Critical infrastructure cyber defense strategies are no longer optional. As essential services become increasingly digitized, the systems that support electricity, water, transportation, and communications face growing exposure to cyber risks. The question for operators is no longer whether attacks or failures will occur, but how effectively systems can withstand, contain, and recover from them.
Unlike traditional IT environments, critical infrastructure operates under strict availability requirements. Defensive strategies must balance security improvements with operational continuity. This article outlines realistic, proven approaches to defending critical infrastructure without disrupting essential services.
Quick Navigation
Why Defense in Critical Infrastructure Is Different
Security strategies for infrastructure must account for:
-
Continuous operation with minimal downtime
-
Legacy systems that cannot be easily replaced
-
Safety-critical physical processes
These constraints mean that aggressive security changes can be as dangerous as inaction. Many defensive failures originate from misaligned security models discussed in industrial control system security failures
Prioritizing Resilience Over Absolute Prevention
Perfect security is unrealistic, especially against sophisticated threats.
Effective defense focuses on:
-
Early detection rather than total blockage
-
Limiting blast radius when incidents occur
-
Rapid, controlled recovery
This mindset directly addresses the broader critical infrastructure cybersecurity risks
Core Cyber Defense Strategies for Critical Infrastructure
Network Segmentation Between IT and OT
Segmentation reduces the likelihood that:
-
IT breaches reach operational systems
-
Malware spreads laterally
-
Incidents escalate uncontrollably
Strong boundaries are foundational to infrastructure defense.
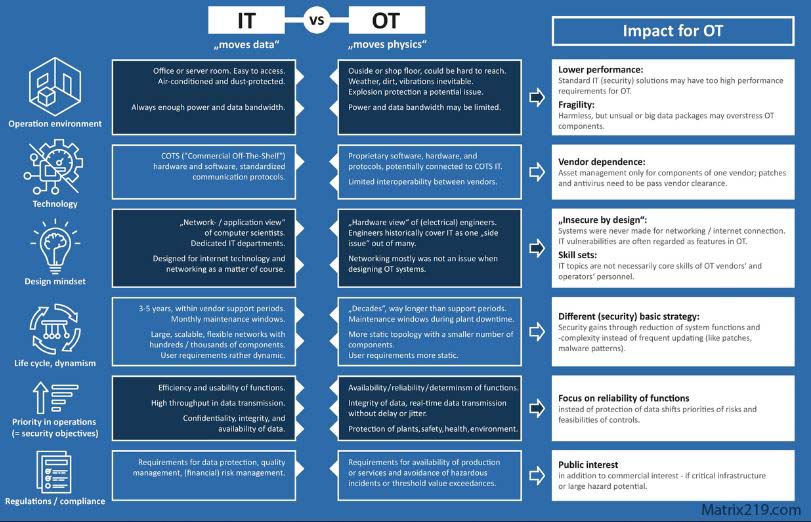
OT vs IT security in critical infrastructure
Strict Access Control and Authentication
Defensive measures should include:
-
Role-based access
-
Multi-factor authentication where feasible
-
Removal of shared accounts
These controls reduce exposure from both external attackers and insider threats.
Continuous Monitoring and Anomaly Detection
Passive monitoring tools designed for OT environments can:
-
Detect unusual commands
-
Identify abnormal traffic patterns
-
Alert operators without interfering with operations
Such visibility helps differentiate normal failure from malicious activity, supporting power grid failure vs cyberattack
Incident Response Planning for Infrastructure Environments
Infrastructure incident response differs from IT response.
Plans must consider:
-
Safe shutdown procedures
-
Manual operation fallback
-
Coordination between engineering and security teams
Response planning also supports delayed but responsible attribution, addressing cyberattack attribution challenges
Managing the Nation-State Threat Reality
Critical infrastructure operators must assume that advanced threats may already exist within networks.
Defense against nation-state actors relies on:
-
Long-term visibility
-
Threat hunting
-
Defense-in-depth strategies
This reality reflects the operational environment shaped by state-sponsored cyber operations explained
Training and Organizational Preparedness
Technology alone is insufficient.
Effective defense requires:
-
Regular staff training
-
Clear roles during incidents
-
Communication protocols for internal and external stakeholders
Human readiness often determines whether an incident becomes a controlled event or a public crisis.
Measuring Defense Effectiveness Over Time
Defense maturity should be evaluated through:
-
Regular risk assessments
-
Tabletop and live simulations
-
Post-incident reviews
Continuous improvement is essential as systems and threats evolve.
Conclusion
Critical infrastructure cyber defense strategies must be realistic, balanced, and resilient by design. Security improvements cannot come at the cost of operational safety, yet ignoring cyber risks is no longer viable.
By focusing on segmentation, monitoring, access control, and preparedness, organizations can significantly reduce the impact of both cyberattacks and system failures. In an environment where disruption is inevitable, resilience is the true measure of defense.





