code Phishing Attack Process Explained
A typical quishing attack follows this flow:
-
A QR code is placed or shared
-
The victim scans the QR code
-
A malicious link opens automatically
-
The victim is prompted to log in or act
This process mirrors early stages of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Common QR Code Phishing Attack Scenarios
QR Code Phishing in Public Places
Common quishing locations include:
-
Restaurants and cafés
-
Parking meters
-
Public transportation
-
Event posters
Attackers replace legitimate QR codes with malicious ones that look identical.
QR Code Phishing in Email and Messaging
QR code phishing attacks are also delivered through:
-
Email attachments
-
PDF documents
-
Messaging apps
This approach avoids traditional link inspection and aligns with patterns seen in Email Phishing Examples and How to Spot Them
Why QR Code Phishing Attacks Are Increasing
Why Quishing Attacks Are on the Rise
QR code phishing is increasing because:
-
QR codes feel safe and routine
-
Users cannot preview URLs easily
-
Mobile scanning bypasses many defenses
This explains why quishing adapts faster than technical controls, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
QR Code Phishing vs Traditional Phishing Attacks
Differences Between Quishing and Email Phishing
Compared to email phishing:
-
QR code phishing avoids clickable links
-
QR code phishing targets mobile devices
-
QR code phishing feels more trustworthy
These differences make quishing harder to detect.
How QR Code Phishing Attacks Bypass Security Controls
QR Code Phishing and Mobile Trust
QR code phishing bypasses security by:
-
Avoiding email and web filters
-
Using camera-based interaction
-
Triggering valid user actions
This aligns with how social engineering bypasses defenses, as explained in How Social Engineering Attacks Bypass Technical Security
QR Code Phishing Red Flags Users Miss
Warning Signs of Quishing Attacks
Common QR code phishing red flags include:
-
QR codes placed over existing ones
-
Requests to log in after scanning
-
QR codes found in unexpected locations
These subtle signs overlap with indicators discussed in Common Social Engineering Red Flags Most Users Miss
QR code phishing
What to Do If You Encounter a QR Code Phishing Attempt
How to Respond to QR Code Phishing Safely
If you suspect QR code phishing:
-
Do not scan the code
-
Avoid entering credentials
-
Verify the source independently
-
Report suspicious QR codes
Pausing prevents silent compromise.
External Perspective on QR Code Phishing Risks
Cybersecurity agencies increasingly warn that QR code phishing is being used to bypass traditional defenses, a trend highlighted in FBI QR Code Phishing Warnings
Frequently Asked Questions (FAQ)
What is quishing in simple terms?
Quishing is phishing that uses QR codes instead of clickable links.
Are QR code phishing attacks dangerous?
Yes. They can lead to credential theft, malware, or payment fraud.
Can security tools scan QR codes?
Some tools can, but many QR scans happen outside protected environments.
Are QR codes always unsafe?
No. But QR codes from unknown or altered sources are risky.
Who is most at risk from QR code phishing?
Mobile users and people who scan QR codes frequently.
Conclusion
QR code phishing shows how phishing attacks evolve with user behavior. By exploiting trust in QR codes and mobile convenience, quishing bypasses many traditional security checks and leads users directly to malicious destinations.
Understanding how QR code phishing works helps users slow down, verify sources, and avoid turning convenience into compromise. In quishing attacks, awareness before scanning is critical.





