Social engineering threats facing small businesses are increasing faster than many owners realize. Unlike large enterprises, small businesses often lack dedicated security teams, formal verification processes, and layered defenses—making them ideal targets for human-based attacks.
Attackers know that small businesses rely heavily on trust, speed, and informal communication. By exploiting these traits, social engineering allows attackers to bypass technical security with minimal effort. This article explains the most common social engineering threats facing small businesses, why they are targeted, and where risk is often underestimated.
Quick Navigation
Why Small Businesses Are Prime Targets for Social Engineering
Social Engineering Targets Operational Simplicity
Small businesses often operate with:
-
Fewer employees
-
Shared responsibilities
-
Informal approval processes
These conditions reduce verification and increase reliance on trust, reinforcing vulnerabilities discussed in Why Humans Are the Weakest Link in Cybersecurity
Common Social Engineering Threats Facing Small Businesses
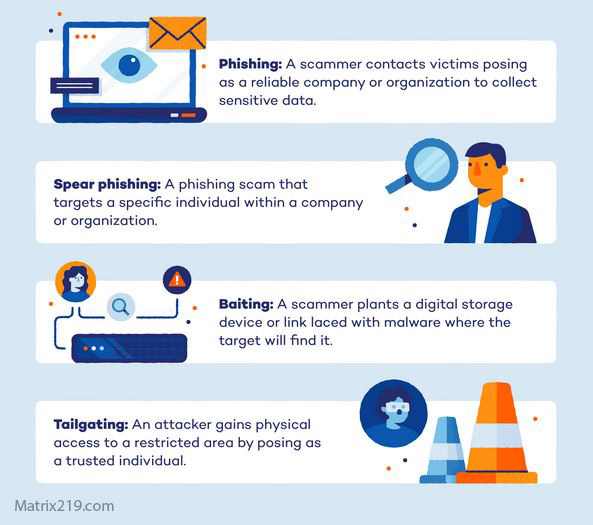
Phishing-Based Social Engineering Attacks on Small Businesses
Small businesses are frequently targeted with:
-
Fake invoices
-
Payment update requests
-
Account suspension emails
These attacks exploit urgency and routine tasks, patterns explained in Why Social Engineering Attacks Are More Effective Than Malware
Vendor and Supplier Impersonation Attacks
Attackers impersonate:
-
Payment processors
-
Service providers
-
Technology vendors
Because small businesses often work closely with vendors, these attacks feel legitimate and bypass scrutiny.
Executive Impersonation in Small Business Social Engineering
In small teams, leadership is easily recognizable.
Attackers impersonate:
-
Owners
-
Managers
-
Finance leads
This tactic mirrors authority-based manipulation discussed in The Role of Trust, Fear, and Urgency in Social Engineering
How Social Engineering Impacts Small Business Operations
Financial Loss From Social Engineering Attacks
Impacts include:
-
Unauthorized payments
-
Fraudulent transfers
-
Recovery costs
Even small losses can have outsized impact on smaller organizations.
Data and Reputation Damage
Social engineering may expose:
-
Customer data
-
Login credentials
-
Internal communication
Loss of trust can be more damaging than direct financial loss.
Why Small Businesses Detect Social Engineering Late
Lack of Formal Detection Processes
Small businesses often:
-
Lack monitoring tools
-
Rely on individuals to notice issues
-
Discover attacks after damage occurs
This delayed detection follows the pattern outlined in Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Lack of Formal Detection Processes
How Social Engineering Exploits Small Business Culture
Small business culture emphasizes:
-
Speed
-
Flexibility
-
Trust
Attackers exploit these values to push victims into acting quickly without verification.
Reducing Social Engineering Risk for Small Businesses
Practical defenses include:
-
Clear payment verification rules
-
Separation of duties where possible
-
Mandatory callbacks for sensitive requests
-
Awareness training focused on real scenarios
Security does not require enterprise-level complexity—it requires consistency.
External Guidance for Small Business Security
Cybersecurity agencies consistently warn that small businesses face disproportionate risk from social engineering, a concern highlighted in FTC Small Business Cybersecurity Guidance
Frequently Asked Questions (FAQ)
Why are small businesses targeted by social engineering?
Because they often lack formal security controls and rely heavily on trust-based processes.
Are small businesses more vulnerable than large enterprises?
Yes. Fewer resources and informal procedures increase risk.
Do attackers assume small businesses have less security?
Yes. Attackers view them as high-reward, low-effort targets.
Can small businesses afford social engineering defenses?
Yes. Simple verification and awareness measures are often enough to reduce risk significantly.
What is the biggest social engineering risk for small businesses?
Unauthorized payments and credential theft through impersonation.
Conclusion
Social engineering threats facing small businesses exploit trust, speed, and informal operations. Attackers deliberately target smaller organizations because human-based manipulation works where technical defenses are minimal.
Understanding these threats allows small businesses to implement simple, effective safeguards that prevent manipulation without disrupting operations. In social engineering defense, awareness and verification matter more than advanced tools.