The role of trust, fear, and urgency in social engineering explains why these attacks succeed even when victims suspect something might be wrong. Social engineering does not rely on technical tricks alone—it relies on emotional pressure that shapes how people make decisions.
Attackers intentionally design messages and interactions to trigger trust, fear, or urgency because these emotions reduce critical thinking. This article explains how trust, fear, and urgency function in social engineering attacks, how attackers combine them, and why recognizing these triggers is essential for prevention.
Quick Navigation
Trust in Social Engineering Attacks
How Trust Is Exploited in Social Engineering
Trust is the foundation of most social interactions, making it a powerful attack surface.
Attackers build trust by:
-
Impersonating known individuals
-
Using familiar language and tone
-
Referencing real organizational details
Once trust is established, victims are far more likely to comply. This tactic aligns with the manipulation strategies discussed in The Psychology Behind Social Engineering Attacks
Fear as a Social Engineering Trigger
Why Fear Increases Compliance in Social Engineering
Fear pushes people to act quickly to avoid negative outcomes.
Common fear-based messages include:
-
Account suspension warnings
-
Security breach alerts
-
Legal or financial threats
When fear is triggered, rational evaluation decreases. This explains why fear-driven attacks often bypass defenses, as outlined in Why Social Engineering Attacks Are More Effective Than Malware
Urgency in Social Engineering Attacks
How Urgency Overrides Normal Verification
Urgency is one of the most effective social engineering tools.
Attackers use urgency to:
-
Prevent verification
-
Create pressure to act
-
Shorten decision time
Requests framed as “urgent” frequently appear during the manipulation phase of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
How Trust, Fear, and Urgency Work Together
Layered Emotional Manipulation in Social Engineering
Attackers rarely rely on a single emotion.
They often combine:
-
Trust + urgency (impersonated executive with a deadline)
-
Fear + urgency (account compromise warning)
-
Trust + fear (fake IT support reporting a breach)
This layered approach significantly increases success rates.
Why These Triggers Feel Legitimate
Social Engineering Mimics Real-Life Pressure
Trust, fear, and urgency are normal parts of real work environments.
Attackers exploit:
-
Busy schedules
-
Hierarchical structures
-
Crisis-response habits
This is why victims often realize the manipulation only afterward.\
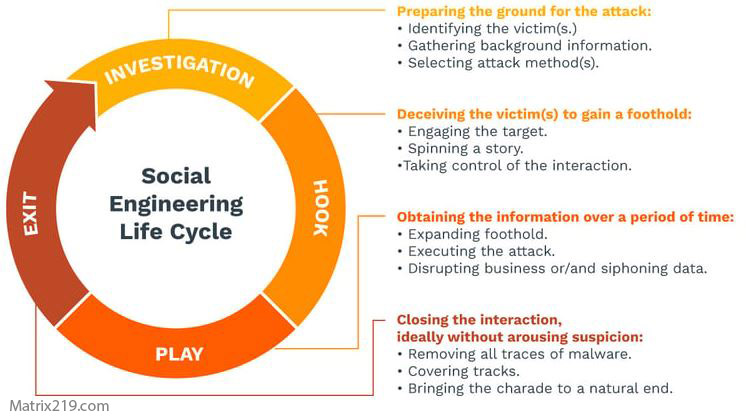
social engineering lifecycle
How Emotional Triggers Bypass Technical Controls
Technical systems cannot:
-
Evaluate emotional context
-
Detect psychological pressure
-
Stop voluntary actions
As a result, emotional manipulation bypasses defenses entirely, reinforcing the core definition in What Is Social Engineering in Cybersecurity? (Updated Definition)
Real-World Examples of Emotional Manipulation
Trust, fear, and urgency appear consistently in:
-
Fake executive requests
-
Account recovery scams
-
Vendor payment fraud
These scenarios are illustrated further in Real-World Social Engineering Examples Explained Simply
Why Humans Are Vulnerable to Emotional Triggers
Humans evolved to:
-
Trust authority
-
Respond to threats
-
Act quickly under pressure
Attackers exploit these traits deliberately, reinforcing why humans are considered the weakest link, as discussed in Why Humans Are the Weakest Link in Cybersecurity
How to Recognize Emotional Manipulation Early
Warning signs include:
-
Pressure to act immediately
-
Requests to bypass verification
-
Messages designed to provoke fear
Recognizing these signals early helps disrupt attacks before damage occurs.
External Behavioral Perspective
Behavioral science research confirms that emotional triggers significantly influence decision-making under pressure, a principle attackers exploit, as reflected in Behavioral Economics and Decision Bias Research
Frequently Asked Questions (FAQ)
Why are trust, fear, and urgency so effective in social engineering?
They reduce rational thinking and increase compliance under pressure.
Can awareness stop emotional manipulation?
Awareness helps, but systems must also support verification and delay.
Is urgency always a sign of an attack?
Not always, but urgency combined with requests to bypass normal steps is a strong warning sign.
Which emotion is most commonly used?
Urgency is the most frequent trigger, often combined with trust or fear.
Can technical tools detect emotional manipulation?
No. Emotional manipulation targets people, not systems.
Conclusion
The role of trust, fear, and urgency in social engineering explains why these attacks bypass even strong technical defenses. By manipulating emotional responses, attackers reduce skepticism and force quick decisions.
Understanding these emotional triggers helps individuals pause, verify, and resist manipulation. In social engineering, emotional awareness is just as important as technical security.