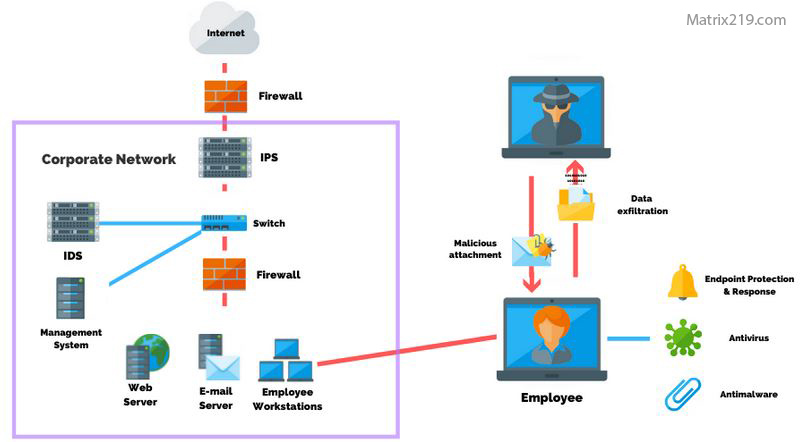
How social engineering attacks bypass technical security explains one of the most frustrating realities in cybersecurity: even the strongest technical defenses can be rendered useless by a single manipulated decision. Firewalls, endpoint protection, and access controls are designed to stop code—not people.
Social engineering attacks succeed because they operate outside the assumptions of technical security models. This article explains how social engineering attacks bypass technical security, why tools alone cannot stop them, and what this means for modern defense strategies.
Quick Navigation
How Social Engineering Attacks Bypass Technical Security Controls
Social Engineering Exploits Trust Instead of Vulnerabilities
Technical security controls are built to:
-
Block malicious code
-
Detect anomalies
-
Enforce access rules
Social engineering bypasses them by:
-
Gaining legitimate access
-
Triggering voluntary actions
-
Exploiting trusted users
This distinction builds on the core definition in What Is Social Engineering in Cybersecurity? (Updated Definition)
Why Technical Security Assumes Rational Behavior
Technical Security Models vs Human Behavior
Most security systems assume users will:
-
Verify requests
-
Follow procedures
-
Act rationally
Social engineering attacks exploit the gap between these assumptions and real human behavior, reinforcing why humans are considered the weakest link, as explained in Why Humans Are the Weakest Link in Cybersecurity
Legitimate Credentials: The Ultimate Security Bypass
Social Engineering Uses Valid Access, Not Exploits
When attackers obtain credentials through manipulation:
-
Authentication succeeds
-
Logs appear normal
-
Alerts are not triggered
This makes social engineering harder to detect than hacking, a difference explored in Social Engineering vs Hacking: What’s the Difference?
How Social Engineering Attacks Defeat Multi-Layered Security
Bypassing Layers Through Human Approval
Layered defenses fail when:
-
Users approve access
-
Employees authorize changes
-
Managers override controls
Attackers target the human approval layer because it overrides every technical layer beneath it.
Why Technical Tools Cannot Detect Social Engineering Easily
Social Engineering Looks Like Normal Activity
From a system perspective:
-
Emails look legitimate
-
Logins are valid
-
Actions follow policy
This explains why social engineering often succeeds more reliably than malware, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
How Social Engineering Fits Into the Attack Lifecycle
Social Engineering as the Entry Point
Social engineering often:
-
Gains initial access
-
Enables lateral movement
-
Prepares for technical exploitation
This progression follows the stages outlined in Social Engineering Attack Lifecycle: Step-by-Step Breakdown
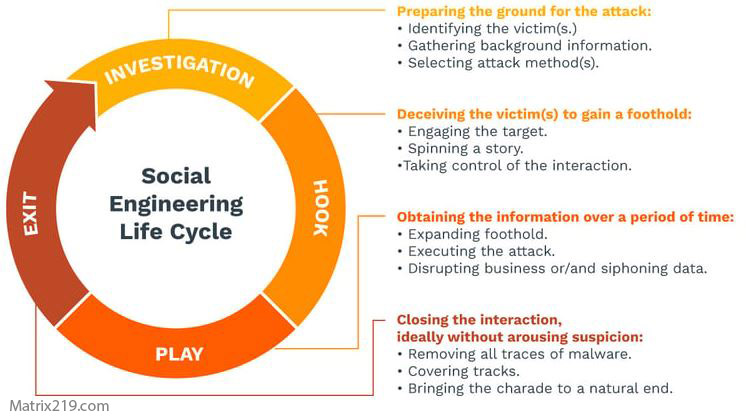
social engineering attack lifecycle
Examples of Technical Security Bypass via Social Engineering
Email Security Bypass
Even advanced email filters fail when:
-
Messages are personalized
-
Context appears legitimate
-
Victims trust the sender
Access Control Bypass
Access controls fail when:
-
Users share credentials
-
Approvals are manipulated
-
Verification is skipped
These examples mirror scenarios shown in Real-World Social Engineering Examples Explained Simply
Why Adding More Tools Doesn’t Solve the Problem
Tool Overload vs Human Behavior
More tools do not:
-
Reduce urgency pressure
-
Eliminate trust-based decisions
-
Stop emotional manipulation
Security improves only when systems expect human error.
Designing Security That Anticipates Social Engineering
Effective defenses include:
-
Mandatory out-of-band verification
-
Delayed approval workflows
-
Least-privilege access
-
Monitoring for unusual but valid behavior
This approach shifts focus from prevention to resilience.
External View on Human-Centered Security Failure
Security frameworks consistently emphasize that human manipulation remains a primary cause of security failure, a reality reflected in NIST Zero Trust Principles
Frequently Asked Questions (FAQ)
Can technical security fully stop social engineering attacks?
No. Technical controls cannot prevent users from being manipulated.
Why do social engineering attacks avoid detection?
Because actions appear legitimate and use valid credentials.
Is multi-factor authentication enough?
It helps, but attackers can still manipulate users into approving access.
Do social engineering attacks always lead to malware?
No. Many attacks succeed without deploying any malware.
What is the most effective defense against social engineering?
Designing systems that assume manipulation will occur and limit damage.
Conclusion
How social engineering attacks bypass technical security reveals a fundamental limitation of traditional defenses: they protect systems, not human decision-making. By exploiting trust, authority, and routine, attackers gain access that technology is designed to allow.
Modern cybersecurity must evolve beyond tools alone. True resilience comes from designing systems that expect human error and prevent a single manipulated decision from becoming a full-scale breach.