Cyberattack attribution challenges remain one of the most complex problems in modern cybersecurity. When a major incident occurs—especially one affecting critical infrastructure—the first public question is often: who did it? Yet answering this question accurately can take months, and sometimes it is never fully resolved.
Unlike physical attacks, cyber operations leave fragmented and manipulable traces. Attackers deliberately design their activities to obscure identity, mislead investigators, and exploit political assumptions. This article explains why attribution is so difficult, what evidence is actually required, and why early accusations are often unreliable.
Quick Navigation
What Does Cyberattack Attribution Really Mean?
Attribution is not just identifying a technical source such as an IP address. It involves linking an attack to:
-
A specific threat actor
-
An organization or group
-
In some cases, a nation-state
This process combines technical forensics, intelligence analysis, behavioral patterns, and geopolitical context. Each layer introduces uncertainty and potential error.
These complexities are especially visible in incidents tied to critical infrastructure cybersecurity risks
Why Technical Evidence Alone Is Not Enough
IP Addresses Are Misleading
IP addresses are often:
-
Spoofed
-
Routed through compromised systems
-
Shared by unrelated attackers
Relying on them alone leads to false conclusions.
Malware Reuse Blurs Attribution
Many hacking tools are:
-
Sold on underground markets
-
Leaked publicly
-
Reused by multiple actors
This means the same malware family can appear in unrelated attacks, weakening claims of exclusivity.
False Flags Are a Real Tactic
Some attackers intentionally:
-
Use another group’s tools
-
Mimic known attack patterns
-
Leave misleading language or code artifacts
False-flag operations are especially relevant in incidents involving state-sponsored cyber operations explained
Time Works Against Accurate Attribution
Accurate attribution requires patience.
Investigators must:
-
Reconstruct attack timelines
-
Analyze command-and-control infrastructure
-
Compare activity to historical threat behavior
Rushing this process increases the risk of misattribution, particularly when public pressure is high after service disruptions or outages linked to power grid failure vs cyberattack
Political Pressure Complicates Cyber Attribution
Cyber incidents rarely occur in a political vacuum.
Governments may:
-
Attribute attacks quickly to external actors
-
Frame incidents to support strategic narratives
-
Delay or withhold technical details
This does not mean all claims are false, but it reinforces why independent verification is essential.
Attribution in Critical Infrastructure Incidents
When infrastructure systems fail, attribution becomes even harder because:
-
Technical failures can mimic attack effects
-
Legacy systems lack detailed logging
-
Physical and digital causes overlap
These challenges are amplified in environments affected by industrial control system security failures
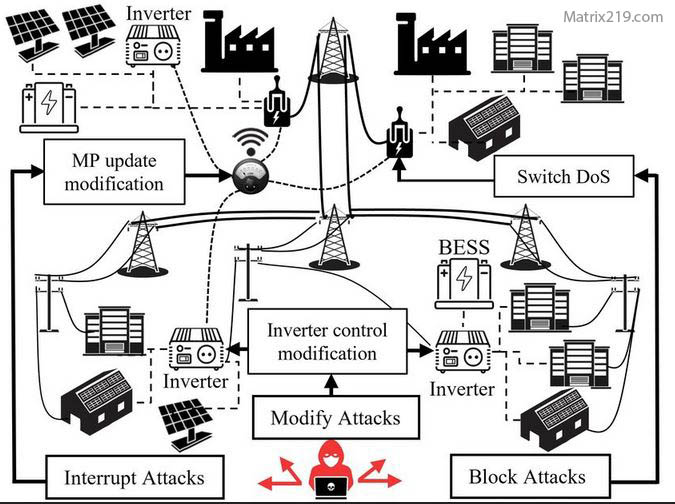
What Responsible Attribution Looks Like
Credible attribution usually includes:
-
Consistent technical indicators across incidents
-
Long-term observation of attacker behavior
-
Corroboration from multiple independent sources
It avoids absolute language and acknowledges uncertainty where evidence is incomplete.
Why Attribution Still Matters
Despite its difficulty, attribution is important because it:
-
Shapes diplomatic responses
-
Influences sanctions and policy decisions
-
Guides defensive prioritization
However, attribution should never overshadow the more urgent goal of resilience and prevention, central to critical infrastructure cyber defense strategies
Conclusion
Cyberattack attribution challenges exist because cyberspace allows attackers to hide, mislead, and manipulate evidence at every stage of an operation. Technical indicators alone are insufficient, and political pressure often distorts early conclusions.
Understanding these limitations is critical when evaluating claims about major cyber incidents. Responsible attribution is slow, cautious, and evidence-driven—anything faster should be treated with skepticism.