Business Email Compromise (BEC) is one of the most financially damaging forms of online fraud, yet it often goes unnoticed until after money is gone. Unlike loud scams that rely on fake websites or malware, BEC is quiet, precise, and deeply contextual.
In 2026, BEC scams target companies of all sizes—from startups to enterprises—by exploiting routine workflows, trust in internal communication, and payment processes. The scam often looks like normal business.
This article explains how BEC scams work, why they bypass traditional security controls, and how organizations and individuals can detect them before irreversible transfers occur.
What Business Email Compromise Really Is
BEC is not primarily a technical attack. It is a trust-based fraud.
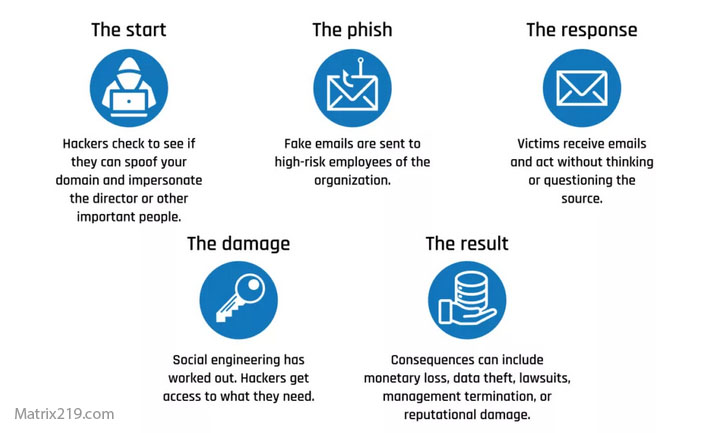
Attackers impersonate executives, finance staff, vendors, or partners to manipulate employees into sending money or sensitive information. The communication appears legitimate, timely, and routine.
No malware is required. No fake websites are necessary. Only belief.
How Attackers Gain the Right Context
Context is the most valuable asset in BEC scams.
Attackers gather information from:
-
Compromised email accounts
-
Data breaches
-
Social media and company websites
-
Previous phishing campaigns
This allows them to understand payment cycles, authority structures, and communication tone.
Preparation makes the scam invisible.
Common Types of BEC Scams
BEC scams usually follow predictable patterns.
These include fake invoice requests, last-minute changes to bank details, executive impersonation demanding urgent transfers, payroll diversion scams, and vendor impersonation during real transactions.
Each variant exploits existing business processes.
Why BEC Scams Bypass Security Tools
Traditional security tools look for malware, links, and attachments.
BEC emails often contain none of these. Messages are short, plain text, and sent from real or convincingly spoofed accounts. Automated filters see nothing suspicious.
Human judgment becomes the only control—and that is where the scam operates.
The Role of Urgency and Authority
Urgency is carefully calibrated.
Attackers often send messages near deadlines, during travel, or outside normal hours. Authority discourages questioning, especially when requests appear to come from senior leadership.
Hierarchy suppresses verification.
Why Employees Don’t Verify
Verification fails for social reasons, not technical ones.
Employees fear appearing incompetent, slowing business, or questioning authority. Scammers rely on this hesitation.
The scam succeeds when verification feels inappropriate.
Red Flags That Actually Matter
Reliable BEC indicators include:
-
Requests to change payment details suddenly
-
Pressure to bypass normal approval processes
-
Unusual secrecy or urgency
-
Minor deviations in tone or timing
-
Requests that arrive at inconvenient moments
Process deviation is the signal—not spelling errors.
How to Stop BEC Scams Before Payment
Effective prevention is procedural.
Best practices include:
-
Mandatory payment change verification
-
Dual approval for transfers
-
Clear out-of-band confirmation rules
-
Training that empowers employees to pause
Rules remove social pressure.
What To Do If a BEC Scam Succeeds
If funds were sent:
-
Contact your bank immediately
-
Report internally and freeze related processes
-
Preserve email evidence
-
Notify law enforcement if required
Speed is critical. Minutes matter.
What To Do If a BEC Scam Succeeds
Why Small Businesses Are Increasingly Targeted
Smaller organizations often lack strict controls.
Fewer approval layers, informal processes, and limited training make them attractive targets. BEC does not require scale—only opportunity.
Every business is a potential target.
BEC Scams as a Systemic Risk
BEC scams exploit how businesses actually work—not how policies say they should work.
Reducing risk requires aligning security with real workflows, not ideal ones.
Security must fit human behavior.
BEC in the Broader Fraud Landscape
BEC scams often intersect with account takeover, impersonation, and payment fraud.
Understanding BEC improves resilience across both personal and organizational fraud threats.
For the complete fraud framework this article supports, see: Online Scams & Digital Fraud: How to Spot, Avoid, and Recover (2026 Guide)
FAQ
Do BEC scams only target large companies?
No. Small and mid-sized businesses are frequent targets.
Are BEC emails always sent from hacked accounts?
Not always, but many are.
Why don’t spam filters catch BEC?
Because messages often contain no technical indicators.
Is employee training effective?
Yes—when paired with clear procedures.
Can funds be recovered after BEC?
Rarely, unless action is immediate.





