Can hackers spy on your phone in real time is one of the most frightening questions people ask after suspecting a compromise. Movies and social media make it seem like attackers can instantly watch your screen, hear your calls, and track every tap. The reality is more constrained—but still serious under specific conditions.
This article explains what real-time spying actually means on phones, when it’s technically possible, when it’s unlikely, and how to recognize the difference. You’ll also learn which actions immediately reduce risk and which fears are usually exaggerated.
Quick Navigation
What “Real-Time Spying” Means on a Phone
Real-time spying isn’t a single capability.
Common forms of real-time access
-
Live screen viewing or screen capture
-
Audio recording during calls or ambient sound
-
Keystroke and notification interception
-
Live location tracking
Each requires specific permissions or account access, not magic exploits.
For the full context of phone compromise, review: If Your Phone Is Hacked: How to Know, What to Do, and How to Stay Safe
When Real-Time Phone Spying Is Technically Possible
Live spying requires sustained access.
Conditions that make real-time spying possible
-
Spyware with accessibility or screen-record permissions
-
Active remote-control apps disguised as system tools
-
Compromised Apple ID or Google account with device sync
-
Messaging apps with linked devices you didn’t approve
If one of these exists, live monitoring becomes feasible.
To identify early warning signs, see: If your phone is hacked how to know
When Real-Time Spying Is Unlikely
Most cases do not involve live surveillance.
Situations where real-time spying is unlikely
-
No unknown permissions or profiles
-
No persistent background network activity
-
No linked devices or account alerts
In many incidents, attackers rely on periodic data sync, not continuous viewing.
Android vs iPhone: Real-Time Spying Differences
Platform design changes the threat surface.
On Android phones
-
Accessibility abuse can enable screen reading
-
Remote-control apps can run quietly
-
Battery or heat spikes may appear during live access
Related context: Signs your Android phone is hacked
On iPhones
-
Live spying usually requires account-level access or profiles
-
System sandboxing limits continuous screen capture
Related context: Signs your iPhone is hacked
How to Reduce the Risk of Live Spying Immediately
If you suspect active monitoring, act fast.
Immediate containment steps
-
Turn on airplane mode to cut live connections
-
Stop sensitive activity on the phone
-
Secure email and cloud accounts from a clean device
Emergency sequencing is covered here: What to do immediately if your phone is hacked
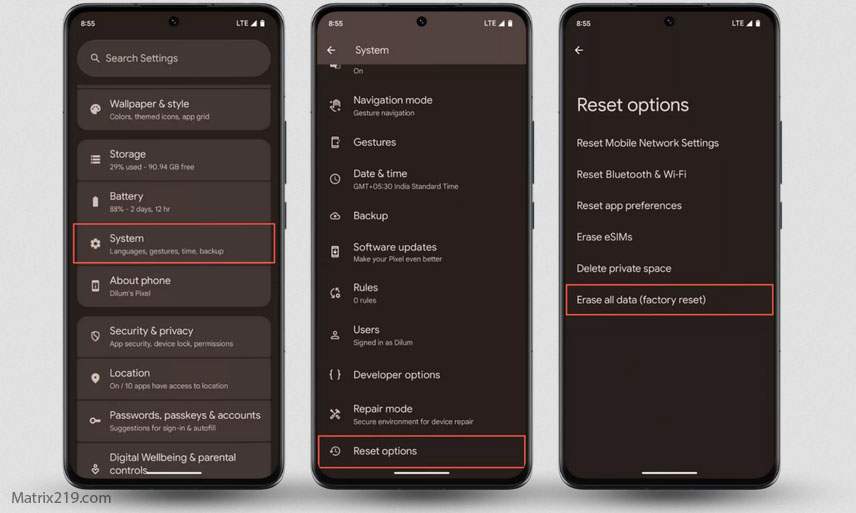
What to do immediately if your phone is hacked
Signs You Might Be Under Live Surveillance
Treat this as serious only when signs align.
Indicators of possible real-time spying
-
Screen wakes or reacts without touch
-
Camera or microphone indicators activating unexpectedly
-
Battery drain or heat during inactivity
-
Repeated network activity while idle
One sign alone is not proof—patterns matter.
What Live Spying Cannot Usually Do
Understanding limits prevents panic.
Common misconceptions
-
Attackers can’t read thoughts or bypass encryption remotely
-
They can’t control the phone without permissions
-
They can’t spy indefinitely without power and connectivity
Live access is fragile and easier to disrupt than people think.
What to Do If You Suspect Live Spying
Move from fear to control.
Correct response order
-
Isolate the phone (airplane mode)
-
Secure email and platform accounts
-
Revoke app permissions and sessions
-
Decide on cleanup or reset
A full recovery workflow is here: If Your Phone Is Hacked: Step-by-Step Recovery Guide (Android & iPhone)
Security analyses consistently show that real-time mobile surveillance is far less common than delayed data collection, because continuous monitoring is resource-heavy and easier to detect, which is why attackers prefer stealthy sync-based methods Mobile surveillance capabilities and limitations overview
Frequently Asked Questions
Can hackers watch my screen live?
Only if spyware with screen or accessibility access is installed.
Can they hear calls in real time?
Sometimes—if microphone access is granted or calls are routed through apps.
Is live spying common?
No. It’s rarer than people fear.
Does airplane mode stop live spying?
Yes, temporarily—by cutting connections.
Should I assume live spying if I feel paranoid?
No. Look for technical signs and patterns first.