Why social engineering attacks are more effective than malware highlights a fundamental shift in modern cyber threats. While malware once dominated breach headlines, many of today’s most damaging incidents begin without malicious code. Instead, attackers manipulate people into granting access willingly.
This trend reflects patterns explored in Social Engineering: The Complete Guide to Human-Based Cyber Attacks (2026), where psychological manipulation consistently outperforms technical exploitation.
This article explains why social engineering outpaces malware-based attacks, how it bypasses technical defenses, and why organizations that focus only on malware detection remain exposed.
Quick Navigation
Social Engineering Targets Decisions, Not Systems
Malware attacks exploit technical flaws. Social engineering attacks influence human decisions.
This distinction matters because:
-
Systems can be patched
-
Humans must continue operating
-
Decisions are often made under pressure
When an action appears legitimate, security tools are designed to allow it. This principle is central to How Social Engineering Attacks Bypass Technical Security, where valid user actions become the attack vector.
Malware Depends on Exploitable Vulnerabilities
Malware effectiveness relies on:
-
Unpatched systems
-
Misconfigured software
-
Detectable malicious behavior
As defenses improve, malware becomes easier to identify, analyze, and neutralize. Social engineering, however, adapts to human behavior rather than system weakness—a contrast frequently discussed in Online Scams & Digital Fraud: How to Spot, Avoid, and Recover (2026 Guide).
Social Engineering Bypasses Security by Design
Most security controls are built to:
-
Accept valid credentials
-
Trust approved workflows
-
Avoid disrupting productivity
Social engineering exploits these assumptions by triggering actions that appear authorized. Once trust is established, technical defenses step aside.
This bypass mechanism reflects behavioral vulnerabilities detailed in The Psychology Behind Social Engineering Attacks, where authority, urgency, and familiarity override caution.
Human Behavior Is More Predictable Than Software
Software behavior changes with updates and patches. Human behavior remains relatively stable.
Attackers rely on:
-
Trust in authority
-
Desire to resolve issues quickly
-
Fear of negative consequences
-
Habitual workflows
These patterns are deeply ingrained and difficult to eliminate, making manipulation more reliable than exploitation.
Social Engineering Scales Without Technical Skill
Modern malware development requires specialized expertise. Social engineering does not.
Attackers can:
-
Reuse proven scripts
-
Adapt messaging rapidly
-
Target many victims simultaneously
This low barrier to entry increases attack volume, as demonstrated in AI-Driven Social Manipulation, where automation enhances scale without requiring advanced exploits.
Malware Creates Noise, Social Engineering Blends In
Malware often triggers:
-
Security alerts
-
Suspicious behavior logs
-
Forensic traces
Social engineering blends into normal communication:
-
Emails look routine
-
Requests sound reasonable
-
Actions feel familiar
This stealth advantage explains why many breaches go unnoticed until after damage occurs.
Why Malware Is Often a Secondary Stage
In many incidents, malware appears only after social engineering succeeds.
A common sequence includes:
-
Social engineering gains initial access
-
Credentials or approvals are obtained
-
Malware is deployed for persistence or impact
This progression mirrors the flow outlined in Social Engineering Attack Lifecycle: Step-by-Step Breakdown, where manipulation precedes technical compromise.
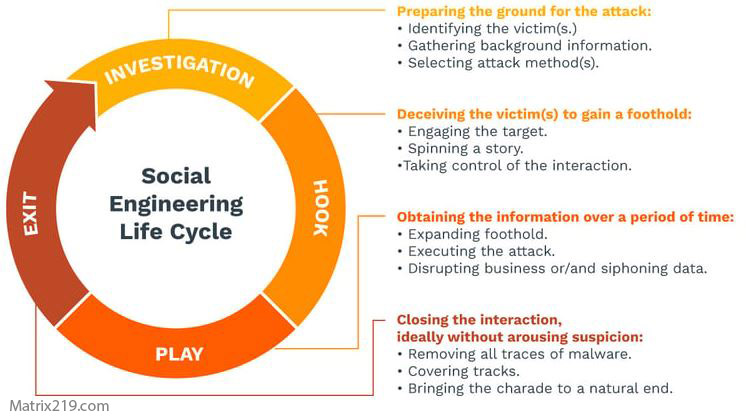
social engineering attack lifecycle
Social Engineering Works Across All Skill Levels
Technical expertise does not guarantee immunity.
Social engineering targets:
-
Authority structures
-
Contextual trust
-
Role-based access
Executives, IT staff, and non-technical users are all viable targets depending on their access and influence—an exposure frequently seen in Account Security and Recovery – How to Recover Hacked Accounts Legally.
Cost and Risk Favor Social Engineering
From an attacker’s perspective, social engineering is:
-
Cheaper to execute
-
Faster to adapt
-
Less risky to deploy
There is no exploit development, no malware analysis, and often no immediate forensic trail—advantages that make manipulation highly attractive.
Why Focusing Only on Malware Defense Fails
Organizations that prioritize malware prevention alone often miss:
-
Credential abuse
-
Impersonation attacks
-
Process manipulation
These gaps allow attackers to operate without triggering traditional security tools, reinforcing the need for behavioral defenses discussed in Digital Privacy and Online Tracking: How You’re Tracked Online and How to Protect Yourself (2026 Guide).
Frequently Asked Questions (FAQ)
Does this mean malware is no longer dangerous?
No. Malware remains harmful but is often deployed after social engineering succeeds.
Can antivirus stop social engineering attacks?
No. Antivirus tools are not designed to detect manipulation.
Are social engineering attacks easier to launch?
Yes. They require less technical skill and infrastructure.
Why do attackers prefer social engineering?
Because it bypasses defenses malware cannot.
What is the best defense against social engineering?
Verification-focused processes and user awareness.
Conclusion
Why social engineering attacks are more effective than malware becomes clear when examining how modern security operates. Malware fights systems. Social engineering exploits trust, routine, and human decision-making—areas technology is designed to accommodate, not block.
Defending against modern threats requires acknowledging that the most powerful attack vector is not code, but people—and building systems resilient to manipulation.
For official guidance on recognizing and reporting social engineering–based fraud, consult Federal Trade Commission (FTC) – Avoid Scams and Fraud.





