Social engineering has become the most reliable entry point for modern cyber attacks. Instead of breaking systems, attackers manipulate people—exploiting trust, urgency, authority, and routine to gain access that security tools are designed to allow.
In 2026, social engineering attacks are more adaptive, more personalized, and harder to detect than ever before. They operate across email, phone, messaging apps, video calls, and even workplace collaboration tools. This guide explains social engineering from the ground up, explores why it works, how attacks unfold, the risks involved, and how individuals and organizations can realistically defend against human-based cyber attacks.
This pillar article is designed as a reference hub—connecting concepts, examples, psychology, and defense strategies in one coherent framework.
Quick Navigation
What Is Social Engineering in Cybersecurity?
Social engineering is a class of cyber attacks that manipulate human behavior to gain unauthorized access, information, or actions.
Instead of exploiting software flaws, social engineering attacks:
-
Exploit trust and familiarity
-
Abuse authority and urgency
-
Leverage routine workflows
A full definition and breakdown is covered in What Is Social Engineering in Cybersecurity? (Updated Definition)
Why Social Engineering Attacks Are So Effective
Social engineering succeeds because humans are not security systems.
Attackers rely on:
-
Cognitive shortcuts
-
Emotional triggers
-
Time pressure
-
Social norms
These factors explain why social engineering often outperforms technical attacks, as explored in Why Social Engineering Attacks Are More Effective Than Malware
The Psychology Behind Social Engineering Attacks
At its core, social engineering is applied psychology.
Attackers intentionally trigger:
-
Trust (“This looks legitimate”)
-
Fear (“Your account is at risk”)
-
Urgency (“Act now”)
-
Authority (“This is from management”)
A deeper psychological breakdown is available in The Psychology Behind Social Engineering Attacks
The Social Engineering Attack Lifecycle
Most social engineering attacks follow a predictable lifecycle:
-
Reconnaissance and profiling
-
Initial contact
-
Trust-building or pressure
-
Action request
-
Exploitation or escalation
This full sequence is explained step-by-step in Social Engineering Attack Lifecycle: Step-by-Step Breakdown
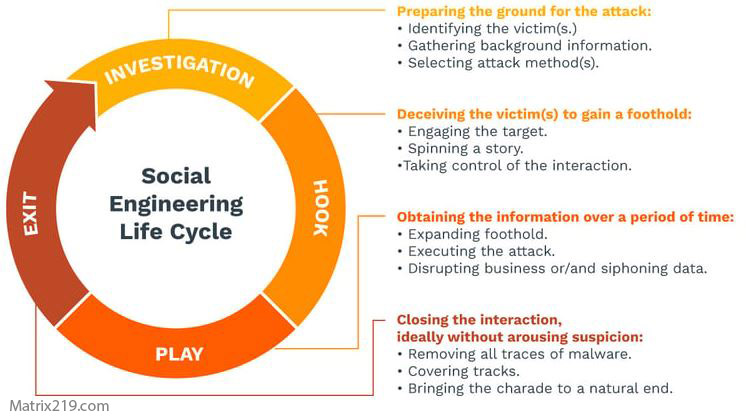
social engineering attack lifecycle
Common Social Engineering Red Flags Users Miss
Many attacks succeed because warning signs are subtle.
Commonly missed red flags include:
-
Slight deviations from normal process
-
Requests to bypass verification
-
Over-polished or overly contextual messages
These indicators are detailed in Common Social Engineering Red Flags Most Users Miss
Social Engineering vs Hacking: Key Differences
Social engineering and hacking are often confused but fundamentally different.
| Social Engineering | Hacking |
|---|---|
| Targets people | Targets systems |
| Uses deception | Uses exploits |
| Bypasses controls | Breaks controls |
A clearer comparison is covered in Social Engineering vs Hacking: What’s the Difference?
Why Humans Are the Weakest Link in Cybersecurity
Humans are the decision-makers security depends on.
This does not mean people are careless—it means:
-
They operate under pressure
-
They trust familiar context
-
They must act to keep work moving
This concept is expanded in Why Humans Are the Weakest Link in Cybersecurity
Real-World Social Engineering Examples
Social engineering appears in many everyday scenarios:
-
Fake account alerts
-
Executive impersonation
-
Support fraud
-
Credential harvesting
Clear, non-technical examples are explained in Real-World Social Engineering Examples Explained Simply
Social Engineering for Non-Technical Users
Social engineering does not require technical victims.
Attackers target:
-
Employees
-
Customers
-
Families
-
Executives
A plain-language explanation is available in Social Engineering Attacks Explained for Non-Technical Users
How Attackers Profile Victims
Profiling enables personalization.
Attackers gather data from:
-
Social media
-
Public records
-
Data leaks
-
Workplace information
This reconnaissance process is detailed in How Attackers Profile Victims Using Public Information
The Role of Trust, Fear, and Urgency
Emotional manipulation drives action.
Attackers intentionally create:
-
Fear of loss
-
Pressure to act
-
Illusion of authority
These mechanisms are explored in The Role of Trust, Fear, and Urgency in Social Engineering
Social Engineering in Remote and Hybrid Work
Remote work amplifies risk by:
-
Reducing face-to-face verification
-
Increasing digital trust
-
Normalizing urgent remote requests
This shift is examined in Social Engineering in the Age of Remote Work
How Social Media Fuels Social Engineering
Social platforms provide attackers with:
-
Context
-
Timing
-
Personal details
This amplification effect is covered in How Social Media Fuels Social Engineering Attacks
Social Engineering Threats Facing Organizations
Different sectors face different risks:
-
Small businesses
-
Enterprises
-
Government and public sector
Sector-specific risks are discussed in Social Engineering Threats Facing Small Businesses and Social Engineering in Government and Public Sector Attacks
Common Social Engineering Mistakes Employees Make
Mistakes usually stem from:
-
Assumptions
-
Speed over verification
-
Over-trusting digital identity
Common pitfalls are detailed in Most Common Social Engineering Mistakes Employees Make
How Social Engineering Bypasses Technical Security
Security tools are designed to allow legitimate actions.
Social engineering exploits this by:
-
Using valid credentials
-
Triggering approved workflows
-
Avoiding malware entirely
This bypass mechanism is explained in How Social Engineering Attacks Bypass Technical Security
How to Defend Against Social Engineering Attacks
Effective defense focuses on:
-
Verification over trust
-
Process over intuition
-
Limiting single-action impact
A strategy-focused breakdown is available in Critical Infrastructure Cyber Defense Strategies (conceptual defense principles apply across sectors)
External Reference on Social Engineering Risk
Human-based attacks remain the dominant initial access vector in modern breaches, a reality emphasized in Verizon Data Breach Investigations Report
Frequently Asked Questions (FAQ)
Is social engineering a technical attack?
No. It targets human behavior, not system vulnerabilities.
Can social engineering be fully prevented?
No. It can be mitigated and contained, not eliminated.
Are trained users immune?
No. Training reduces risk but does not remove manipulation.
Why is social engineering increasing?
Because it scales well and bypasses advanced defenses.
What is the most effective defense?
Mandatory verification and resilient process design.
Conclusion
Social engineering remains the most powerful cyber attack method because it exploits something no system can remove: human decision-making. In 2026, these attacks are more subtle, more contextual, and more integrated into everyday digital life.
Defending against social engineering requires a shift in mindset—from preventing every attack to designing systems that remain safe when manipulation succeeds. This guide serves as a foundation for understanding, detecting, and mitigating human-based cyber threats.





