Smishing attacks are a rapidly growing form of phishing attacks that use SMS messages instead of email. As users increasingly rely on mobile phones for banking, work, and authentication, attackers have shifted toward SMS-based phishing to exploit trust in text messages.
Smishing attacks feel personal, urgent, and legitimate. They often bypass email security controls entirely and reach victims directly on their phones. This article explains smishing attacks in clear terms, how SMS phishing works, why smishing is effective, and how users can recognize and stop these mobile-based phishing threats.
Quick Navigation
Smishing Attacks Explained in Simple Terms
What Are Smishing Attacks in Phishing?
Smishing attacks are phishing attacks delivered through SMS text messages.
In smishing attacks, attackers:
-
Pretend to be trusted organizations
-
Send urgent or alarming messages
-
Include links or phone numbers
The goal is to trick victims into clicking links, calling attackers, or sharing sensitive information.
This builds directly on the phishing concept explained in What Is Phishing? A Complete Beginner’s Guide
How SMS Phishing Attacks Work Step by Step
Smishing Attack Process Explained
A typical smishing attack follows this flow:
-
A text message claims a problem or reward
-
Urgency or fear is introduced
-
A link or number is provided
-
The victim reacts without verification
This mirrors early phases of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Common Smishing Attack Scenarios
Delivery and Account Smishing Attacks
Common SMS phishing messages include:
-
Package delivery issues
-
Bank account alerts
-
Payment confirmation warnings
These messages exploit routine mobile interactions and urgency.
Security Alert Smishing Attacks
Attackers send SMS messages claiming:
-
Account compromise
-
Suspicious activity
-
Verification failures
These fear-based smishing attacks rely on emotional triggers explained in The Role of Trust, Fear, and Urgency in Social Engineering
Why Smishing Attacks Are So Effective
Why SMS Phishing Works Better Than Email Phishing
Smishing attacks succeed because:
-
SMS messages feel personal
-
Users trust mobile notifications
-
Messages are read quickly
-
Verification is often skipped
This explains why smishing can outperform other phishing attacks, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
Smishing Attacks vs Email Phishing Attacks
Differences Between Smishing and Email Phishing
Compared to email phishing:
-
Smishing bypasses email filters
-
Smishing reaches users instantly
-
Smishing feels more urgent
These differences make SMS phishing harder to control using traditional tools.
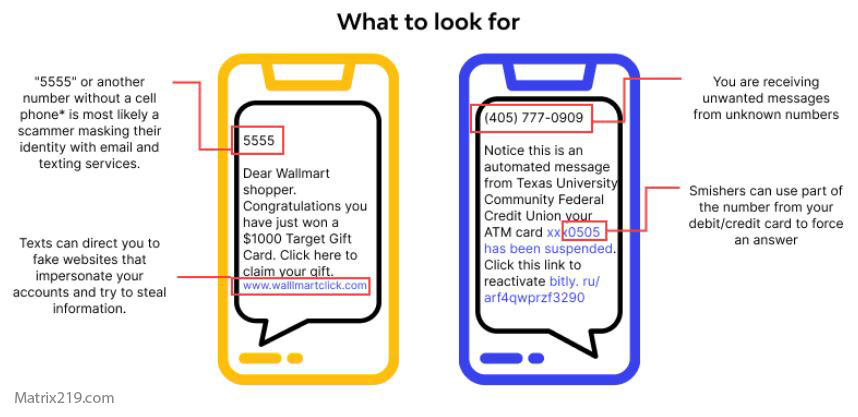
How Smishing Attacks Bypass Mobile Security
SMS Phishing and Mobile Trust
Smishing attacks bypass security by:
-
Using phone numbers instead of domains
-
Exploiting trust in telecom networks
-
Triggering valid user actions
This aligns with how social engineering bypasses technical controls, as explained in How Social Engineering Attacks Bypass Technical Security
Smishing Red Flags Users Often Miss
Warning Signs of Smishing Attacks
Users should be cautious of:
-
Unexpected SMS links
-
Requests for credentials or codes
-
Messages demanding immediate action
These red flags overlap with broader warning signs covered in Common Social Engineering Red Flags Most Users Miss
What to Do If You Receive a Smishing Message
How to Respond to SMS Phishing Attacks
If you suspect smishing:
-
Do not click links
-
Do not reply
-
Verify through official channels
-
Delete and report the message
Pausing breaks the attack flow.
External Perspective on Smishing Attacks
Consumer cybersecurity authorities consistently warn that SMS phishing is one of the fastest-growing phishing methods, as highlighted in FTC Smishing Warnings
Frequently Asked Questions (FAQ)
What is smishing in simple terms?
Smishing is phishing conducted through SMS text messages.
Are smishing attacks more dangerous than email phishing?
They can be, because users trust SMS and react faster.
Can phone security apps stop smishing?
They help, but they cannot prevent users from trusting messages.
Are smishing messages always obvious?
No. Many smishing messages look legitimate and routine.
Can anyone be targeted by smishing?
Yes. Anyone with a mobile phone can receive smishing attacks.
Conclusion
Smishing attacks show how phishing continues to evolve with user behavior. By exploiting trust in SMS messages and mobile urgency, attackers bypass traditional security and reach victims directly.
Understanding how smishing works helps users slow down, verify messages, and avoid reacting impulsively. In mobile-based phishing, awareness is the strongest defense.





