Social engineering in government and public sector attacks poses unique and high-impact risks. Government agencies manage sensitive data, critical services, and public trust—making them attractive targets for attackers who exploit human behavior rather than technical weaknesses.
Public sector environments often involve complex hierarchies, rigid procedures, and time-critical decisions. Attackers take advantage of these characteristics to manipulate employees into bypassing safeguards. This article explains how social engineering targets government and public sector organizations, why these attacks are effective, and where defenses commonly fail.
Quick Navigation
Why Government and Public Sector Are Targeted by Social Engineering
Social Engineering Targets Authority and Process
Government environments emphasize:
-
Formal authority
-
Chain of command
-
Compliance with procedure
Attackers exploit these traits by impersonating officials or invoking regulatory urgency, reinforcing vulnerabilities discussed in The Role of Trust, Fear, and Urgency in Social Engineering
Common Social Engineering Attacks in Government Organizations
Phishing Attacks Against Government Employees
Government phishing attacks often involve:
-
Fake policy updates
-
Security alerts
-
Payroll or benefits changes
These messages appear legitimate and authoritative, aligning with techniques outlined in Why Social Engineering Attacks Are More Effective Than Malware
Impersonation of Officials and Agencies
Attackers impersonate:
-
Senior officials
-
Internal departments
-
External government agencies
Victims comply due to perceived authority, a weakness explained in Why Humans Are the Weakest Link in Cybersecurity
Vendor and Contractor Social Engineering
Government agencies rely heavily on contractors.
Attackers impersonate:
-
Service providers
-
Maintenance contractors
-
Technology vendors
This attack vector mirrors patterns discussed in Real-World Social Engineering Examples Explained Simply
How Bureaucracy Enables Social Engineering in Public Sector Attacks
Complex Processes Create Opportunity
Public sector procedures often involve:
-
Multiple approvals
-
Documentation overload
-
Slow verification
Attackers exploit procedural fatigue to push urgent requests through without scrutiny.
Why Social Engineering Detection Is Slower in Government
Delayed Response and Limited Visibility
Public sector organizations may face:
-
Legacy systems
-
Limited monitoring tools
-
Siloed departments
These factors delay detection, following the attack progression described in Social Engineering Attack Lifecycle: Step-by-Step Breakdown
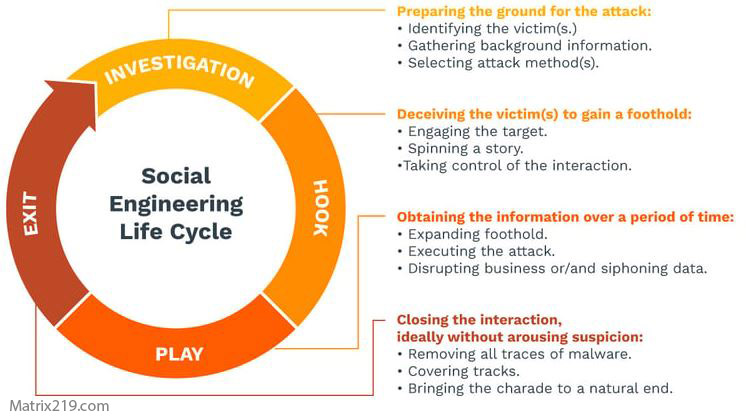
social engineering attack lifecycle
Impact of Social Engineering on Government and Public Trust
Social engineering attacks can lead to:
-
Data breaches involving citizen information
-
Disruption of public services
-
Loss of public confidence
Unlike private breaches, public sector incidents often carry national or societal consequences.
How Public Sector Culture Amplifies Social Engineering Risk
Government culture values:
-
Compliance
-
Procedure
-
Authority
Attackers manipulate these values to discourage questioning and verification.
Reducing Social Engineering Risk in Government Organizations
Effective mitigation includes:
-
Mandatory verification for sensitive requests
-
Clear escalation paths
-
Cross-department awareness training
-
Limiting public exposure of staff details
Security must account for human behavior, not just policy.
External Perspective on Government Social Engineering Risk
National cybersecurity authorities consistently warn that social engineering is a leading threat to public sector organizations, as emphasized in CISA Government Cybersecurity Guidance
Frequently Asked Questions (FAQ)
Why are government agencies attractive targets for social engineering?
Because they hold sensitive data, manage critical services, and rely heavily on authority-based processes.
Are government employees trained against social engineering?
Many are trained, but training alone does not eliminate manipulation risk.
Is social engineering harder to detect in the public sector?
Yes. Bureaucracy and legacy systems often delay detection and response.
Do these attacks affect public trust?
Yes. Public sector breaches undermine confidence in institutions and services.
Can government organizations reduce social engineering risk?
Yes. Verification, awareness, and process design significantly reduce exposure.
Conclusion
Social engineering in government and public sector attacks exploits authority, bureaucracy, and trust. Attackers manipulate procedural compliance to bypass safeguards without using technical exploits.
Understanding how social engineering targets public institutions is essential for protecting sensitive data and maintaining public trust. In the public sector, resilience depends on designing processes that expect manipulation—not perfect compliance.





