Real-world social engineering examples help clarify how these attacks actually work outside of theory. While definitions and concepts are useful, seeing how attackers manipulate people in everyday situations makes the risk far more tangible.
Most social engineering attacks look ordinary at first glance. They rely on believable scenarios, familiar communication styles, and routine requests. This article explains real-world social engineering examples in simple terms, showing how attackers exploit trust and why victims often realize the attack only after damage occurs.
Quick Navigation
Real-World Social Engineering Example: Fake IT Support Email
Social Engineering Example Using Authority and Trust
An employee receives an email claiming to be from internal IT support. The message explains that a system update failed and requests a password reset to “restore access.”
Nothing technical is exploited. The employee complies because the request appears legitimate and urgent.
This scenario aligns directly with the definition outlined in What Is Social Engineering in Cybersecurity? (Updated Definition)
Real-World Social Engineering Example: Executive Impersonation
Social Engineering Example Targeting Authority Bias
An attacker impersonates a senior executive and emails a finance employee requesting an urgent transfer or sensitive document.
The message uses:
-
Familiar tone
-
Executive authority
-
Time pressure
This attack succeeds because employees are conditioned not to question leadership, a weakness explained in Why Humans Are the Weakest Link in Cybersecurity
Real-World Social Engineering Example: Phone-Based Support Scam
Social Engineering Example Using Voice and Urgency
A victim receives a phone call from someone claiming to be technical support. The caller warns of suspicious activity and instructs the victim to take immediate action.
The attacker relies on fear and urgency—two psychological triggers discussed in The Psychology Behind Social Engineering Attacks
Real-World Social Engineering Example: Social Media Profiling
Social Engineering Example Using Public Information
Attackers study a target’s social media to learn:
-
Job role
-
Colleagues’ names
-
Ongoing projects
They then craft a personalized message that feels familiar and credible. This technique reflects the reconnaissance stage of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
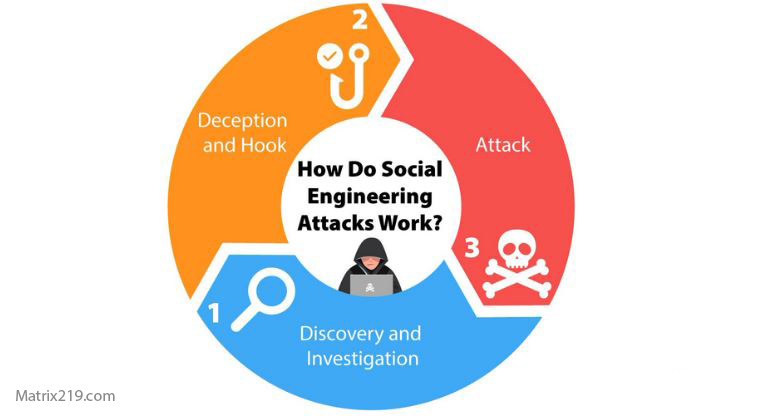
what is social engineering in cybersecurity
Real-World Social Engineering Example: Fake Vendor Communication
Social Engineering Example Breaking Normal Process
An attacker impersonates a known vendor and requests updated payment details. Because the request references real contracts and past interactions, it is approved without verification.
This attack demonstrates why social engineering often bypasses technical defenses more effectively than malware, as explained in Why Social Engineering Attacks Are More Effective Than Malware
Why These Social Engineering Examples Work
All real-world social engineering examples share common traits:
-
They feel routine
-
They exploit trust
-
They create urgency or authority
-
They avoid technical indicators
Victims believe they are following normal procedures, not making security mistakes.
How Social Engineering Examples Differ From Hacking Examples
In hacking examples:
-
Systems are exploited
-
Vulnerabilities are targeted
-
Tools leave technical traces
In social engineering examples:
-
Humans are manipulated
-
Actions are voluntary
-
Detection is delayed
This distinction is explored further in Social Engineering vs Hacking: What’s the Difference?
Lessons From Real-World Social Engineering Attacks
Key lessons include:
-
Verification matters more than intent
-
Familiarity does not equal legitimacy
-
Urgency should always trigger caution
Understanding these examples helps users recognize red flags discussed in Common Social Engineering Red Flags Most Users Miss
External Case-Based Perspective
Security awareness programs consistently use real-world examples to demonstrate how easily human behavior can be exploited, a practice supported by guidance from SANS Social Engineering Case Studies
Frequently Asked Questions (FAQ)
Are real-world social engineering attacks usually simple?
Yes. Most successful attacks rely on simple, believable scenarios rather than complex techniques.
Do these examples only apply to non-technical users?
No. Technical expertise does not prevent psychological manipulation.
Why don’t victims realize the attack immediately?
Because actions appear legitimate and align with routine behavior.
Can real-world examples improve security awareness?
Yes. Concrete examples are more effective than abstract rules.
Are these attacks increasing?
Yes. As technical defenses improve, attackers increasingly rely on human-based methods.
Conclusion
Real-world social engineering examples show that these attacks succeed not because victims are careless, but because attackers design interactions that feel normal and trustworthy. By exploiting routine behavior, authority, and urgency, social engineering bypasses security without triggering alarms.
Learning from real-world examples helps users recognize patterns early and respond before manipulation leads to compromise.





