In today’s digital world, cyber threats are no longer limited to malicious software, complex hacking techniques, or technical vulnerabilities in computer systems. One of the most dangerous and underestimated forms of attack is social engineering. Unlike traditional hacking, which exploits weaknesses in systems or networks, social engineering exploits human psychology—our natural tendencies to trust, help, or comply with authority.
But what exactly is social engineering, how does it work, and why is it so effective? In this article, we will explore social engineering in detail, its types, techniques, real-world examples, and strategies to protect yourself and your organization.
What Is Social Engineering?
At its core, social engineering is the manipulation of people to gain unauthorized access to systems, networks, or sensitive information. Instead of breaking into computers, attackers trick individuals into handing over confidential data, granting access, or performing actions that compromise security.
Unlike technical attacks, social engineering exploits human emotions such as trust, fear, greed, curiosity, and urgency. Cybercriminals understand that humans are often the “weakest link” in security, and they use this weakness to their advantage.
Why Is Social Engineering Effective?
Exploiting Human Nature
Humans are social beings who rely on trust and cooperation. Attackers take advantage of this natural inclination to manipulate victims.
Psychological Triggers
Social engineers often use:
-
Authority (pretending to be a boss or government official)
-
Urgency (claiming immediate action is needed)
-
Scarcity (limited offers or threats of losing access)
-
Curiosity (enticing emails or links)
-
Fear (threatening consequences if the victim doesn’t comply)
Lack of Awareness
Many people underestimate the risks of social engineering. While most know about viruses or phishing, few understand how subtle manipulation can lead to massive breaches.
Types of Social Engineering Attacks
Phishing
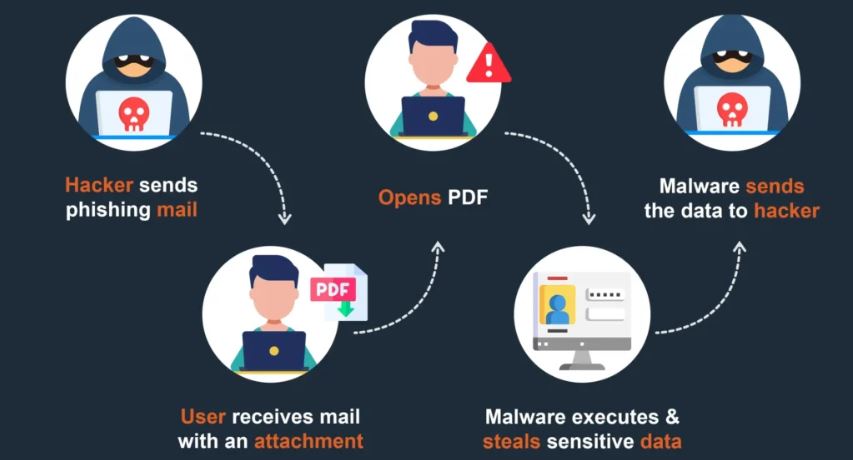
Phishing is the most common social engineering attack. It involves fraudulent emails, messages, or websites designed to trick victims into revealing sensitive information such as passwords or credit card numbers.
Spear Phishing
Unlike generic phishing, spear phishing targets specific individuals or organizations using personalized information. This makes it much more convincing.
Whaling
This is a specialized form of spear phishing targeting high-level executives or decision-makers. The goal is often financial fraud or access to highly sensitive information.
Pretexting
Pretexting involves creating a fabricated scenario to obtain information. For example, an attacker may impersonate an IT support agent and ask an employee for their login credentials.
Baiting
Baiting uses a tempting offer, such as free software, music, or a USB drive left in a public place, to lure victims into downloading malware or giving away information.
Quid Pro Quo
This technique involves offering something in exchange for information. For example, a fake IT technician might offer “free technical support” in exchange for login details.
Tailgating (Piggybacking)
Tailgating occurs when an attacker physically follows an authorized person into a restricted area, bypassing security measures.
Vishing (Voice Phishing)
Attackers use phone calls to trick victims into revealing information. They may impersonate bank employees, government agencies, or even family members.

Real-World Examples of Social Engineering
The Twitter Bitcoin Scam (2020)
Hackers compromised high-profile Twitter accounts—including those of Elon Musk, Bill Gates, and Barack Obama—through social engineering techniques. They convinced employees to provide credentials, leading to a massive cryptocurrency scam.
Target Data Breach (2013)
Attackers gained access to Target’s network by tricking a third-party vendor into revealing credentials. The breach exposed personal and financial data of over 40 million customers.
RSA Security Breach (2011)
An employee opened a malicious Excel file attached to a phishing email. This led to a compromise of RSA’s security products, impacting numerous organizations worldwide.
The Role of Social Engineering in Cybersecurity
Human Weakness as the Primary Target
While firewalls, encryption, and antivirus software protect systems, social engineering bypasses these defenses by targeting people directly.
The Cost of Social Engineering
According to cybersecurity reports, social engineering is one of the leading causes of data breaches, costing businesses billions annually.
How to Recognize Social Engineering Attempts
Suspicious Emails or Messages
Be cautious of messages with:
-
Urgent requests
-
Poor grammar or spelling
-
Suspicious links or attachments
Unusual Requests from Authority Figures
Always verify before complying with unusual requests from managers, CEOs, or government agencies.
Offers That Are Too Good to Be True
Free giveaways or unrealistic offers often hide malicious intent.
Requests for Sensitive Information
Legitimate companies never ask for passwords or personal data via email or phone.
How to Protect Yourself from Social Engineering
Education and Awareness
The most effective defense is knowledge. Regular training helps individuals recognize and resist manipulation attempts.
Multi-Factor Authentication (MFA)
Even if attackers steal credentials, MFA provides an additional layer of security.
Verification Protocols
Always confirm requests through secondary channels (e.g., call the person directly).
Secure Password Practices
Avoid reusing passwords and use strong, unique combinations.
Limiting Information Sharing
Be cautious about what you share on social media, as attackers often gather intelligence from public profiles.
Organizational Strategies Against Social Engineering
Security Training Programs
Companies should conduct regular awareness sessions and simulated phishing exercises.
Incident Response Plans
Employees should know how to report suspicious activity quickly.
Strict Access Controls
Limit access to sensitive data only to those who need it.
Encouraging a Security Culture
Organizations should promote a culture where questioning unusual requests is encouraged, not punished.
Future of Social Engineering
Use of Artificial Intelligence
Attackers are increasingly using AI to create more convincing phishing emails, voice deepfakes, and fake videos.
Deepfake Technology
Deepfakes allow attackers to impersonate trusted individuals through realistic audio or video.
Social Media Manipulation
Attackers exploit platforms like Facebook, LinkedIn, and Instagram to gather intelligence and launch attacks.
Conclusion
Social engineering is one of the most powerful tools in a cybercriminal’s arsenal. Unlike technical hacks, it preys on human emotions, trust, and habits. To defend against it, both individuals and organizations must prioritize awareness, training, and vigilance.
By understanding the tactics of social engineers and adopting strong security practices, we can reduce the risk of falling victim to manipulation. Remember: the human element is both the weakest link and the strongest defense in cybersecurity.