Social engineering vs hacking is a comparison many users struggle to understand clearly. Both are associated with cybercrime, security breaches, and unauthorized access, yet they rely on fundamentally different methods. Confusing the two leads to misunderstanding how modern attacks actually happen and why traditional security defenses often fail.
While hacking targets systems and code, social engineering targets people and behavior. This article explains the difference between social engineering and hacking, how each attack works, where they overlap, and why social engineering is increasingly more dangerous in real-world scenarios.
Quick Navigation
Social Engineering vs Hacking: Core Definition Differences
What Is Social Engineering in Cybersecurity?
Social engineering in cybersecurity refers to attacks that manipulate human behavior to gain access or information. Instead of exploiting software flaws, attackers exploit trust, fear, urgency, or authority.
A full definition is covered in What Is Social Engineering in Cybersecurity? (Updated Definition)
What Is Hacking in Cybersecurity?
Hacking involves exploiting technical vulnerabilities in systems, applications, or networks. Hackers rely on:
-
Software bugs
-
Weak configurations
-
Unpatched systems
Hacking is primarily a technical discipline, even when used for malicious purposes.
Social Engineering vs Hacking: Attack Methods Compared
How Social Engineering Attacks Work
Social engineering attacks typically involve:
-
Phishing emails
-
Impersonation
-
Fake support requests
-
Psychological manipulation
These attacks succeed when victims willingly perform unsafe actions. This explains why they often bypass defenses, as detailed in Why Social Engineering Attacks Are More Effective Than Malware
How Hacking Attacks Work
Hacking attacks rely on:
-
Exploit development
-
Network scanning
-
Privilege escalation
-
Malware deployment
They require technical expertise and are more likely to be detected by security tools.
Social Engineering vs Hacking: Tools vs Psychology
Social Engineering Relies on Psychology, Not Tools
Social engineering uses:
-
Human emotions
-
Social norms
-
Behavioral bias
Attackers design scenarios that feel legitimate, exploiting psychological triggers explained in The Psychology Behind Social Engineering Attacks
Hacking Relies on Technical Tools and Exploits
Hacking depends on:
-
Scripts and frameworks
-
Vulnerability scanners
-
Exploit kits
Defenders can often block or detect these tools using security software.
Social Engineering vs Hacking: Detection and Prevention
Why Social Engineering Is Harder to Detect Than Hacking
Social engineering activity often looks like:
-
Normal communication
-
Legitimate logins
-
Approved actions
This makes detection slower and more difficult, especially compared to hacking attempts that generate technical indicators.
Why Hacking Is Easier to Monitor
Hacking usually leaves:
-
Log entries
-
Network anomalies
-
Malware artifacts
Security systems are designed to detect these signals.
Where Social Engineering and Hacking Overlap
In many real-world attacks:
-
Social engineering gains initial access
-
Hacking techniques expand control
This blended approach follows the lifecycle outlined in Social Engineering Attack Lifecycle: Step-by-Step Breakdown Social engineering opens the door; hacking walks through it.
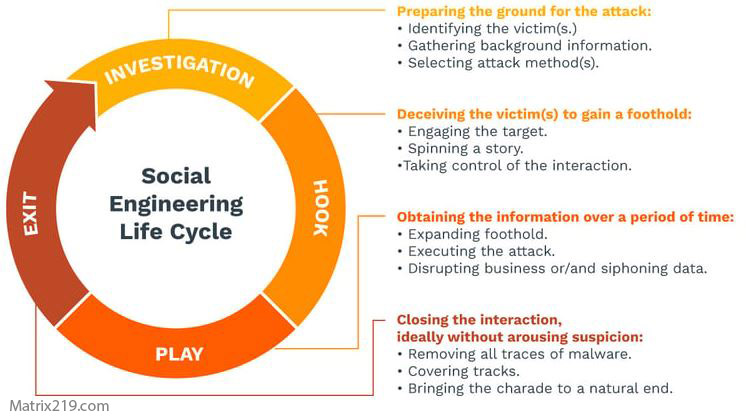
social engineering attack lifecycle
Social Engineering vs Hacking: Which Is More Dangerous?
Social engineering is often more dangerous because:
-
It bypasses technical defenses
-
It exploits trusted users
-
It scales easily
-
It is cheap to execute
This reinforces why humans are considered a primary risk factor, as discussed in Why Humans Are the Weakest Link in Cybersecurity
Real-World Examples: Social Engineering vs Hacking
Example of a Social Engineering Attack
An attacker impersonates IT support and convinces an employee to reset credentials. No malware is used, yet access is granted.
Example of a Hacking Attack
An attacker exploits an unpatched server vulnerability to gain unauthorized system access.
Both are attacks—but only one relies on code.
External Perspective on the Difference
Cybersecurity standards consistently distinguish between human-based attacks and technical exploitation, as reflected in guidance from NIST Cybersecurity Framework
Frequently Asked Questions (FAQ)
Is social engineering a type of hacking?
No. Social engineering manipulates people, while hacking exploits technical vulnerabilities, though both are cyberattacks.
Which is more common: social engineering or hacking?
Social engineering is more common today because it is easier, cheaper, and harder to detect.
Can hacking occur without social engineering?
Yes. Some attacks are purely technical, but many modern breaches combine both methods.
Do hackers use social engineering?
Yes. Many hackers use social engineering as the first step to gain access.
Which requires more skill?
Hacking requires technical skill; social engineering requires psychological understanding.
Conclusion
Social engineering vs hacking is not a debate about which is worse, but about how attacks actually succeed. Hacking targets systems, while social engineering targets human behavior. As technical defenses improve, attackers increasingly favor social engineering because it bypasses security by design.
Understanding the difference between social engineering and hacking is essential for building effective cybersecurity strategies that protect both systems and people.