The social engineering attack lifecycle explains how attackers move from initial targeting to full compromise without exploiting technical vulnerabilities. These attacks are rarely random. Instead, they follow a structured process designed to manipulate human behavior at each stage.
Understanding this lifecycle helps individuals and organizations recognize attacks earlier and disrupt them before damage occurs. This article breaks down each phase of a social engineering attack, explains what happens at every step, and highlights where intervention is most effective.
Quick Navigation
Phase 1: Target Selection and Reconnaissance
Every social engineering attack begins with information gathering.
Attackers collect data such as:
-
Job roles and responsibilities
-
Organizational structure
-
Public email addresses
-
Social media activity
This profiling process enables attackers to craft believable scenarios, as further explored in How Attackers Profile Victims Using Public Information
Phase 2: Pretext Creation
A pretext is the story that makes the interaction feel legitimate.
Common pretexts include:
-
IT support requests
-
Urgent management instructions
-
Vendor or partner communications
The effectiveness of pretexts relies heavily on psychological manipulation discussed in The Psychology Behind Social Engineering Attacks
Phase 3: Initial Engagement
During engagement, attackers initiate contact through:
-
Email
-
Phone calls
-
Messaging platforms
-
Social media
At this stage, the goal is not immediate compromise but building trust and credibility.
This phase often overlaps with tactics explained in What Is Social Engineering in Cybersecurity? (Updated Definition)
Phase 4: Manipulation and Pressure
Once trust is established, attackers apply pressure.
Techniques include:
-
Creating urgency
-
Invoking authority
-
Introducing fear or consequences
This pressure reduces critical thinking and increases compliance, which explains why social engineering often outperforms malware, as shown in Why Social Engineering Attacks Are More Effective Than Malware
Phase 5: Exploitation and Action
In this phase, the victim performs the requested action, such as:
-
Sharing credentials
-
Clicking a malicious link
-
Approving access
-
Transferring sensitive information
At this point, technical defenses are bypassed entirely by human compliance.
Phase 6: Escalation and Persistence
After initial success, attackers may:
-
Expand access
-
Target additional users
-
Introduce malware for persistence
This phase connects social engineering with broader attack strategies and reinforces why humans are often described as the weakest layer in security, as discussed in Why Humans Are the Weakest Link in Cybersecurity
Phase 7: Exit or Cover-Up
Attackers may:
-
Disappear immediately after success
-
Maintain long-term access
-
Clean traces of interaction
Because actions appear legitimate, detection is often delayed.
Where Most Defenses Fail in the Lifecycle
Organizations often focus defenses on:
-
The exploitation phase
-
Malware detection
-
Network monitoring
However, the most effective disruption points are earlier stages:
-
Reconnaissance
-
Pretext validation
-
Engagement verification
Understanding the full lifecycle shifts defense from reaction to prevention.
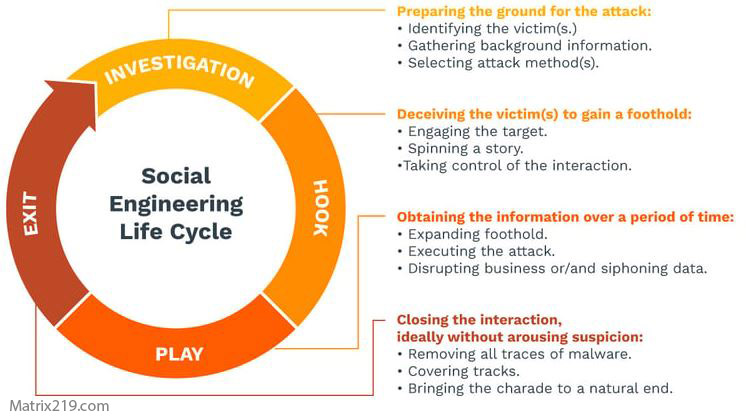
social engineering attack lifecycle
External Perspective on Attack Lifecycles
Security research consistently shows that social engineering attacks follow repeatable behavioral patterns, even when technical tools change, as reflected in MITRE ATT&CK Social Engineering Techniques
Frequently Asked Questions (FAQ)
Are social engineering attacks always planned?
Yes. Successful social engineering attacks rely on preparation and contextual awareness.
Which stage is most critical to stop an attack?
Early stages such as reconnaissance and pretext validation offer the best opportunity for prevention.
Can technical tools detect social engineering early?
Rarely. Early detection depends more on human awareness than automated systems.
Do all social engineering attacks follow this lifecycle?
Most do, although some stages may overlap or occur rapidly.
Why is detection often delayed?
Because actions appear legitimate and do not trigger technical alerts.
Conclusion
The social engineering attack lifecycle reveals why these attacks are so effective and difficult to stop. By manipulating behavior at each stage, attackers bypass technical defenses and rely on human compliance.
Understanding this lifecycle allows organizations to intervene earlier, reduce risk, and shift security efforts toward prevention rather than cleanup.





