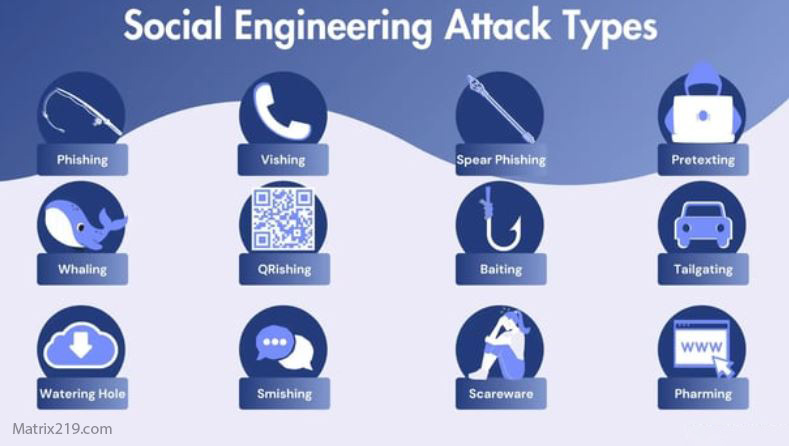
Social engineering attacks explained for non-technical users focus on one simple truth: you do not need technical knowledge to be targeted—or tricked—by a cyberattack. Many successful attacks do not involve hacking tools or complex software exploits. Instead, they rely on convincing people to take unsafe actions.
Non-technical users are often targeted because attackers know these users may not recognize manipulation tactics hidden inside everyday communication. This article explains social engineering attacks in simple terms, using clear examples and plain language to help non-technical users understand how these attacks work and how to spot them.
Quick Navigation
What Are Social Engineering Attacks for Non-Technical Users?
Social Engineering Attacks Explained Simply
Social engineering attacks are scams where attackers trick people into giving away information or access.
Instead of breaking into systems, attackers:
-
Pretend to be someone trustworthy
-
Create urgency or fear
-
Ask for information or action
This definition builds directly on the concept explained in What Is Social Engineering in Cybersecurity? (Updated Definition)
Why Non-Technical Users Are Targeted by Social Engineering
Social Engineering Attacks Target Human Behavior, Not Skills
Attackers target non-technical users because:
-
Trust is easier to exploit than software
-
Routine tasks reduce suspicion
-
Verification steps may be skipped
This is why humans are often described as the weakest security layer, as discussed in Why Humans Are the Weakest Link in Cybersecurity
Common Social Engineering Attacks Non-Technical Users Face
Email-Based Social Engineering Attacks
These attacks include:
-
Fake delivery notices
-
Account warning emails
-
Payment or invoice requests
They look legitimate and often imitate trusted brands.
Phone-Based Social Engineering Attacks
Attackers call pretending to be:
-
Bank representatives
-
Technical support
-
Government agencies
Fear and urgency are used to pressure victims, a tactic rooted in principles explained in The Psychology Behind Social Engineering Attacks
Social Media Social Engineering Attacks
Attackers use social media to:
-
Gather personal details
-
Build fake relationships
-
Send convincing messages
This approach mirrors the reconnaissance phase in the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Why Social Engineering Attacks Are Hard to Spot
Social Engineering Attacks Feel Normal
These attacks succeed because:
-
Messages look routine
-
Requests sound reasonable
-
Communication feels familiar
This explains why social engineering often works better than malware, as outlined in Why Social Engineering Attacks Are More Effective Than Malware
Simple Warning Signs Non-Technical Users Should Watch For
Social Engineering Red Flags Explained Simply
Non-technical users should be cautious when:
-
Asked to act urgently
-
Requested to share passwords or codes
-
Told to bypass normal steps
These warning signs are covered in detail in Common Social Engineering Red Flags Most Users Miss
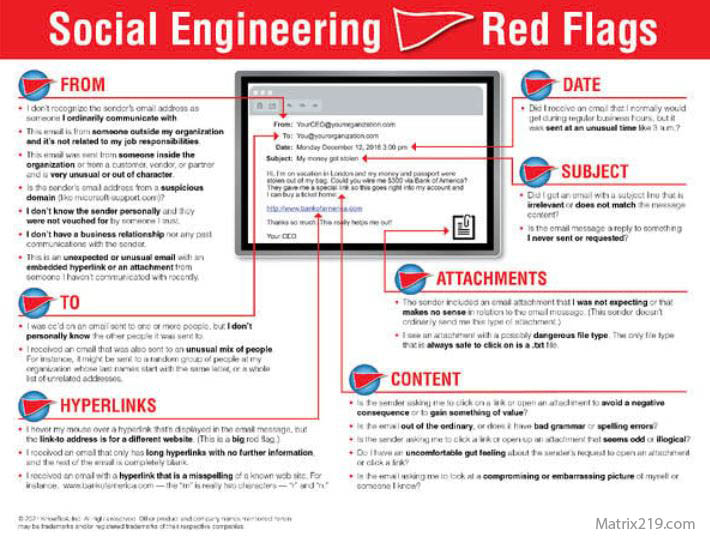
Social Engineering Red Flags
What Non-Technical Users Should Do When Unsure
If something feels off:
-
Pause and do not respond immediately
-
Verify the request through another channel
-
Ask someone else for confirmation
These simple steps stop many attacks before damage occurs.
Why Non-Technical Awareness Matters in Cybersecurity
Social Engineering Attacks Depend on Everyday Users
Organizations rely on non-technical users to:
-
Follow procedures
-
Handle sensitive information
-
Communicate externally
When attackers manipulate these users, technical defenses are bypassed entirely.
External Plain-Language Guidance
Consumer-focused cybersecurity guidance consistently emphasizes awareness and verification as the most effective defenses against social engineering, as reflected in FTC Consumer Scam Awareness
Frequently Asked Questions (FAQ)
Do I need technical knowledge to stop social engineering attacks?
No. Awareness and verification are more important than technical skills.
Are social engineering attacks only online?
No. They can occur via email, phone calls, text messages, or in person.
Why do attackers target regular users?
Because manipulating people is easier than breaking security systems.
What should I do if I think I was targeted?
Stop communication, verify the situation, and report it if possible.
Can anyone fall for social engineering?
Yes. These attacks exploit human behavior, not intelligence or experience.
Conclusion
Social engineering attacks explained for non-technical users reveal that cybersecurity is not just a technical issue—it is a human one. By manipulating trust, urgency, and routine behavior, attackers bypass defenses without touching systems.
Understanding how social engineering works empowers non-technical users to recognize manipulation early and respond safely. Awareness, not technical expertise, is the most effective defense.