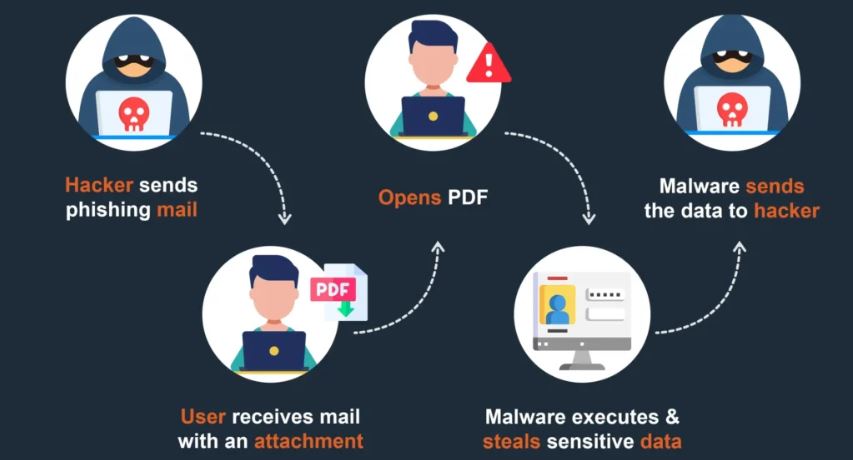
In the digital age, cyberattacks have become a significant threat to businesses of all sizes. Among the various attack vectors, social engineering stands out as one of the most effective methods used by cybercriminals, as it targets human behavior rather than technical vulnerabilities. This article examines real-world examples of social engineering attacks, their impact on organizations, and how businesses can reduce their exposure to these risks, as explained in Social Engineering: The Complete Guide to Human-Based Cyber Attacks.
Real-World Examples of Social Engineering Attacks
1. Twitter Hack (2020)
How It Happened:
Attackers used phone-based phishing, commonly known as vishing, to deceive Twitter employees into revealing login credentials. This method relied heavily on psychological pressure and trust manipulation techniques similar to those discussed in The Psychology Behind Social Engineering Attacks.
Impact:
Fraudulent cryptocurrency scam tweets were posted from high-profile accounts, leading to financial losses and severe reputational damage for Twitter.
2. Target Data Breach (2013)
How It Happened:
Attackers infiltrated a third-party HVAC vendor to gain initial network access and then used stolen credentials to move laterally into Target’s internal systems, a classic example of trust exploitation.
Impact:
Approximately 40 million credit card records were compromised, resulting in financial losses exceeding $18 million and long-term damage to consumer trust.
3. RSA Security Breach (2011)
How It Happened:
Employees received phishing emails containing malicious Excel attachments. Once opened, the malware provided attackers with access to sensitive security data, a technique commonly categorized under Phishing as a Social Engineering Technique.
Impact:
Compromised authentication data weakened RSA’s security products and harmed its reputation as a cybersecurity leader.
4. Sony Pictures Hack (2014)
How It Happened:
Attackers conducted targeted spear-phishing campaigns against Sony employees to steal login credentials and gain unauthorized access to confidential company data.
Impact:
Internal emails and unreleased movies were leaked, causing major financial losses and long-term reputational damage.
5. Crelan Bank Fraud (2016)
How It Happened:
Attackers executed a business email compromise (BEC) attack by impersonating the bank’s CEO and convincing an employee to authorize large financial transfers. This technique is closely related to account takeover scenarios discussed in Account Security and Recovery – How to Recover Hacked Accounts Legally.
Impact:
The bank lost approximately $75 million, and customer trust was significantly eroded.
Impact of Social Engineering Attacks on Organizations
Social engineering attacks can cause severe consequences for organizations, including:
-
Financial Losses: Direct theft, recovery costs, and regulatory fines.
-
Data Breaches: Exposure of sensitive corporate and customer information.
-
Reputational Damage: Loss of consumer and investor confidence.
-
Operational Disruptions: Business interruptions and increased security expenses.
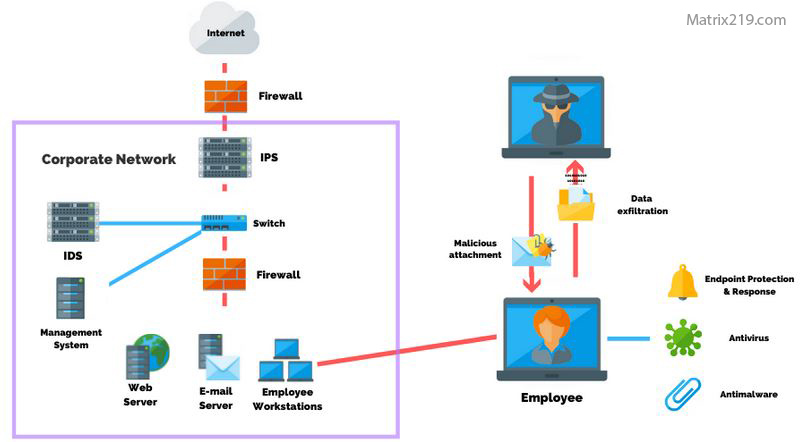
How Organizations Can Protect Themselves
1. Employee Awareness & Training
Organizations should conduct regular cybersecurity awareness programs and train employees to recognize phishing and manipulation tactics, as emphasized in Protection Against Social Engineering: A Comprehensive Guide for Individuals and Organizations.
2. Implement Strong Security Measures
Using two-factor authentication (2FA), intrusion detection systems, and endpoint protection tools significantly reduces attack success rates.
3. Limit Data Access
Applying the principle of least privilege helps minimize insider threats and reduces the impact of compromised accounts.
4. Behavioral Analysis Tools
AI-driven security solutions can detect unusual behavior patterns that may indicate social engineering attempts.
5. Incident Response Planning
Well-defined incident response plans enable organizations to contain damage quickly and recover from attacks efficiently.
Conclusion
Social engineering attacks highlight the human element as one of the weakest links in cybersecurity. Organizations that invest in employee training, layered security controls, and proactive monitoring are far better positioned to defend against these threats. Studying real-world cases allows businesses to anticipate attacker behavior and strengthen their defenses accordingly.
For additional background on the concept of social engineering, see Encyclopaedia Britannica – Social Engineering.