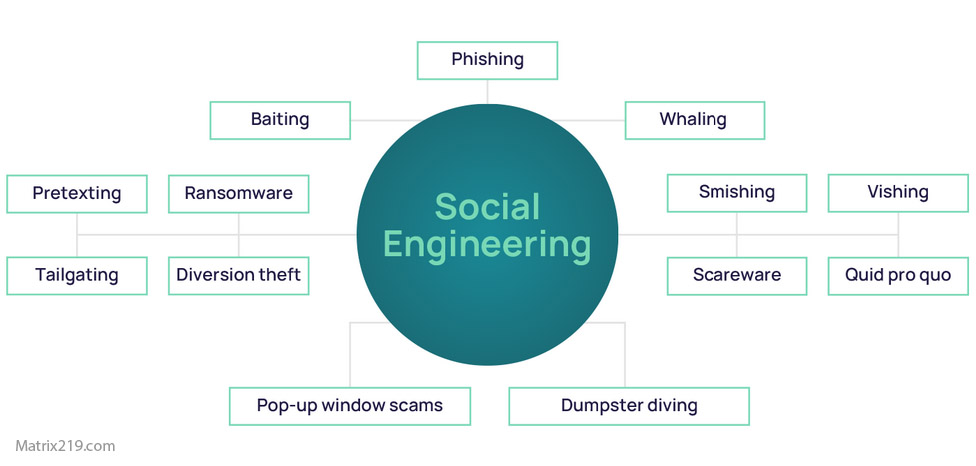
Most common social engineering mistakes employees make are rarely caused by carelessness. Instead, they result from routine behavior, time pressure, and misplaced trust. Attackers understand workplace dynamics and design social engineering attacks to exploit predictable employee responses.
Even well-trained employees can make critical mistakes when attacks feel legitimate or urgent. This article explains the most common social engineering mistakes employees make, why these errors occur, and how attackers turn small lapses into full-scale compromise.
Quick Navigation
Why Employees Make Social Engineering Mistakes
Social Engineering Exploits Normal Work Behavior
Employees are trained to:
-
Respond quickly
-
Help colleagues
-
Follow authority
-
Keep operations moving
Attackers exploit these norms, reinforcing why humans are often considered the weakest link, as discussed in Why Humans Are the Weakest Link in Cybersecurity
Common Social Engineering Mistake: Acting on Urgency
Urgency-Based Social Engineering Mistakes
Employees often act immediately when:
-
Deadlines are emphasized
-
Consequences are implied
-
Delays are discouraged
Urgency overrides verification and critical thinking, a tactic rooted in emotional manipulation explained in The Role of Trust, Fear, and Urgency in Social Engineering
Common Social Engineering Mistake: Trusting Authority Without Verification
Authority-Based Social Engineering Errors
Employees may comply with requests from:
-
Executives
-
IT staff
-
Managers
Attackers impersonate authority to discourage questioning, a technique common in Real-World Social Engineering Examples Explained Simply
Common Social Engineering Mistake: Bypassing Normal Procedures
Policy Bypass as a Social Engineering Weakness
Employees sometimes:
-
Skip approval steps
-
Ignore verification rules
-
“Make exceptions”
These shortcuts create openings during the manipulation phase of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Common Social Engineering Mistake: Sharing Too Much Information
Information Disclosure in Social Engineering Attacks
Employees may unintentionally share:
-
Internal processes
-
System details
-
Colleague information
This data helps attackers refine future attacks, reinforcing the importance of profiling discussed in How Attackers Profile Victims Using Public Information
Common Social Engineering Mistake: Assuming Familiarity Equals Safety
Familiar Communication as a Social Engineering Trap
Attackers mimic:
-
Writing styles
-
Names
-
Tools and platforms
Familiarity lowers suspicion and leads to trust-based errors.
Why Social Engineering Mistakes Are Hard to Prevent
Training vs Real-World Pressure
While training improves awareness:
-
Stress reduces recall
-
Habits override policy
-
Context influences decisions
This explains why social engineering often succeeds even in trained environments, as outlined in Why Social Engineering Attacks Are More Effective Than Malware
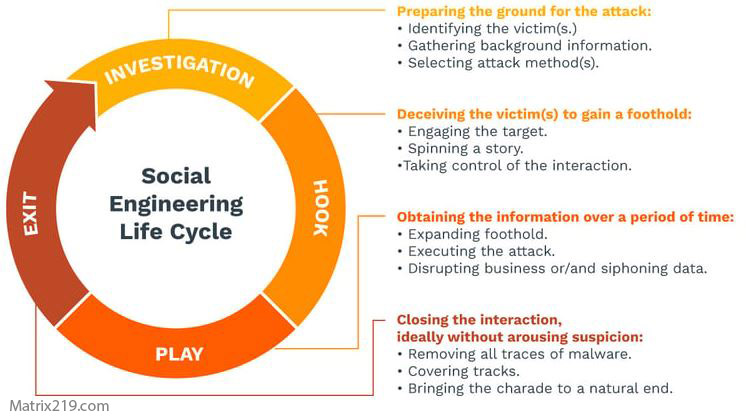
social engineering attack lifecycle
How Small Mistakes Escalate Into Major Incidents
One mistake can lead to:
-
Credential compromise
-
Unauthorized access
-
Financial loss
Once access is gained, attackers may escalate using technical methods or additional manipulation.
How Organizations Can Reduce Employee Mistakes
Effective measures include:
-
Mandatory verification for sensitive actions
-
Clear escalation paths
-
Slowing down high-risk decisions
-
Reinforcing “pause and verify” culture
Reducing reliance on perfect behavior improves resilience.
External Perspective on Employee Errors
Industry breach analysis consistently shows that employee actions are a leading factor in social engineering incidents, a trend highlighted in Verizon Human Error in Breaches
Frequently Asked Questions (FAQ)
Are employees to blame for social engineering attacks?
No. Attacks exploit human behavior, not negligence.
Can training stop all social engineering mistakes?
No. Training reduces risk but cannot eliminate manipulation under pressure.
What is the most common employee mistake?
Acting on urgency without verification.
Should employees always question authority-based requests?
Yes. Legitimate organizations support verification, even for senior staff.
How can organizations reduce employee-related risk?
By designing systems that assume mistakes will happen and limit their impact.
Conclusion
Most common social engineering mistakes employees make stem from trust, urgency, and routine—not ignorance. Attackers exploit these traits deliberately, turning normal workplace behavior into security vulnerabilities.
Reducing social engineering risk requires more than training. It requires designing processes that support verification, slow down risky actions, and protect employees from manipulation under pressure.