Social engineering in the age of remote work has become one of the fastest-growing cybersecurity risks. As organizations shifted to distributed teams, attackers adapted quickly—exploiting isolation, digital communication, and reduced verification to manipulate employees more easily than ever.
Remote work removed many informal security checks that existed in physical offices. Conversations moved to email, chat, and video calls, creating ideal conditions for impersonation and deception. This article explains how social engineering has evolved in the age of remote work, why remote employees are targeted, and which risks organizations often underestimate.
Quick Navigation
Why Remote Work Changed Social Engineering Attacks
Social Engineering Thrives in Remote Environments
Remote work environments:
-
Rely heavily on digital communication
-
Reduce face-to-face verification
-
Normalize urgent online requests
These changes expanded the human attack surface described in Social Engineering: The Complete Guide to Human-Based Cyber Attacks (2026)
Social Engineering Techniques Targeting Remote Workers
Impersonation Attacks in Remote Work
Attackers impersonate:
-
IT support staff
-
Managers or executives
-
HR or finance teams
Because remote employees expect digital requests, these attacks feel routine and legitimate. This mirrors patterns discussed in Real-World Social Engineering Examples Explained Simply
Remote Work Phishing and Messaging Attacks
Remote workers frequently receive:
-
Login verification messages
-
Tool access updates
-
Video meeting requests
These messages exploit urgency and familiarity—two triggers explained in The Role of Trust, Fear, and Urgency in Social Engineering
Why Remote Employees Are More Vulnerable to Social Engineering
Isolation Increases Social Engineering Risk
Remote employees often:
-
Cannot quickly verify requests in person
-
Feel pressure to respond quickly
-
Lack immediate peer confirmation
This isolation amplifies the human weaknesses discussed in Why Humans Are the Weakest Link in Cybersecurity
Blurred Work-Life Boundaries
Remote work blurs:
-
Work and personal devices
-
Office hours and personal time
-
Formal and informal communication
Attackers exploit this blur to strike when vigilance is lowest.
Social Engineering in Remote Work Communication Tools
Chat Platforms and Social Engineering
Messaging tools enable:
-
Fast impersonation
-
Short, urgent requests
-
Minimal context
Attackers use these tools to bypass traditional email security controls.
Video and Voice-Based Social Engineering
Remote work normalized video and voice calls.
Attackers now:
-
Fake urgent video requests
-
Use voice impersonation
-
Leverage reduced visual cues
These methods build on psychological manipulation discussed in The Psychology Behind Social Engineering Attacks
How Remote Work Changed the Social Engineering Attack Lifecycle
Remote work shortened the time between:
-
Initial contact
-
Trust establishment
-
Victim action
This accelerates the attack stages described in Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Why Technical Controls Struggle in Remote Work
Remote environments rely on:
-
User judgment
-
Digital trust
-
Self-verification
Technical tools cannot easily detect manipulation that appears as legitimate communication, reinforcing why social engineering often outperforms malware, as explained in Why Social Engineering Attacks Are More Effective Than Malware
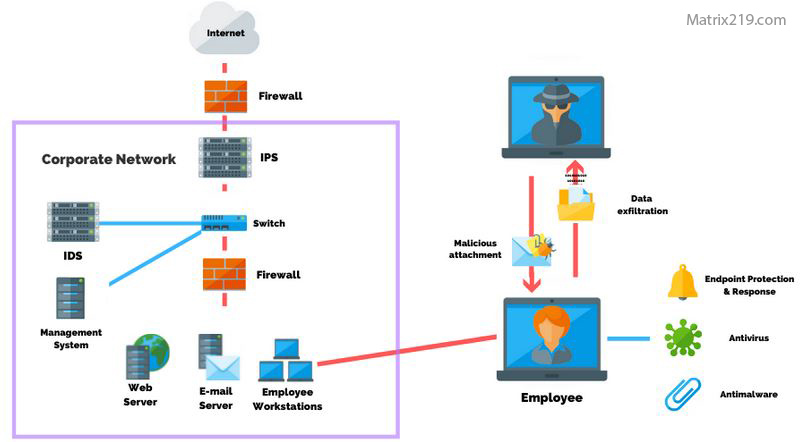
Why Social Engineering Attacks Are More Effective Than Malware
Reducing Social Engineering Risk in Remote Work
Effective mitigation includes:
-
Mandatory verification for sensitive requests
-
Clear escalation procedures
-
Delayed approval workflows
-
Security awareness tailored to remote scenarios
Designing security around human behavior matters more than adding tools.
External Perspective on Remote Work Risk
Cybersecurity authorities consistently warn that remote work environments increase exposure to human-based attacks, a trend highlighted in CISA Remote Work Security Guidance
Frequently Asked Questions (FAQ)
Why is social engineering more effective in remote work?
Because digital communication reduces verification and increases reliance on trust.
Are remote workers more at risk than office workers?
Yes. Isolation and lack of in-person confirmation increase vulnerability.
Do technical tools solve remote social engineering?
No. Tools help, but human judgment remains the primary target.
What is the biggest remote work red flag?
Urgent requests that bypass normal verification processes.
Can remote work be secure against social engineering?
Yes, if systems assume manipulation will occur and limit its impact.
Conclusion
Social engineering in the age of remote work exploits isolation, digital trust, and reduced verification. Attackers adapted faster than many organizations, shifting their focus squarely to remote employees.
Understanding how social engineering evolved with remote work is essential for building defenses that protect people—not just systems. In distributed environments, resilience depends on designing security that accounts for human behavior under remote conditions.





