What is social engineering in cybersecurity is one of the most important questions for understanding modern cyber threats. While many security discussions focus on malware, exploits, and technical vulnerabilities, the majority of successful attacks today rely on manipulating people rather than systems.
Social engineering attacks bypass technical defenses by exploiting trust, urgency, fear, and authority. Instead of breaking into networks, attackers convince victims to open the door themselves. This makes social engineering especially dangerous in organizations with strong technical security but weak human awareness.
This article provides a clear, updated definition of social engineering in cybersecurity, explains how it works in practice, and shows why it remains one of the most effective attack methods in the digital world.
Quick Navigation
Social Engineering Definition in Cybersecurity
In cybersecurity, social engineering refers to attack techniques that manipulate individuals into performing actions or revealing information that compromises security.
These actions may include:
-
Sharing login credentials
-
Clicking malicious links
-
Approving unauthorized access
-
Disclosing confidential data
Unlike technical attacks, social engineering relies on deception disguised as legitimacy. Victims believe they are following normal procedures, not making security mistakes.
A broader strategic view of this threat is covered in Social Engineering: The Complete Guide to Human-Based Cyber Attacks (2026)
How Social Engineering Works in Practice
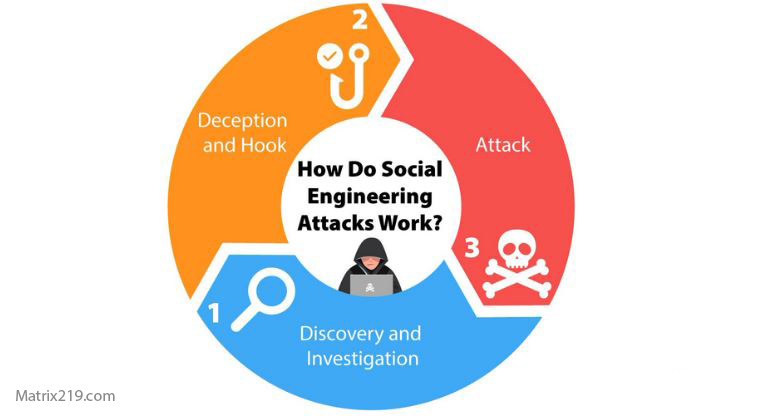
Most social engineering attacks follow a predictable pattern:
-
Reconnaissance – Studying the target’s role, habits, or environment
-
Engagement – Initiating contact using a believable scenario
-
Manipulation – Applying psychological pressure or emotional triggers
-
Compliance – The victim performs the requested action
This lifecycle explains why attackers prefer social engineering over complex exploits, as detailed in Why Social Engineering Attacks Are More Effective Than Malware
Social Engineering vs Traditional Cyber Attacks
Traditional cyber attacks focus on:
-
Vulnerable software
-
Misconfigured systems
-
Network exposure
Social engineering focuses on:
-
Human trust
-
Emotional reactions
-
Decision-making under pressure
Because the attack happens at the human layer, security tools often fail to detect it. This distinction is explored further in Social Engineering vs Hacking: What’s the Difference?
Why Social Engineering Is So Effective
Social engineering works because it exploits natural human behavior.
People are inclined to:
-
Trust authority figures
-
Respond quickly to urgent requests
-
Help colleagues or customers
-
Avoid appearing uncooperative
Attackers design scenarios that feel routine and legitimate, bypassing skepticism. This psychological dimension is examined in depth in The Psychology Behind Social Engineering Attacks
Common Forms of Social Engineering
Social engineering is not a single technique. It includes:
-
Phishing emails
-
Voice scams (vishing)
-
SMS scams (smishing)
-
Impersonation attacks
-
Pretexting and baiting
These methods all rely on manipulating perception rather than exploiting code. A simplified explanation for general audiences is available in Social Engineering Attacks Explained for Non-Technical Users
Is Social Engineering a New Threat?
Social engineering is older than computers.
Long before digital systems existed, attackers used:
-
Fake identities
-
Authority impersonation
-
Emotional manipulation
What changed is scale. Digital communication allows attackers to target thousands of victims instantly, increasing success rates and damage.
Who Is Vulnerable to Social Engineering?
No group is immune.
Common targets include:
-
Employees with system access
-
Executives and managers
-
Remote workers
-
Customer support staff
This reinforces why humans are often described as the weakest layer in security, a concept expanded in Why Humans Are the Weakest Link in Cybersecurity
Why Social Engineering Is a Cybersecurity Priority
Organizations prioritize social engineering defense because:
-
Human error is a leading cause of breaches
-
Technical controls cannot stop deception
-
Attacks are low-cost and scalable
-
Detection often happens after compromise
Industry-wide recognition of this threat is reflected in authoritative cybersecurity frameworks such as NIST Social Engineering
Frequently Asked Questions (FAQ)
What is social engineering in simple terms?
Social engineering is when attackers trick people into giving up access or information instead of hacking systems directly.
Is social engineering considered hacking?
It is different from traditional hacking. Social engineering relies on manipulation rather than technical exploitation, but it is still a cyberattack.
Why do social engineering attacks succeed so often?
They exploit trust, urgency, and fear—human traits that security tools cannot fully control.
Can antivirus software stop social engineering?
No. Antivirus tools can block malware, but they cannot prevent someone from making a harmful decision.
Is social engineering illegal?
Yes. Social engineering is commonly used in fraud, identity theft, and unauthorized access, which are illegal activities.
Can training eliminate social engineering risk?
Training reduces risk but does not eliminate it. Continuous awareness and reinforcement are required.
Conclusion
Social engineering in cybersecurity is the practice of exploiting human behavior to bypass security controls. By manipulating trust and emotion, attackers succeed without breaking systems or defeating technical defenses.
Understanding what social engineering is—and how it works—is the foundation for recognizing attacks and reducing risk. As long as humans remain part of security processes, social engineering will remain a critical threat.