As organizations scale, file protection challenges grow exponentially. Enterprise File Encryption Solutions Explained is a common search in 2026 because large organizations face complex environments involving thousands of users, multiple cloud platforms, regulatory pressure, and constant data movement. At this level, basic encryption tools are no longer sufficient. Enterprises need structured systems that enforce policy, provide visibility, and maintain control over encryption keys across the entire organization.
This article explains what truly defines an enterprise-grade file encryption solution, how it differs from small business tools, and which architectural components matter most in real-world deployments. The goal is to help decision-makers understand enterprise encryption beyond vendor buzzwords—focusing instead on control, scalability, and operational resilience.
Quick Navigation
What Makes File Encryption “Enterprise-Grade”
Centralized Governance and Policy Control
Enterprise solutions enforce encryption rules automatically across departments, devices, and locations without relying on individual user decisions.
Organization-Owned Key Infrastructure
Encryption keys are managed by the organization, not end users, ensuring continuity even when staff roles change.
Visibility and Accountability
Enterprises require detailed logs showing who accessed encrypted files, when, and under what conditions.
This foundational difference is outlined in File Encryption Software for Business.
Key Architectural Components of Enterprise Encryption
Centralized Key Management Systems (KMS)
A KMS controls key generation, rotation, revocation, and backup at scale.
Identity and Access Integration
Enterprise encryption integrates with identity providers to enforce role-based access.
Policy Engines
Policies define when files are encrypted, who can decrypt them, and under which scenarios.
Key architecture concepts are grounded in Symmetric vs Asymmetric File Encryption.
How Enterprise File Encryption Works in Practice
Automatic Encryption at Creation
Files are encrypted automatically when created or modified, reducing human error.
Transparent User Experience
Employees access files normally while encryption operates silently in the background.
Secure Decryption Based on Identity
Decryption depends on verified identity and policy compliance, not shared passwords.
A beginner-friendly process overview is available in How File Encryption Works (Beginner Friendly).
Enterprise Encryption Across Hybrid and Cloud Environments
On-Premises and Cloud Coexistence
Enterprise encryption must function consistently across local servers and cloud platforms.
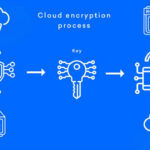
Client-Side Encryption for Cloud Storage
Files are encrypted before reaching cloud providers to maintain key ownership.
Preventing Cloud Vendor Access
Enterprise tools ensure providers never see unencrypted data.
Cloud-specific challenges are discussed in File Encryption for Cloud Storage.
Scalability and Performance at Enterprise Scale
High-Volume File Processing
Enterprise systems must encrypt large datasets without disrupting operations.
Hardware Acceleration and Load Distribution
Modern solutions use hardware support and distributed processing to maintain speed.
Avoiding Bottlenecks
Centralized control should not become a single point of failure.
Performance considerations are often misunderstood and addressed in Is File Encryption Really Secure?
Compliance and Regulatory Alignment
Meeting Legal Encryption Requirements
Enterprises must comply with data protection laws across multiple jurisdictions.
Audit Trails and Reporting
Detailed logs support audits and regulatory reviews.
Key Custody and Legal Responsibility
Who controls encryption keys determines legal accountability.
Many enterprise evaluations align with NIST encryption standards to validate encryption strength and operational controls.
Common Challenges in Enterprise Encryption Deployments
Over-Complex Policy Design
Too many rules can create confusion and operational friction.
Poor Change Management
Encryption systems must adapt smoothly to organizational changes.
Ignoring User Experience
Excessive friction encourages users to bypass security controls.
These pitfalls are frequently discussed in Common File Encryption Mistakes to Avoid.
Enterprise Encryption vs Small Business Solutions
Scale and Automation
Enterprise solutions prioritize automation, while small business tools rely more on manual control.
Governance Depth
Large organizations require stronger enforcement and reporting.
Long-Term Sustainability
Enterprise systems are designed for years of continuous operation.
A pricing and capability comparison is explored in Free vs Paid File Encryption Software.

Free vs Paid File Encryption Software
How to Evaluate Enterprise File Encryption Solutions
Assess Organizational Risk
Identify which data types require the highest protection.
Test Policy Flexibility
Encryption must adapt to changing roles and workflows.
Validate Recovery and Continuity Plans
Key escrow and recovery must be defined clearly.
A complete evaluation framework is provided in Best File Encryption and Decryption Software in 2026 (Complete Guide).
Frequently Asked Questions (FAQ)
Is enterprise file encryption only for large corporations?
No. Any organization with complex data workflows can benefit from enterprise features.
Do enterprise solutions replace disk encryption?
No. They complement disk encryption by protecting files beyond device boundaries.
Can enterprise encryption slow down large teams?
Not when implemented correctly with modern architecture.
Who should manage encryption keys in an enterprise?
Key management should be handled by designated security or IT teams.
Are enterprise encryption systems difficult to maintain?
Modern solutions are designed for automation and scalability.