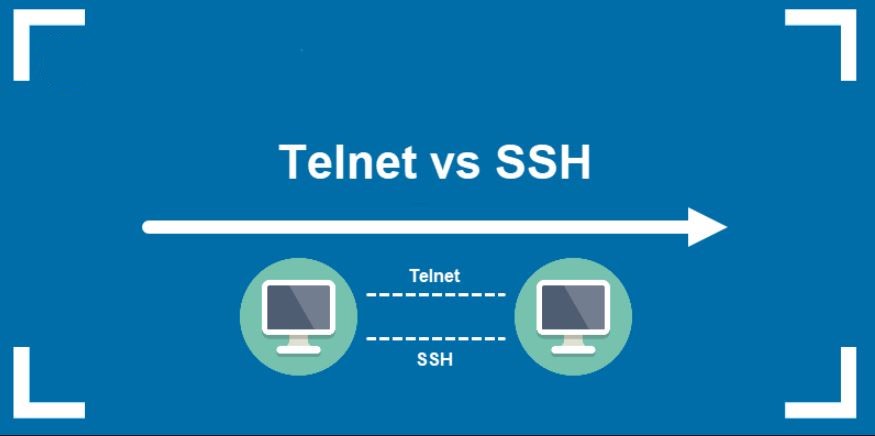
In networking and system administration, remote access is a fundamental requirement for managing servers, network devices, and services from a distance. Two commonly known technologies used for this purpose are SSH (Secure Shell) and Telnet. While both enable remote connections to systems, they differ substantially in terms of security, data protection, and practical use. This article examines what SSH and Telnet are, outlines their respective advantages and disadvantages, and highlights the key differences that make SSH the preferred choice in modern, security-focused environments.
What is SSH?
1. Definition
SSH (Secure Shell) is a secure communication protocol that encrypts data to establish a safe connection between two devices over a network. It is widely used for secure remote administration of servers.
2. Features of SSH
- Security – Uses encryption algorithms like RSA and DSA to protect data.
- Multi-functionality – Supports file transfer, command execution, and tunneling.
- Authentication – Uses password-based or public-private key authentication.
- Cross-Platform Compatibility – Works on Linux, Windows, and macOS.
3. Common Uses of SSH
- Remote server management.
- Secure file transfer via SCP or SFTP.
- Creating encrypted tunnels between devices.
What is Telnet?
1. Definition
Telnet is a text-based network protocol that allows remote access to a device without encryption. Users can execute commands as if they were physically present at the remote machine.
2. Features of Telnet
- Simplicity – Easy to use and requires minimal setup.
- Fast Performance – Lacks encryption, making it faster than SSH.
3. Drawbacks of Telnet
- Lack of Security – Data, including passwords, is transmitted in plain text.
- High Vulnerability – Hackers can easily intercept communication.
Key Differences Between SSH and Telnet
| Feature | SSH | Telnet |
|---|---|---|
| Security | Encrypted | Plain text transmission |
| Primary Use | Secure remote management | Simple text-based access |
| Encryption | Supported (RSA, DSA) | Not supported |
| Authentication | Passwords or encrypted keys | Plain-text passwords |
| Compatibility | Works on multiple OS | Works on multiple OS |
| Performance | Slightly slower due to encryption | Faster but insecure |
Why is SSH Preferred Over Telnet?
1. Security
SSH encrypts data, making it the go-to choice for secure remote access. Telnet, on the other hand, transmits data unencrypted, making it vulnerable to eavesdropping.
2. Flexibility
SSH supports file transfer, port forwarding, and tunneling, whereas Telnet only provides command execution.
3. Modern Standards
SSH aligns with current security standards, whereas Telnet is considered outdated and rarely used in modern systems.
Common Use Cases
SSH
- Managing remote servers securely.
- Secure file transfers using SCP or SFTP.
- Creating Virtual Private Networks (VPNs).
Telnet
- Used in controlled internal networks where security is not a concern.
- Educational and training environments for learning basic networking.
How to Use SSH?
1. Installing SSH
- Linux: Install OpenSSH via package manager.
- Windows: Use applications like PuTTY or PowerShell.
2. Connecting to a Remote Device
- Open a terminal.
- Enter the command:
ssh username@hostname - Enter your password to establish the connection.
Conclusion
Although SSH and Telnet are designed to achieve the same fundamental goal of remote system access, their underlying security models and practical capabilities differ greatly. SSH stands out as the superior solution because it encrypts data, protects credentials, and supports secure authentication mechanisms, making it suitable for modern networking and system administration environments. Telnet, by contrast, lacks built-in security and is therefore limited to controlled or legacy scenarios where risk is minimal. As a result, SSH has become the industry-standard protocol for managing remote systems in a safe, reliable, and efficient manner.
Source: Read the full article on Matrix219.Net