The question do hackers bypass free antivirus comes up whenever someone hears about a successful breach despite having protection installed. In 2026, this concern is completely valid. Cyberattacks are no longer crude or obvious—they’re designed to blend in, trick users, and exploit trust rather than smash through technical defenses.
Free antivirus software does stop many attacks—but hackers don’t usually attack antivirus directly. Instead, they work around it. Understanding how and why that happens is critical to knowing what free antivirus can realistically protect against, and where its limits are.
This article explains the real techniques hackers use to bypass free antivirus, what defenses still work, and how to reduce your exposure without relying on false confidence.
For the full protection framework: best free antivirus in 2026
Quick Navigation
What “bypassing antivirus” really means
Hackers rarely disable antivirus outright. Instead, they:
-
Avoid triggering detection
-
Use trusted tools in malicious ways
-
Rely on user actions rather than exploits
So when someone says antivirus was “bypassed,” it often means the attack never looked malicious to begin with.
The most common ways hackers bypass free antivirus
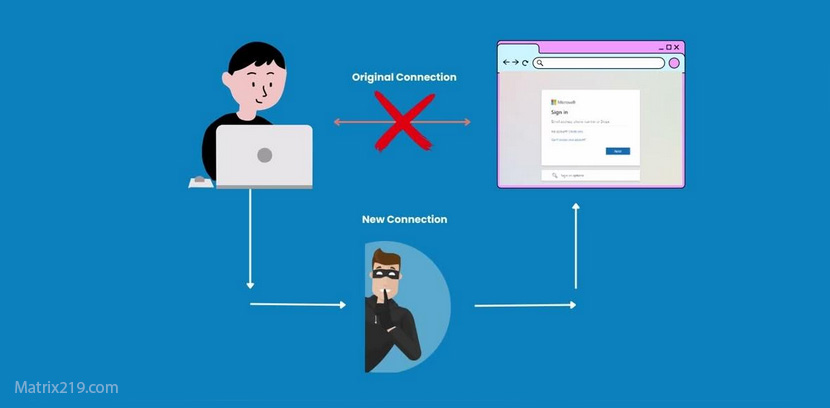
1. Social engineering and phishing
The most effective bypass is still human behavior:
-
Fake emails and login pages
-
Convincing messages urging urgent action
-
Links that lead to credential theft
No antivirus can block a user who willingly enters passwords on a fake site.
2. Legitimate tools used maliciously
Hackers increasingly use:
-
PowerShell and system scripts
-
Built-in admin tools
-
Signed executables
These tools look legitimate, so antivirus may not flag them—especially in free versions with limited behavior analysis.
3. Fileless and memory-based attacks
Some attacks:
-
Don’t write files to disk
-
Operate in memory only
-
Disappear after execution
Free antivirus tools are less effective against these because they rely heavily on file scanning.
4. Delayed or staged execution
Malware may:
-
Stay dormant for hours or days
-
Activate only under specific conditions
-
Download payloads later
This helps attackers evade initial detection, especially from lightweight free tools.
5. User-approved installations
If a user:
-
Installs cracked software
-
Approves security prompts blindly
-
Disables warnings
Antivirus often treats the action as trusted—because the user allowed it.
Free antivirus vs paid tools in bypass scenarios
Paid security solutions often add:
-
Advanced behavioral monitoring
-
Memory and script analysis
-
Ransomware rollback
-
Identity and phishing protection
Free antivirus focuses on blocking known threats, not detecting every evasive tactic.
For that comparison: Free Antivirus Download vs Paid: Real Differences
Built-in OS defenses matter more than you think
Modern operating systems include:
-
Exploit mitigation
-
Credential protection
-
Firewalls and sandboxing
Free antivirus works best when combined with these—not when relied on alone.
For Windows users: Free Antivirus vs Windows Defender in 2026
Why antivirus bypass doesn’t mean failure
It’s important to understand:
-
No antivirus blocks 100% of attacks
-
Successful hacks often involve multiple mistakes
-
Antivirus is one layer, not the whole system
When attackers succeed, it’s rarely due to one failed defense—it’s usually a chain of weak points.
How to reduce bypass risk with free antivirus
You can significantly lower risk by:
-
Avoiding unknown links and attachments
-
Using strong, unique passwords
-
Enabling two-factor authentication
-
Keeping OS and browsers updated
-
Reviewing antivirus alerts carefully
These steps close the gaps hackers rely on.
When free antivirus is still effective
Free antivirus works well against:
-
Known malware
-
Malicious downloads
-
Common trojans and spyware
-
Unsophisticated ransomware
Most everyday threats fall into these categories.
When free antivirus is not enough
It’s not sufficient alone if:
-
You’re a high-value target
-
You manage sensitive business data
-
You reuse passwords
-
You’re frequently exposed to phishing
In these cases, layered security is necessary.
Final answer
So, do hackers bypass free antivirus in 2026?
Yes—but not by breaking it. They bypass it by targeting users, abusing trusted tools, and exploiting behavior gaps. Free antivirus remains effective against common malware, but it cannot replace awareness, strong account security, and system-level defenses.
For a realistic, layered security strategy built around free tools, revisit: best free antivirus in 2026
FAQ
Can hackers completely disable free antivirus?
Rarely. Most attacks avoid detection rather than disabling protection.
Is paid antivirus immune to bypass?
No. It reduces risk but doesn’t eliminate bypass techniques.
Are phishing attacks the biggest weakness?
Yes. Phishing bypasses antivirus by targeting users directly.
Does antivirus protect accounts and passwords?
No. Account security depends on passwords and two-factor authentication.
Is free antivirus useless against hackers?
No. It blocks many common attacks—but it’s not a full security strategy.