Critical infrastructure cybersecurity risks have become a central concern as governments and organizations increasingly rely on digital systems to operate essential services. Power grids, water treatment plants, transportation networks, and healthcare systems all depend on interconnected technologies that were never originally designed to withstand modern cyber threats.
Unlike typical IT environments, critical infrastructure systems combine physical processes with digital control. This convergence creates unique vulnerabilities where a cyber incident can escalate into real-world disruption. Understanding these risks is essential not only for security professionals but also for decision-makers responsible for public safety and national stability.
This article explains why critical infrastructure is especially vulnerable, what types of risks are most common, and how these weaknesses can translate into large-scale failures.
Quick Navigation
What Is Considered Critical Infrastructure?
Critical infrastructure refers to systems and assets whose disruption would have a severe impact on society, the economy, or national security.
Common examples include:
-
Electricity generation and distribution
-
Water and wastewater systems
-
Oil and gas pipelines
-
Transportation networks
-
Telecommunications
-
Healthcare services
These sectors share a common challenge: they must operate continuously, often using legacy technologies that are difficult to upgrade or replace without downtime.
Why Critical Infrastructure Faces Unique Cybersecurity Risks
Legacy Systems and Technical Debt
Many infrastructure environments rely on decades-old systems that were designed for reliability, not security. These systems often:
-
Lack encryption
-
Use outdated authentication methods
-
Cannot be easily patched
This creates long-term exposure that attackers can exploit.
A deeper technical breakdown of these weaknesses appears in industrial control system security failures
IT and OT Convergence
Operational Technology (OT) systems control physical processes, while IT systems manage data and communications. Historically, these environments were separated.
Today, they are increasingly connected for efficiency and remote management, which:
-
Expands the attack surface
-
Allows IT breaches to cascade into physical systems
-
Makes containment more difficult during incidents
High Impact, Low Tolerance for Failure
Unlike traditional cyber incidents, failures in critical infrastructure:
-
Cannot be easily rolled back
-
May cause safety hazards
-
Can disrupt millions of people simultaneously
This raises the stakes of even minor misconfigurations or delayed responses.
Common Cybersecurity Risks Facing Critical Infrastructure
Remote Access Vulnerabilities
Remote access is often required for maintenance and monitoring, but it introduces risks when:
-
Credentials are reused
-
Multi-factor authentication is missing
-
Access is not properly logged or segmented
Attackers frequently target remote access points as initial entry vectors.
Supply Chain Exposure
Infrastructure operators depend on vendors for hardware, software, and maintenance. Compromised suppliers can unintentionally introduce:
-
Malicious code
-
Insecure updates
-
Hidden backdoors
Supply chain attacks are especially dangerous because they bypass perimeter defenses.
Insider Threats and Human Error
Not all risks come from external attackers.
Common internal risks include:
-
Misconfigured systems
-
Weak passwords
-
Unauthorized changes
-
Inadequate training
In critical environments, small mistakes can have outsized consequences.
How Cyber Risks Turn Into Real-World Disruptions
Cyber incidents do not always start with dramatic failures. Many begin quietly and escalate over time.
Typical progression:
-
Initial access through phishing or exposed services
-
Lateral movement within IT networks
-
Pivoting into OT environments
-
Manipulation or shutdown of physical processes
This progression explains why distinguishing between technical failure and malicious activity is often difficult, as explored in power grid failure vs cyberattack
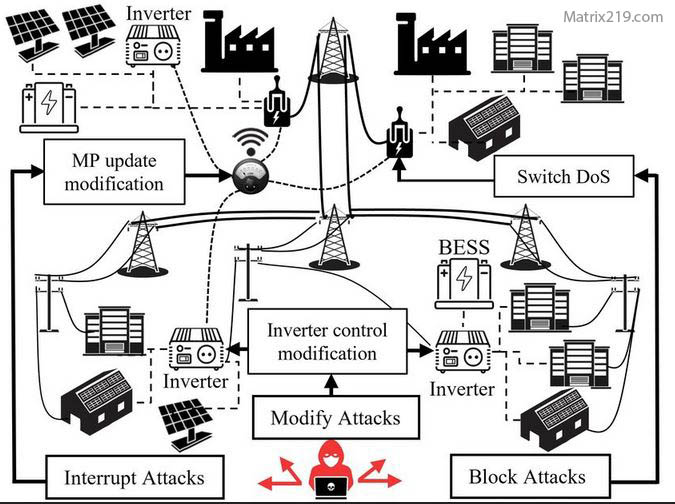
critical infrastructure cybersecurity risks
Why Attribution Matters—but Comes Later
When infrastructure fails, public narratives often focus on who is responsible. However, identifying attackers is complex and time-consuming.
Attribution challenges include:
-
Obfuscated attack paths
-
Shared tools among multiple threat actors
-
Deliberate false-flag techniques
A focused discussion on this issue is covered in cyberattack attribution challenges
The Broader Cybersecurity Risk Landscape
Critical infrastructure risks cannot be isolated from global cyber trends.
Key factors include:
-
Increased geopolitical tension
-
Growth of state-sponsored cyber activity
-
Rising sophistication of attack tools
Understanding these dynamics helps explain why infrastructure systems are frequent targets, as detailed in state-sponsored cyber operations explained
Risk Reduction Is About Resilience, Not Perfection
Eliminating all cyber risks is unrealistic. Instead, infrastructure operators focus on resilience:
-
Early detection
-
Segmentation between IT and OT
-
Incident response planning
-
Controlled system recovery
Practical defensive approaches are discussed further in critical infrastructure cyber defense strategies
Conclusion
Critical infrastructure cybersecurity risks stem from a combination of legacy technology, operational constraints, and growing digital connectivity. These systems were built to prioritize availability, not security, making them attractive targets for both malicious actors and opportunistic attackers.
Understanding how these risks emerge—and how they can escalate into physical disruption—is essential for building realistic defense strategies. As infrastructure continues to modernize, cybersecurity must be treated as a core operational requirement rather than an afterthought.