Why social engineering attacks are more effective than malware is a question that explains a major shift in modern cyber threats. For years, security strategies focused on blocking malicious software through antivirus tools, firewalls, and intrusion detection systems. Yet despite these defenses, successful attacks continue to rise.
The reason is simple: malware targets machines, but social engineering targets people. By manipulating human behavior, attackers bypass technical controls entirely. This article explains why social engineering consistently outperforms malware, how attackers exploit human weaknesses, and why organizations increasingly struggle to stop these attacks.
Quick Navigation
Malware Targets Systems, Social Engineering Targets Humans
Malware relies on:
-
Exploitable software vulnerabilities
-
Weak configurations
-
Unpatched systems
Social engineering relies on:
-
Trust
-
Urgency
-
Fear
-
Authority
When malware fails to bypass defenses, social engineering convinces users to bypass them willingly. This fundamental difference is central to understanding What Is Social Engineering in Cybersecurity? (Updated Definition)
Security Tools Are Designed to Stop Malware, Not Deception
Modern security tools are effective at:
-
Detecting malicious code
-
Blocking known attack signatures
-
Isolating suspicious files
However, they cannot reliably detect:
-
A user willingly sharing credentials
-
An employee approving a fake request
-
A manager trusting a spoofed executive
This gap explains why human-focused attacks dominate real-world breaches.
Social Engineering Adapts Faster Than Malware
Malware requires:
-
Development and testing
-
Avoidance of detection signatures
-
Infrastructure maintenance
Social engineering requires:
-
A convincing story
-
Basic target research
-
Psychological pressure
Attackers can rapidly adapt social engineering tactics without rewriting code. This flexibility makes attacks harder to predict and easier to scale, as shown throughout Social Engineering: The Complete Guide to Human-Based Cyber Attacks (2026)
Human Psychology Is a Built-In Vulnerability
Social engineering exploits predictable behaviors:
-
Responding quickly to urgent requests
-
Trusting authority figures
-
Avoiding conflict
-
Wanting to be helpful
These behaviors are not flaws—they are social norms. Understanding how attackers weaponize them is explored further in The Psychology Behind Social Engineering Attacks
Malware Is Blocked at the Perimeter, Social Engineering Enters Through the Front Door
Most malware attacks attempt to:
-
Bypass firewalls
-
Evade endpoint detection
-
Avoid sandboxing
Social engineering attacks:
-
Use legitimate communication channels
-
Mimic trusted identities
-
Appear as routine requests
As a result, attackers often gain legitimate access without triggering alarms.
Social Engineering Attacks Leave Fewer Technical Traces
Malware often leaves:
-
Files
-
Network indicators
-
Detectable artifacts
Social engineering may leave:
-
Legitimate logins
-
Approved actions
-
Normal-looking behavior
This makes detection slower and investigations more complex, especially compared to traditional hacking discussed in Social Engineering vs Hacking: What’s the Difference?
Real-World Impact: Why Breaches Start With People
Many major incidents begin with:
-
A phishing email
-
A fake support request
-
An impersonated executive
These scenarios demonstrate why attackers prefer manipulating humans over exploiting systems. Simplified examples for general audiences are outlined in Social Engineering Attacks Explained for Non-Technical Users
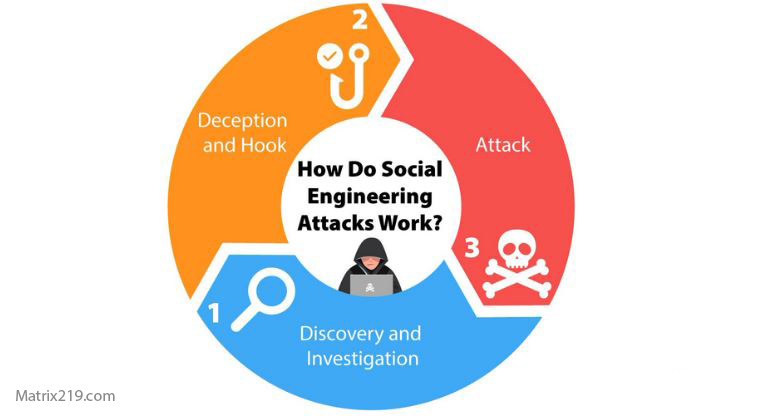
Why Malware Still Exists—but Plays a Secondary Role
Malware has not disappeared. Instead, it is often:
-
Delivered after social engineering succeeds
-
Used to maintain access
-
Deployed once trust is exploited
In this model, social engineering opens the door and malware follows.
Why This Makes Humans the Weakest Security Layer
Because social engineering bypasses technology, people become the primary target.
This reality explains why human behavior is often described as the weakest link, a concept examined in Why Humans Are the Weakest Link in Cybersecurity
External Perspective on Human-Centered Attacks
Industry-wide research confirms that the majority of breaches involve human manipulation rather than pure technical exploitation, as reflected in frameworks such as Verizon Data Breach Investigations Report
Frequently Asked Questions (FAQ)
Why do attackers prefer social engineering over malware?
Social engineering is cheaper, faster, and more reliable than developing malware that must evade security tools.
Does this mean malware is no longer dangerous?
No. Malware remains dangerous, but it is often used after social engineering succeeds.
Can technical defenses stop social engineering?
Technical defenses help, but they cannot stop users from making trust-based decisions.
Are social engineering attacks increasing?
Yes. As technical defenses improve, attackers increasingly shift toward human-focused methods.
Is social engineering harder to detect than malware?
Yes. Social engineering often appears as legitimate behavior, making detection slower and less obvious.
Conclusion
Social engineering attacks are more effective than malware because they exploit human behavior rather than technical weaknesses. While systems can be patched and protected, human trust, urgency, and emotion cannot be “fixed” with software.
As long as people remain part of security processes, social engineering will continue to outperform malware as the most reliable attack method in cybersecurity.