How social media fuels social engineering attacks is no longer theoretical—it is one of the primary reasons these attacks succeed at scale. Social platforms encourage sharing, visibility, and interaction, all of which provide attackers with exactly what they need to manipulate people convincingly.
From professional profiles to personal posts, social media creates detailed behavioral maps that attackers use to personalize attacks. This article explains how social media fuels social engineering attacks, what information attackers extract, and why social platforms have become one of the most valuable tools in human-based cybercrime.
Quick Navigation
How Social Media Fuels Social Engineering Attacks Through Oversharing
Social Media Oversharing as a Social Engineering Enabler
Attackers monitor social media to collect:
-
Job roles and promotions
-
Team relationships
-
Travel plans and locations
-
Tools and platforms in use
This oversharing enables highly targeted manipulation and directly supports the profiling stage explained inHow Attackers Profile Victims Using Public Information
Social Media Trust Signals Used in Social Engineering
How Social Media Builds False Trust for Attackers
Social platforms display:
-
Mutual connections
-
Company affiliations
-
Public interactions
Attackers exploit these signals to appear legitimate and familiar. This trust-building tactic mirrors patterns seen in The Role of Trust, Fear, and Urgency in Social Engineering
Social Media and Impersonation Attacks
Social Engineering Impersonation Using Social Profiles
Attackers create fake profiles that:
-
Copy real photos and bios
-
Mimic colleagues or executives
-
Reference recent posts or events
These impersonation attacks feel authentic and are commonly seen in Real-World Social Engineering Examples Explained Simply
How Social Media Accelerates the Social Engineering Attack Lifecycle
Faster Reconnaissance and Engagement via Social Platforms
Social media shortens the time needed to:
-
Identify targets
-
Gather context
-
Initiate contact
This acceleration compresses the stages described in Social Engineering Attack Lifecycle: Step-by-Step Breakdown and increases attack efficiency.
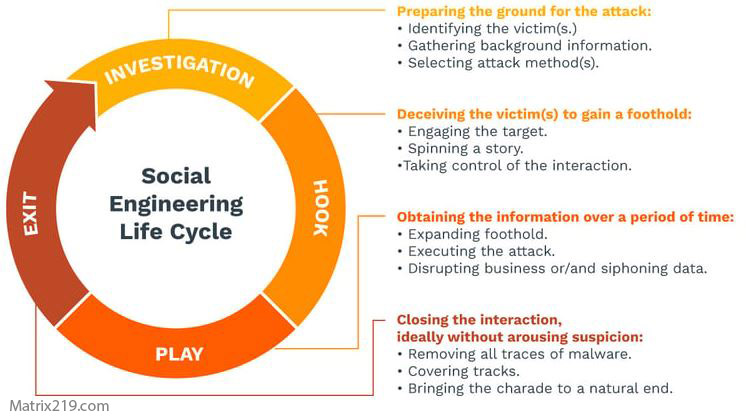
social engineering attack lifecycle
Why Social Media-Based Social Engineering Is Hard to Detect
Social Engineering Attacks Blended Into Normal Social Interaction
Social media attacks often:
-
Use personal messages
-
Occur outside corporate email
-
Bypass security monitoring
This makes detection difficult and explains why social engineering often bypasses tools designed to stop malware, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
The Psychological Impact of Social Media on Social Engineering
How Familiarity Lowers Suspicion
Frequent online interaction creates a false sense of familiarity.
Attackers exploit:
-
Informal tone
-
Repeated exposure
-
Shared interests
This psychological effect reinforces vulnerabilities discussed in The Psychology Behind Social Engineering Attacks
Social Media Risks for Individuals vs Organizations
Social Engineering Risk at the Individual Level
Individuals expose:
-
Personal habits
-
Emotional triggers
-
Daily routines
These details make attacks feel personal rather than random.
Social Engineering Risk at the Organizational Level
Organizations expose:
-
Employee roles
-
Internal relationships
-
Operational tools
This information enables attackers to target the right people with the right message.
How to Reduce Social Media–Driven Social Engineering Risk
Mitigation strategies include:
-
Limiting public profile details
-
Reviewing privacy settings regularly
-
Avoiding real-time location sharing
-
Verifying requests received via social platforms
Reducing exposure disrupts attacker preparation before contact occurs.
External Guidance on Social Media Security
Cybersecurity authorities consistently warn that social media is a major enabler of targeted social engineering, a risk emphasized in CISA Social Media Safety Guidance
Frequently Asked Questions (FAQ)
Why do attackers rely on social media for social engineering?
Because it provides real, trusted, and current information that makes attacks feel legitimate.
Are private social media accounts safe from profiling?
No. Even limited visibility can expose useful context and connections.
Can social engineering attacks happen entirely on social media?
Yes. Many attacks never move to email or corporate systems.
Does deleting social media prevent attacks?
No, but reducing public information lowers risk significantly.
Should organizations restrict employee social media use?
Education and awareness are more effective than strict restrictions.
Conclusion
How social media fuels social engineering attacks becomes clear when examining how much trust, context, and personal information these platforms expose. Social media turns ordinary sharing into a powerful attack resource.
Understanding this connection helps individuals and organizations reduce exposure and recognize why social platforms play such a central role in modern social engineering campaigns.





