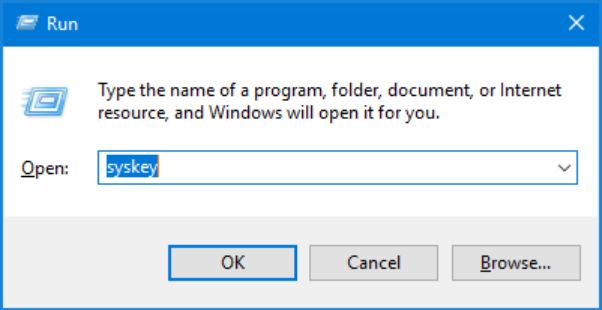
In the evolutionary timeline of operating system security, certain features stand as pivotal, albeit sometimes flawed, milestones. The System Key Utility, known universally by its executable name, Syskey security, is one such feature. Introduced in the era of Windows NT 4.0, it represented one of Microsoft’s early, significant attempts to harden the Windows platform against a burgeoning class of security threats. At a time when physical security breaches were a primary concern for system administrators, Syskey security was engineered with a singular, critical purpose: to protect the Security Account Manager (SAM) database from offline password cracking attacks. This database, the vault for user password hashes, was a prime target for any attacker who could gain physical access to a machine’s hard drive.
Syskey’s approach was to add an extra layer of strong encryption over these already-hashed passwords, rendering the SAM file useless to an attacker unless they also possessed a corresponding “system key”. This concept, while sound in principle, was a product of its time—a time before the widespread adoption of hardware-rooted security, robust full-volume encryption, and a mature understanding of cryptographic best practices. It was designed to solve a specific problem within a threat model that has since been dwarfed by a far more complex and hostile digital landscape.
This report will provide a definitive and exhaustive analysis demonstrating that Syskey security is not merely outdated but is fundamentally insecure by modern standards. Its failure stems from a trifecta of critical weaknesses: the implementation of weak and now-deprecated cryptographic primitives, a fatally flawed key storage mechanism that relied on easily reversible obfuscation, and its unfortunate transformation from a defensive utility into a weapon for malicious actors. Syskey security has been entirely and rightly superseded by a modern, holistic security stack comprising BitLocker for data-at-rest protection, Secure Boot for boot process integrity, and Windows Hello for robust user authentication. The verdict is unequivocal: Syskey boot offers no meaningful security and represents a liability on any system where it might still be found.
Section 1: The Anatomy of Syskey: Purpose and Design
To comprehend the full extent of Syskey’s obsolescence, one must first understand its original architecture and the specific threat it was designed to mitigate. As the “SAM Lock Tool,” its entire existence was predicated on defending a single, vital component of the Windows security architecture.
1.1. The Target: Securing the Security Account Manager (SAM)
The Security Account Manager, or SAM, is a database file stored in the Windows registry (%SystemRoot%\System32\config\SAM) that serves as the primary repository for user account credentials on local, non-domain-controlled Windows machines. It does not store passwords in plaintext; instead, it stores cryptographic hashes of these passwords, typically using the LAN Manager (LM) or New Technology LAN Manager (NTLM) hashing algorithms. When a user attempts to log in, the operating system hashes the provided password and compares it to the stored hash in the SAM database to grant or deny access.
The Syskey utility provided administrators with three distinct modes of operation, each representing a different balance between security and operational convenience.
This was the default and most commonly used configuration, especially after it was enabled by default during the installation of Windows 2000 and later operating systems. In this mode, the system generates a random 128-bit key that is used to encrypt the SAM database. This key is then stored on the local computer’s hard drive, scattered throughout the registry and protected by what Microsoft described as a “complex obfuscation algorithm”. The primary advantage of this mode was its transparency; it allowed for strong encryption of the password information in the registry while enabling the computer to be restarted without any administrator intervention, making it suitable for servers and unattended machines. However, as will be detailed later, the security of this mode was entirely dependent on the secrecy and strength of its obfuscation, a reliance that proved to be its Achilles’ heel.
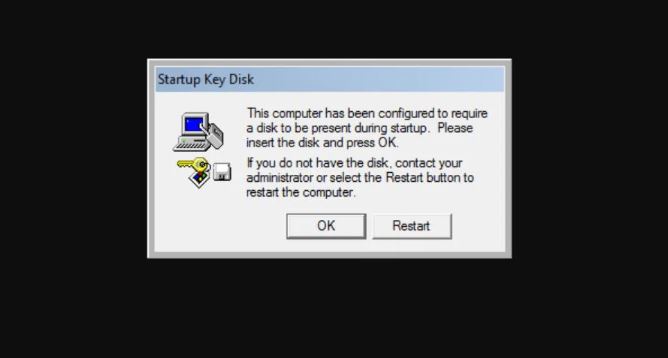
For environments requiring a higher level of security, Mode 2 offered a significant improvement. In this configuration, the system-generated random key was not stored anywhere on the computer itself. Instead, it was written to a removable storage medium, originally a floppy disk. During the system’s startup sequence, the boot process would halt and prompt the administrator to insert the disk containing the system key. Without this physical token, the system could not decrypt the SAM database and would not boot. This mode effectively thwarted the classic offline attack, as an attacker would need to acquire not only the computer’s hard drive but also the corresponding floppy disk. In later years, this functionality could be adapted to work with USB flash drives that were mapped to the A: drive letter. The obvious trade-off was the loss of unattended reboot capability and the operational risk of losing or damaging the key disk, which would render the system unbootable without a prior registry backup.
This mode offered the highest level of security provided by the Syskey utility. Here, an administrator could set a startup password. During the boot sequence, the system would prompt the user to enter this password before proceeding to the user login screen. The 128-bit encryption key was then derived from this password and was never stored on the system in any form. This made the system highly resistant to offline attacks, as the critical secret existed only in the administrator’s memory. However, this security came at a high price. Like Mode 2, it prevented unattended reboots. More critically, if the password was forgotten, the system was rendered completely inaccessible, with no recovery option other than restoring the registry from a backup made before Syskey was enabled.
While Syskey’s design philosophy was already problematic, its technical implementation was riddled with vulnerabilities that rendered it insecure by modern cryptographic standards. Its foundation was built on weak algorithms, its key protection mechanism was a trivial exercise in obscurity, and its history was marked by early signs of fragility.
2.1. Cryptographic Failure: A Foundation of Sand
The cryptographic primitives chosen for Syskey in the 1990s are now considered dangerously obsolete. The core encryption of the SAM database was performed using a 128-bit RC4 stream cipher, and key derivation (for example, from the Mode 3 startup password) utilized the MD5 hashing algorithm.
RC4, once widely used in protocols like SSL/TLS, has been found to possess significant cryptographic weaknesses, including biases in its output keystream that can be exploited to recover the plaintext. These vulnerabilities have led to its formal deprecation and prohibition in modern secure communication standards. Similarly, MD5 has been cryptographically broken for over a decade; it is not collision-resistant, meaning attackers can create different inputs that produce the same hash value. This makes it unsuitable for any security application that relies on hashing for integrity or key derivation.
Microsoft itself acknowledged this fundamental weakness when it officially deprecated the utility, stating that “Syskey is based on weak cryptography that can easily be broken in modern times”. Relying on these broken algorithms means that even in its most secure configurations (Modes 2 and 3), the underlying encryption layer is fragile and does not meet the baseline requirements for modern data protection.
The most catastrophic failure of Syskey lies in its default and most common configuration: Mode 1, where the bootkey is stored locally. The security of this entire mode rested on Microsoft’s claim of a “complex obfuscation algorithm” used to hide the key within the system registry. However, independent security research, most notably documented in a detailed analysis that led to the creation of tools like
pwdump2, completely dismantled this claim, revealing the “algorithm” to be nothing more than trivial security through obscurity.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\JDHKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Skew1HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\DataHKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\GBG
The obfuscation was not a cryptographic function but a simple permutation. The key components were hidden as hexadecimal strings within the Class attribute of these registry keys. The recovery process simply required reassembling these components in the correct order, a sequence that was quickly reverse-engineered.
- System Acquisition: The attacker boots the target machine using a live operating system from a USB drive or connects the hard drive to another computer.
- Hive Extraction: The attacker copies two critical files from the Windows partition:
C:\Windows\System32\config\SAM(containing the encrypted password hashes) andC:\Windows\System32\config\SYSTEM(containing the obfuscated bootkey). - Bootkey Recovery: The attacker uses a tool like
Bkhiveto process the SYSTEM hive. The tool applies the known reverse permutation to theClassattributes of the four LSA keys and extracts the raw 128-bit bootkey. On older systems (pre-Windows NT 4.0 SP4), the permissions on these registry keys were so lax that even a standard user could extract the key while the system was running. - Hash Decryption: With the bootkey recovered, the attacker uses a tool like
SAMDUMP2. This tool takes the SAM file and the recovered bootkey as input. It then emulates the Windows boot process to derive a final session key (hbootkey) and uses it with the RC4 algorithm to decrypt the password hashes for each user account stored in the SAM file. - Offline Cracking: The attacker is now left with the original NTLM password hashes, completely stripped of Syskey’s protection. They can proceed with standard offline cracking techniques as if Syskey had never been enabled.
This entire process demonstrates a catastrophic failure in security design. The decision to store the key, however obfuscated, on the same device it was protecting created an inherent and ultimately fatal vulnerability. It was a digital equivalent of hiding the key to a safe under the doormat in front of it. This reliance on a secret, easily reversed obfuscation method stands in stark contrast to modern security principles, which are founded on public, heavily scrutinized cryptographic algorithms and hardware-based key protection. The security of a modern system like one using BitLocker does not depend on keeping the encryption method secret, but on the proven mathematical difficulty of breaking the AES algorithm and the physical tamper-resistance of a hardware security module like the TPM. Syskey’s failure was therefore not just a matter of choosing poor algorithms, but a failure of its entire security philosophy.
2.3. The “Syskey Bug” and a History of Vulnerability
Even before its obfuscation scheme was publicly broken, Syskey’s security was shown to be imperfect. In December 1999, a security team from BindView discovered a significant flaw, dubbed the “Syskey Bug,” which affected Windows NT 4.0 and pre-release versions of Windows 2000. This vulnerability indicated that a form of offline cryptanalytic attack was possible against a syskeyed SAM, allowing for a brute-force attack that was previously thought to be infeasible. While Microsoft subsequently issued a patch to correct the issue, the discovery served as an early warning that the implementation of Syskey was not as robust as it appeared. It was a symptom of a design that had not been subjected to the rigorous public scrutiny expected of modern security components, foreshadowing the more fundamental flaws that would later be uncovered.
Perhaps the most compelling reason for Syskey’s removal was not its technical failings, but its transformation from a niche security tool into a favored weapon of cybercriminals. The very feature designed to offer the highest level of security—the pre-boot password—became the mechanism for a widespread and damaging form of extortion.
3.1. The Tech Support Scam Epidemic
In the 2010s, a particular type of fraud known as the “tech support scam” became rampant. The typical modus operandi involved a scammer, often posing as an employee from Microsoft or another major tech company, convincing a victim to grant them remote access to their computer under the guise of fixing a non-existent virus or performance issue.
The widespread abuse of Syskey, combined with its increasingly obvious technical weaknesses, made its position within the Windows operating system untenable. Microsoft made the decisive move to remove the utility entirely, starting with the Windows 10 Fall Creators Update (version 1709) and Windows Server 2016 (version 1709).
Microsoft’s official documentation provides a clear and concise summary of the reasons for this deprecation:
- Insecure Cryptography: The utility was based on weak cryptographic algorithms (RC4, MD5) that are no longer considered secure and can be easily broken by modern methods.
- Limited Scope of Protection: Syskey’s protection was narrowly focused on the SAM database. It did not cover all files or data on the operating system volume, leaving vast amounts of sensitive information vulnerable to offline attacks.
- Widespread Malicious Use: The utility had become a known tool for hackers and scammers as part of ransomware and extortion schemes, turning a feature intended for security into a significant liability for Windows users.
In place of Syskey, Microsoft’s official and unequivocal recommendation is for users to adopt modern, robust security technologies, with BitLocker Drive Encryption being the primary replacement for data-at-rest protection. This decision marked the official end of Syskey’s long and troubled history, closing the chapter on a security tool that had been outpaced by technology and co-opted by crime.
The removal of Syskey was not merely the deletion of an old feature; it was a reflection of a fundamental shift in Microsoft’s approach to endpoint security. Syskey was a single-point solution for a single, narrowly defined problem. Its replacements—BitLocker, Secure Boot, and Windows Hello—are not individual tools but interlocking components of a comprehensive, layered defense-in-depth strategy. Each addresses a different threat vector, and together they provide a level of security that Syskey could never achieve.
The following table provides a high-level comparison that starkly illustrates the architectural and philosophical differences between Syskey and its modern successors.
4.1. Full-Volume Encryption: BitLocker as the True Successor
BitLocker Drive Encryption is the direct and vastly superior replacement for Syskey’s intended function of protecting data against offline attacks. However, its approach is far more comprehensive and robust.
Instead of encrypting a single database file, BitLocker provides encryption for the entire operating system volume. This means that all data at rest—including the SAM database, user documents, temporary files, the page file, and all operating system binaries—is rendered unreadable without the proper decryption key. This holistic approach completely mitigates the threat of an attacker selectively stealing files from a compromised drive; the entire volume is an opaque, encrypted block.
While both Syskey security and Secure Boot operate during the pre-boot phase, they serve entirely different and complementary purposes. This distinction is crucial: Syskey’s password prompt was for user authentication—a mechanism to prove a user’s identity to unlock an encryption key. Secure Boot, in contrast, performs software attestation—a mechanism to prove that the code being loaded is authentic and has not been maliciously modified.
- The Signature Database (db), which contains the public keys or hashes of trusted operating system bootloaders, firmware drivers, and applications.
- The Revoked Signatures Database (dbx), which contains a blacklist of signatures corresponding to known malicious or vulnerable components.
When a Secure Boot-enabled PC starts, the firmware begins a chain of trust. It first verifies the digital signature of the bootloader against the db. If the signature is valid and not present in the dbx, the firmware transfers control to the bootloader. The bootloader then continues the process, verifying the signature of the operating system kernel before loading it. If at any point in this chain a signature is found to be invalid, missing, or explicitly revoked, the boot process is halted, preventing the potentially malicious code from executing.
4.3. Identity and Authentication: Windows Hello’s Paradigm Shift
The final piece of the modern security stack, Windows Hello, addresses the problem of user authentication—the very area Syskey security tried to reinforce. But where Syskey’s goal was to better protect the password, Windows Hello’s goal is to eliminate it entirely.
- Enrollment: When a user sets up Windows Hello, the system generates a unique cryptographic key pair (a public key and a private key). The private key is securely stored and protected by the device’s TPM. The public key is registered with the user’s identity provider (such as their Microsoft Account or an enterprise Azure Active Directory account).
- Authentication: When the user needs to sign in, they provide their biometric gesture or PIN. This action does not transmit a secret over the network. Instead, it serves as an authorization for the TPM to access the protected private key. The identity provider sends a challenge (a piece of data) to the device. The TPM uses the private key to cryptographically sign this challenge and sends the signed response back.
- Verification: The identity provider uses the user’s previously registered public key to verify the signature on the response. If the signature is valid, authentication succeeds, and the user is granted access.
This architecture provides monumental security advantages over password-based systems, even those protected by Syskey. The user’s actual secret—the private key—never leaves the hardware-protected boundary of the TPM. The biometric data used to unlock it is also processed securely on the device and is never transmitted. This model is inherently resistant to the most common forms of credential theft:
- Phishing: There is no password for an attacker to trick the user into revealing.
- Server-Side Breaches: The identity provider’s servers only store the public key, which is not a secret. A breach of the server does not expose user credentials.
- Replay Attacks: The challenge-response mechanism prevents an attacker from capturing and re-using an old authentication session.
This layered defense model illustrates a mature and robust security architecture. Syskey security was a single, brittle wall built to guard one part of the castle. The modern Windows security stack is a system of interlocking defenses: Secure Boot guards the gates and ensures only trusted guards are on duty; BitLocker encrypts the entire castle and everything in it; and Windows Hello provides a phishing-proof method for the king to prove his identity without ever sharing the secret royal password. An attacker seeking to compromise a modern, properly configured Windows device must find a way to defeat all three of these mutually reinforcing layers—a task orders of magnitude more difficult than simply reversing Syskey’s flawed obfuscation.
Conclusion: The Final Verdict on Syskey Boot Security
The analysis of the System Key Utility’s architecture, cryptographic implementation, and historical context leads to an unequivocal and absolute conclusion: Syskey boot is not secure. It is a deprecated feature from a bygone era of computing that provides a dangerously false sense of security. Its continued use on any system, for any purpose, constitutes a significant security risk.
This verdict is founded on a confluence of irremediable failures. First, its cryptographic underpinnings—the RC4 stream cipher and the MD5 hashing algorithm—are fundamentally broken by modern standards, a fact acknowledged by Microsoft itself as a primary reason for its deprecation. Second, its default and most common mode of operation, which stores the encryption key locally, relies on a trivial and easily reversible obfuscation scheme, rendering it completely ineffective against the very offline attacks it was designed to prevent. Finally, its most secure mode was systematically weaponized by cybercriminals, transforming a defensive tool into a mechanism for extortion and making it a liability to the Windows ecosystem.
The path forward for securing Windows endpoints is clear and does not involve seeking a direct, one-to-one replacement for Syskey security. Instead, it requires the adoption of the modern, layered security model that has been architected to replace it and address a far broader range of threats. The actionable recommendation for any administrator or security professional is to ensure that all systems adhere to the following baseline:
- Enable the Trusted Platform Module (TPM) in the device firmware as the hardware root of trust.
- Implement BitLocker Drive Encryption to provide robust, full-volume, data-at-rest protection against offline attacks.
- Ensure Secure Boot is active to maintain the integrity of the boot process and protect against bootkits and rootkits.
- Transition users to passwordless authentication with Windows Hello to mitigate the risks of phishing and credential theft.
Syskey security was a well-intentioned but ultimately flawed solution to a problem of its time. The threat landscape has evolved, and so have the defenses. To rely on Syskey security today is to ignore two decades of progress in cybersecurity and to leave a system vulnerable to attacks that have long since been solved by superior, integrated, and hardware-backed technologies. Its chapter in the history of Windows security is definitively closed.