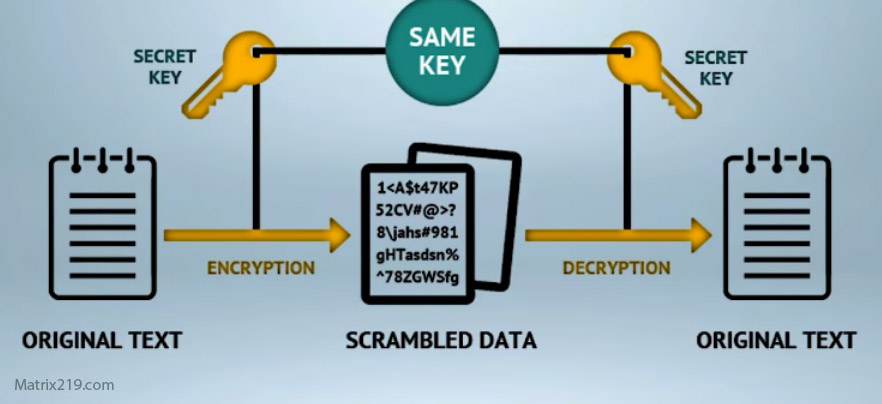
Many people assume that once a file is encrypted, it becomes completely immune to hacking. In reality, the question Can Encrypted Files Be Hacked? reflects a deeper concern about where encryption truly protects data—and where it does not. In 2026, attackers rarely “break” encryption mathematically. Instead, they exploit weaknesses around it: poor key handling, compromised devices, and human error.
This article explains what hacking encrypted files actually means in practice, how attackers bypass encryption without cracking it, and which scenarios genuinely put encrypted data at risk. Understanding these distinctions helps you use encryption realistically—neither overestimating its power nor underestimating its importance.
Quick Navigation
What “Hacking Encrypted Files” Really Means
Breaking Encryption vs Bypassing It
Cracking strong encryption directly is not feasible with modern algorithms.
Attacking the Environment Around Encryption
Hackers target keys, devices, and users rather than the encrypted data itself.
Why This Distinction Matters
Most real-world breaches occur without breaking encryption at all.
This misconception is common and leads to misplaced confidence.
Can Strong Encryption Be Cracked?
Modern Algorithms Are Not the Weak Point
When implemented correctly, modern encryption resists brute-force attacks.
Time and Computing Limits
Breaking strong encryption would require unrealistic time and resources.
Why Attackers Choose Easier Paths
Human and system weaknesses are far more efficient targets.
Algorithm fundamentals are explained in Common File Encryption Algorithms (AES, RSA, ChaCha20).
Common File Encryption Algorithms AES, RSA, ChaCha20
How Encrypted Files Actually Get Compromised
Stolen or Exposed Encryption Keys
If an attacker gets the key, encryption becomes irrelevant.
Malware on the User’s Device
Files are vulnerable while decrypted and in active use.
Insecure Key Storage
Keys stored alongside encrypted files defeat encryption entirely.
These failures are repeatedly discussed in Common File Encryption Mistakes to Avoid.
Device Compromise: The Biggest Risk
Encryption Does Not Protect Active Files
Once a file is opened, it exists in plaintext temporarily.
Keyloggers and Screen Capture Malware
Attackers can capture passwords or decrypted content directly.
Why Endpoint Security Still Matters
Encryption complements security—it does not replace it.
This limitation is often misunderstood and explored in Is File Encryption Really Secure?
Password-Based Encryption Risks
Weak or Reused Passwords
Human-chosen passwords are often predictable.
Brute-Force Against Weak Keys
Poor passwords can still be cracked despite strong algorithms.
Importance of Key Strength
Key quality matters as much as algorithm choice.
Password misconceptions are tied to Encryption vs Password Protection.
Cloud and Encrypted Files
Provider Account Compromise
Encrypted files remain protected if keys are not stored in the cloud.
Storing Keys in the Same Account
This common mistake allows attackers to decrypt files easily.
Client-Side Encryption Advantage
Encrypting files before upload removes cloud trust assumptions.
Cloud-specific risks are discussed in File Encryption for Cloud Storage.
Can Encrypted Files Be Hacked in Business Environments?
Insider Threats
Authorized users can misuse decrypted access.
Poor Access Revocation
Former employees may retain access if keys are not rotated.
Centralized Key Control Matters
Organizations reduce risk through policy and auditing.
Business scenarios are discussed in File Encryption Software for Business.
When Encrypted Files Are Effectively “Unhackable”
Proper Key Management
Keys are stored securely and separately.
Clean, Trusted Devices
Systems are free from malware and unauthorized access.
Minimal Plaintext Exposure
Files are decrypted only when absolutely necessary.
These conditions define encryption success.
When Encryption Fails to Protect Data
Lost or Stolen Keys
Encryption provides no protection once keys are exposed.
Compromised Endpoints
Malware bypasses encryption during legitimate access.
False Encryption Claims
Some tools do not encrypt data properly at all.
Warning signs are explained in Signs Your File Encryption Software Is Fake.
How to Reduce the Risk of Encrypted File Compromise
Protect Encryption Keys First
Key security determines encryption security.
Limit Decryption Time
Do not leave sensitive files open longer than necessary.
Combine Encryption With Other Controls
Endpoint security and access control remain essential.
A broader strategy is outlined in Best File Encryption and Decryption Software in 2026 (Complete Guide).
Standards and Security Reality
Security models aligned with NIST encryption standards assume that encryption protects data only as long as keys and endpoints remain secure.
Frequently Asked Questions (FAQ)
Can hackers crack encrypted files directly?
Not realistically, if strong encryption is used correctly.
Are encrypted files safe if my computer is hacked?
Not while files are open or keys are accessible.
Does encryption stop ransomware?
It can limit damage but does not prevent infection.
Are encrypted cloud files safe if my account is hacked?
Yes, if encryption keys are not stored in the same account.
Is encryption still worth using?
Absolutely. Most breaches succeed because encryption is missing or misused.