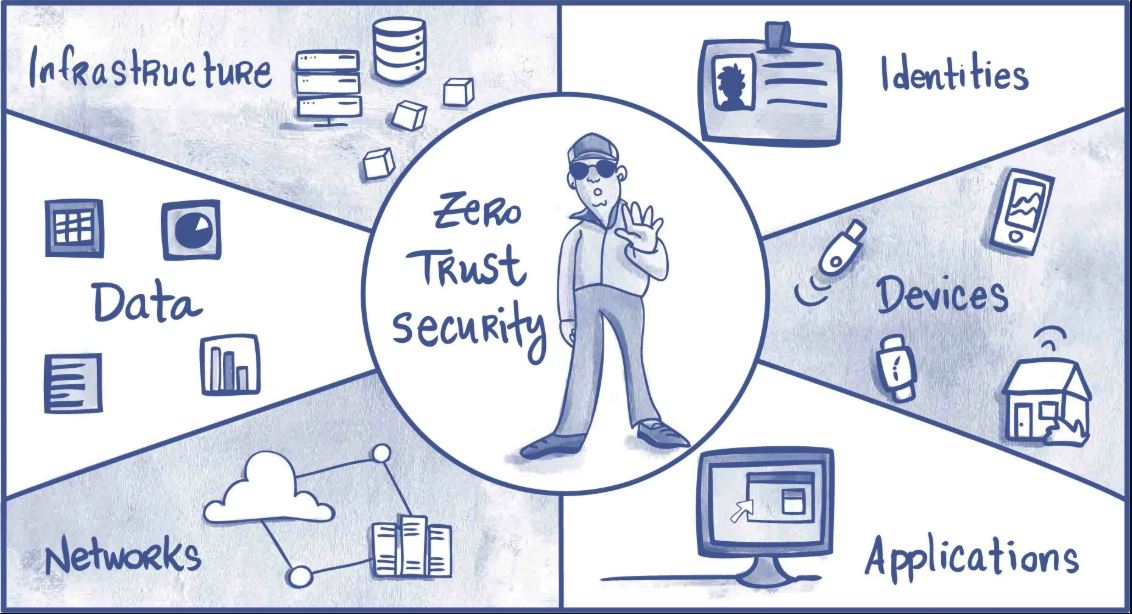
Zero Trust Architecture (ZTA) is a modern cybersecurity strategy that operates on the core principle of “never trust, always verify.” It eliminates the idea of a trusted internal network and an untrusted external network. Instead, it assumes that threats exist both inside and outside the network and therefore requires strict identity verification for every person and device trying to access resources, regardless of their location.
The Old Model vs. The Zero Trust Model
For decades, network security followed the “castle-and-moat” approach. You had a strong perimeter (the moat) with firewalls and other defenses, but anything inside that perimeter was generally trusted. The problem is, once an attacker breaches the perimeter, they can move freely inside the network.
Zero Trust assumes the attacker is already inside. It gets rid of the trusted internal network concept and puts up secure checkpoints around every single resource (like applications, files, and databases).
Core Principles of Zero Trust
A Zero Trust model is built on three main ideas:
1. Verify Explicitly
Always authenticate and authorize based on all available data points. This includes user identity, location, device health, the service being accessed, and more. Don’t trust anyone or anything by default, even if they’ve connected before.
2. Use Least Privilege Access
Grant users the minimum level of access—or “just-in-time” and “just-enough-access” (JIT/JEA)—to the resources they absolutely need to perform their job. This limits the potential damage an attacker can do if an account is compromised.
3. Assume Breach
Operate as if a breach has already occurred. This means you should minimize the “blast radius” by segmenting your network into smaller, isolated zones (a practice called micro-segmentation). This way, if one part of the network is compromised, the attacker is contained and cannot easily move to other parts.
How to Implement a Zero Trust Architecture (Simplified Steps)
Implementing Zero Trust is a journey, not a destination. Here are the foundational steps:
Step 1: Strengthen Identity and Access Management (IAM)
This is the foundation of Zero Trust. You can’t verify everyone if you don’t know who they are. Start by implementing strong authentication methods, with Multi-Factor Authentication (MFA) as the absolute minimum for all users.
Step 2: Implement Micro-segmentation
Break down your large, flat network into smaller, isolated segments. You can create segments based on the sensitivity of the data or the function of the applications within them. This contains threats and prevents lateral movement by attackers.
Step 3: Secure Your Devices (Endpoints)
A user is only as secure as the device they are using. Ensure all devices (laptops, phones, servers) connecting to your network are healthy and compliant with your security policies. Use endpoint detection and response (EDR) tools to monitor for threats.
Step 4: Monitor and Log Everything
You need visibility into what’s happening on your network. Collect logs and use security analytics to detect and respond to threats in real-time. Continuously monitoring traffic helps you understand normal behavior, so you can quickly spot anomalies that could indicate an attack.
Conclusion: A Proactive Approach to Security
Zero Trust is a fundamental shift from a reactive to a proactive security posture. By assuming threats are everywhere and rigorously verifying every access request, you build a more resilient and defensible infrastructure for the modern threat landscape.