Vishing attacks, also known as voice phishing attacks, are rapidly increasing as attackers exploit trust in phone calls. While users have become more cautious with emails and links, many still trust voices—especially when calls sound urgent, authoritative, or professional.
Voice phishing scams bypass email filters, endpoint security, and many digital protections. By using phone calls, attackers directly manipulate human judgment in real time. This article explains vishing attacks, how voice phishing works, why vishing scams are on the rise, and how users can recognize and stop these attacks.
Quick Navigation
Vishing Attacks Explained in Simple Terms
What Are Vishing Attacks in Phishing?
Vishing attacks are phishing attacks conducted through phone calls.
In voice phishing attacks, attackers:
-
Impersonate trusted organizations
-
Use urgent or threatening language
-
Request sensitive information or actions
Unlike email phishing, vishing relies entirely on conversation and emotional pressure.
This definition extends the phishing concept explained in What Is Phishing? A Complete Beginner’s Guide
How Voice Phishing Attacks Work Step by Step
Vishing Attack Process Explained
A typical vishing attack follows these steps:
-
The attacker calls the victim
-
A trusted identity is impersonated
-
Urgency or fear is introduced
-
The victim is pressured to act immediately
This flow mirrors early stages of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Common Vishing Attack Scenarios
Bank and Financial Vishing Attacks
Common voice phishing scams include calls claiming:
-
Suspicious bank activity
-
Account verification issues
-
Fraud prevention actions
These calls exploit fear and authority.
IT Support Vishing Attacks
Attackers impersonate:
-
IT helpdesk staff
-
Security teams
-
Service providers
Victims are instructed to reset passwords or approve access. This tactic relies on trust-based manipulation explained in The Role of Trust, Fear, and Urgency in Social Engineering
Why Vishing Attacks Are Increasing
Why Voice Phishing Is on the Rise
Vishing attacks are increasing because:
-
People trust phone calls more than emails
-
Caller ID can be spoofed easily
-
Remote work normalized phone-based requests
This shift mirrors how social engineering adapts faster than technical defenses, as discussed in Why Social Engineering Attacks Are More Effective Than Malware
Vishing Attacks vs Other Phishing Attacks
Differences Between Vishing and Email or SMS Phishing
Compared to email or SMS phishing:
-
Vishing allows real-time manipulation
-
Vishing adapts instantly to victim responses
-
Vishing applies stronger emotional pressure
These traits make voice phishing harder to resist.
How Vishing Attacks Bypass Security Controls
Voice Phishing and Human Trust
Vishing attacks bypass security by:
-
Avoiding digital indicators
-
Using live conversation
-
Triggering voluntary disclosure
This aligns with how social engineering bypasses technical defenses, as explained in How Social Engineering Attacks Bypass Technical Security
Vishing Red Flags Users Often Ignore
Warning Signs of Voice Phishing Attacks
Common vishing red flags include:
-
Requests for passwords or codes
-
Pressure to act immediately
-
Threats of account suspension
-
Refusal to allow call-back verification
These signs overlap with broader warning signals discussed in Common Social Engineering Red Flags Most Users Miss
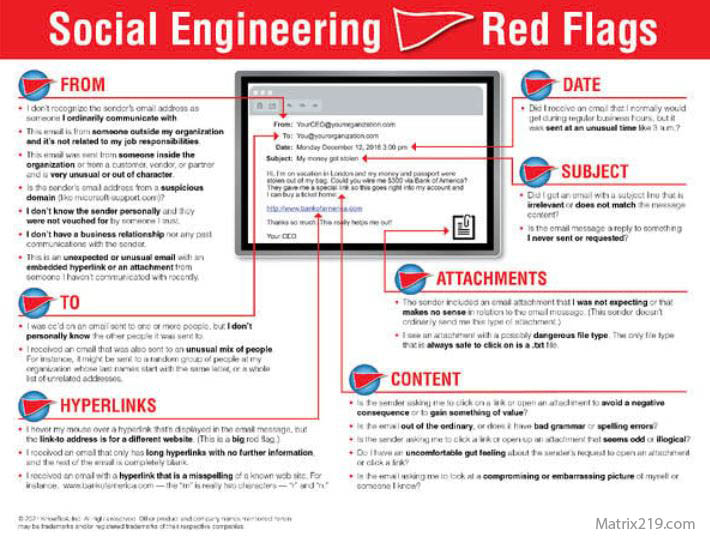
Vishing Red Flags
What to Do If You Receive a Vishing Call
How to Respond to Voice Phishing Safely
If you suspect a vishing attack:
-
Hang up immediately
-
Do not share information
-
Verify by calling the organization directly
-
Report the call if possible
Breaking the conversation breaks the attack.
External Perspective on Vishing Attacks
Consumer protection agencies consistently warn that voice phishing scams are rising and causing significant financial loss, as highlighted in FTC Voice Phishing Alerts
Frequently Asked Questions (FAQ)
What is vishing in simple terms?
Vishing is phishing conducted through phone calls.
Are vishing attacks more dangerous than email phishing?
They can be, because live conversation increases emotional pressure.
Can caller ID be trusted?
No. Caller ID can be spoofed easily by attackers.
Do legitimate organizations ask for passwords by phone?
No. Legitimate organizations do not request passwords or codes over calls.
Can anyone be targeted by vishing?
Yes. Anyone who answers phone calls can be targeted.
Conclusion
Vishing attacks demonstrate how phishing evolves with human behavior. By exploiting trust in voice communication and applying real-time pressure, attackers bypass technical security entirely.
Understanding how voice phishing works allows users to pause, verify, and disengage before manipulation leads to compromise. In vishing attacks, hanging up is often the safest defense.





