As organizations grow, file encryption stops being a technical feature and becomes an operational system. In 2026, decentralized encryption—where individuals manage their own keys and tools—creates serious risk: lost access, inconsistent protection, and failed audits. Centralized File Encryption Management Systems address these problems by shifting encryption from individual behavior to enforceable policy.
This article explains what centralized encryption management actually is, how it works in practice, and why it has become essential for businesses handling sensitive data at scale. Rather than focusing on vendors, the emphasis is on architecture, control, and real operational outcomes. Understanding these systems helps organizations reduce human error, maintain compliance, and keep encrypted data accessible and secure over time.
Quick Navigation
What Centralized File Encryption Management Means
Policy-Driven Encryption
Encryption rules are defined centrally and applied automatically across users, devices, and storage locations.
Organization-Owned Key Control
Keys are generated, stored, rotated, and revoked by the organization—not individual employees.
Unified Visibility
Security teams can see where encrypted files exist, who accessed them, and under what conditions.
This marks a clear shift from ad-hoc encryption practices.
Why Decentralized Encryption Fails at Scale
Key Loss and Orphaned Data
When users manage their own keys, files often become permanently inaccessible.
Inconsistent Encryption Coverage
Some files are encrypted, others are not—creating blind spots.
No Auditability
Without centralized logs, organizations cannot prove compliance or investigate incidents.
These failures are frequently discussed in Common File Encryption Mistakes to Avoid
Core Components of Centralized Encryption Systems
Central Key Management Infrastructure
A dedicated system handles key lifecycle management securely and consistently.
Identity and Access Integration
Access to encrypted files is tied to verified user identity and role.
Policy Engines and Automation
Rules define when files are encrypted, who can decrypt them, and how access is enforced.
Key architecture principles are grounded in Symmetric vs Asymmetric File Encryption.
How Centralized File Encryption Works in Practice
Automatic Encryption at File Creation
Files are encrypted by default based on policy, without user action.
Transparent Access for Authorized Users
Employees work normally while encryption operates silently.
Immediate Access Revocation
When roles change or devices are compromised, access can be revoked instantly.
A beginner-friendly workflow is outlined in How File Encryption Works (Beginner Friendly)
Centralized Encryption Across Devices and Locations
Endpoint-Agnostic Protection
Encryption follows the file across laptops, servers, and cloud platforms.
Remote and Hybrid Work Support
Policies remain enforced regardless of where users work.
External Storage and Transfers
Encrypted files remain protected on USB drives and shared media.
Remote scenarios are discussed in File Encryption for Remote Work Security.
Centralized Encryption and Cloud Environments
Client-Side Encryption at Scale
Files are encrypted before reaching cloud providers, preserving key ownership.
Multi-Cloud Consistency
Encryption policies apply uniformly across different cloud platforms.
Preventing Provider-Level Access
Centralized control ensures providers cannot decrypt stored files.
Cloud-specific workflows are explained in File Encryption for Cloud Storage.
Compliance and Audit Advantages
Enforced Encryption Policies
Centralized systems ensure regulated files are always encrypted.
Detailed Audit Logs
Access, decryption events, and policy changes are fully recorded.
Clear Key Custody
Organizations can prove who controls encryption keys and why.
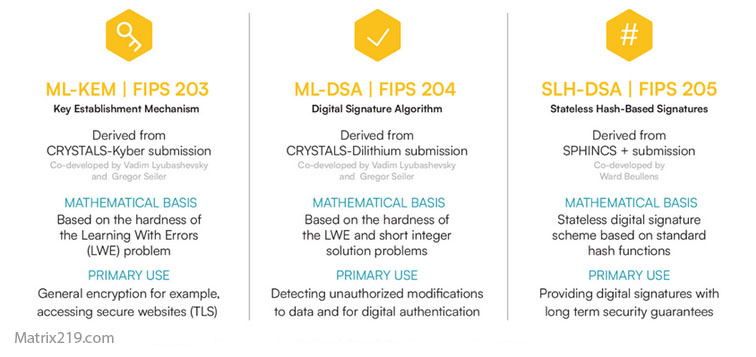
Compliance alignment is often evaluated against NIST encryption standards in regulatory audits.
NIST encryption standards
Performance and Reliability Considerations
Scaling Without Bottlenecks
Centralized control must not slow file access or business operations.
High Availability of Key Services
Encryption systems must remain accessible during outages.
Hardware Acceleration and Optimization
Modern systems minimize performance impact through optimized cryptography.
Performance trade-offs are often misunderstood and discussed in Is File Encryption Really Secure?
When Centralized Encryption Is Essential
Medium to Large Organizations
As user count grows, manual encryption becomes unmanageable.
Regulated Industries
Healthcare, finance, and legal sectors require consistent enforcement.
Long-Term Data Retention
Centralized systems reduce key-loss risk over years of storage.
Enterprise requirements are detailed in Enterprise File Encryption Solutions Explained.
When Centralized Encryption May Be Overkill
Single-User Environments
Individuals may not need centralized management.
Short-Term or Low-Risk Data
Simple encryption tools may suffice for temporary files.
Limited IT Resources
Poorly implemented centralization can be worse than simple controls.
A cost-benefit comparison is covered in Free vs Paid File Encryption Software.
How to Evaluate Centralized Encryption Management Systems
Assess Organizational Risk
Identify which data types require enforced encryption.
Validate Policy Flexibility
Systems must adapt to role changes and workflows.
Test Recovery and Continuity
Key escrow and disaster recovery must be clearly defined.
A full evaluation framework is provided in Best File Encryption and Decryption Software in 2026 (Complete Guide).
Frequently Asked Questions (FAQ)
Do centralized encryption systems replace disk encryption?
No. They complement disk encryption by protecting files beyond devices.
Who should manage centralized encryption?
Dedicated IT or security teams should control policies and keys.
Can centralized encryption work with remote teams?
Yes. Policies apply regardless of location or device.
Does centralized encryption slow down workflows?
Not when implemented correctly with modern architecture.
Is centralized encryption required for compliance?
In many regulated environments, it is strongly recommended or expected.





