What is phishing is one of the most searched cybersecurity questions among beginners and non-technical users. Despite advanced security tools, phishing remains the most common entry point for cyberattacks because it targets people, not systems.
Phishing attacks trick users into revealing sensitive information, clicking malicious links, or approving unauthorized actions. These attacks look legitimate, routine, and urgent—making them difficult to recognize without proper understanding. This beginner’s guide explains what phishing is, how phishing attacks work, and why phishing continues to succeed despite growing awareness.
Quick Navigation
What Is Phishing in Cybersecurity?
Phishing Definition for Beginners
Phishing in cybersecurity is a type of social engineering attack where attackers impersonate trusted entities to trick victims into revealing information or taking unsafe actions.
Phishing attacks commonly aim to steal:
-
Login credentials
-
Financial information
-
Authentication codes
-
Personal data
This definition aligns directly with the broader concept explained in What Is Social Engineering in Cybersecurity? (Updated Definition)
How Phishing Attacks Work Step by Step
Phishing Attack Process Explained Simply
A typical phishing attack follows these steps:
-
The attacker sends a fake message
-
The message imitates a trusted source
-
Urgency or fear is introduced
-
The victim clicks, replies, or submits data
This process mirrors the early stages of the Social Engineering Attack Lifecycle: Step-by-Step Breakdown
Common Types of Phishing Attacks
Email Phishing Attacks Explained
Email phishing is the most common form of phishing.
These attacks often include:
-
Fake account alerts
-
Delivery or invoice notices
-
Security warnings
They succeed because they look routine and legitimate.
Phishing Attacks via SMS and Phone Calls
Phishing is not limited to email.
Attackers also use:
-
SMS phishing (smishing)
-
Voice phishing (vishing)
These methods exploit trust and urgency, psychological triggers explained in The Role of Trust, Fear, and Urgency in Social Engineering
Why Phishing Attacks Are So Effective
Why Phishing Works Better Than Technical Attacks
Phishing attacks succeed because:
-
They bypass technical defenses
-
They rely on human trust
-
They use legitimate communication channels
This explains why phishing often outperforms malware, a concept explored in Why Social Engineering Attacks Are More Effective Than Malware
Who Is Most Vulnerable to Phishing Attacks?
Phishing Targets Beginners and Experienced Users Alike
Phishing attacks target:
-
Non-technical users
-
Employees
-
Executives
-
Small business owners
Experience alone does not prevent phishing, reinforcing why humans are considered the weakest security layer, as explained in Why Humans Are the Weakest Link in Cybersecurity
How Phishing Attacks Bypass Security Tools
Phishing Uses Legitimate-Looking Behavior
Phishing attacks often:
-
Use real-looking domains
-
Avoid malware
-
Trigger valid logins
This allows them to bypass technical controls, as discussed in How Social Engineering Attacks Bypass Technical Security
Basic Phishing Warning Signs Beginners Should Know
Common Phishing Red Flags
Beginner users should be cautious of:
-
Urgent requests
-
Unexpected links
-
Requests for credentials
-
Pressure to act immediately
These red flags are covered in depth in Common Social Engineering Red Flags Most Users Miss
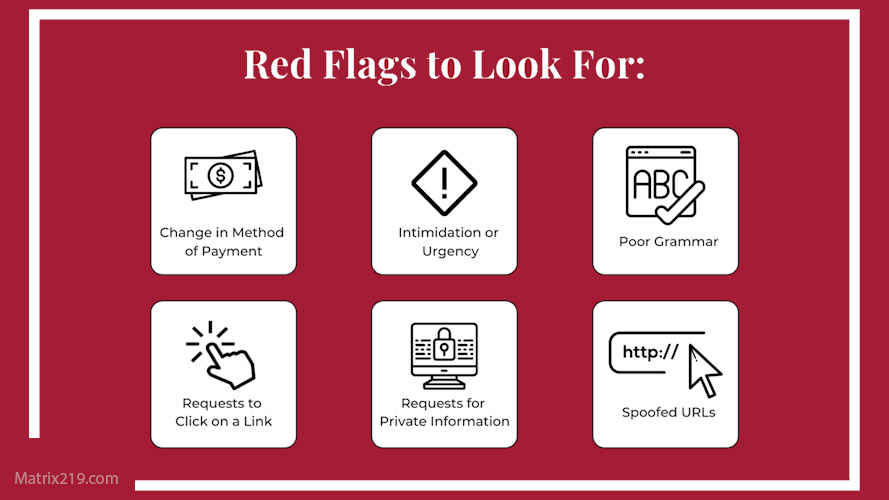
Phishing Red Flags
What Beginners Should Do If They Suspect Phishing
How to Respond to Suspected Phishing Attacks
If you suspect phishing:
-
Do not click links
-
Do not reply
-
Verify through another channel
-
Report the message
These simple steps stop many attacks early.
External Beginner-Friendly Guidance on Phishing
Global cybersecurity awareness initiatives consistently identify phishing as the leading threat to users, a reality highlighted in FTC Phishing Awareness
Frequently Asked Questions (FAQ)
What is phishing in simple terms?
Phishing is when attackers pretend to be trusted sources to trick you into giving information or clicking malicious links.
Is phishing the same as hacking?
No. Phishing manipulates people, while hacking exploits technical vulnerabilities.
Can antivirus stop phishing?
Antivirus helps, but it cannot prevent users from trusting fake messages.
Are phishing attacks illegal?
Yes. Phishing is commonly used in fraud and identity theft.
Can anyone fall for phishing?
Yes. Phishing exploits human behavior, not intelligence or experience.
Conclusion
What is phishing becomes clear when viewed as a human-focused attack rather than a technical one. By exploiting trust, urgency, and routine behavior, phishing bypasses defenses designed to stop malware and exploits.
Understanding phishing is the foundation for recognizing scams early and responding safely. Awareness—not tools alone—is the most effective defense against phishing attack.





