Regulatory pressure has made encryption a legal and operational requirement rather than a best practice. In 2026, organizations handling personal, medical, or financial data must understand how encryption fits into compliance obligations. File Encryption Compliance (GDPR, HIPAA Explained) addresses a common point of confusion: when encryption is required, what “compliant encryption” actually means, and how mistakes in key management can still lead to violations.
This article explains encryption requirements under major regulations in practical terms. Instead of legal jargon, the focus is on how file encryption supports compliance, where it falls short, and how organizations should structure encryption programs to reduce regulatory risk without overengineering solutions.
Quick Navigation
Why Regulations Emphasize File Encryption
Encryption Reduces Breach Impact
Many regulations treat encryption as a safeguard that limits damage when data is exposed.
Files Are a High-Risk Data Format
Files are easily copied, emailed, and stored outside controlled systems.
Legal Accountability Depends on Data Protection Controls
Encryption often determines whether an incident is classified as a reportable breach.
This broader risk context is explained in Best File Encryption and Decryption Software in 2026 (Complete Guide).
How GDPR Views File Encryption
Encryption as a Recommended Safeguard
GDPR does not mandate encryption in all cases but strongly encourages it for protecting personal data.
Impact on Breach Notification
Properly encrypted files may reduce or eliminate mandatory breach notifications.
Key Control and Data Ownership
Organizations must control encryption keys to claim protection benefits.
These principles are often misunderstood and linked to poor practices discussed in Common File Encryption Mistakes to Avoid.
How HIPAA Treats File Encryption
Encryption as an Addressable Requirement
HIPAA expects encryption for electronic protected health information unless a justified alternative is documented.
File-Level Encryption for Medical Records
Files containing patient data must remain protected across devices and storage systems.
Audit and Access Controls
Encryption alone is insufficient without logging and access monitoring.
Business-focused requirements are covered in File Encryption Software for Business.
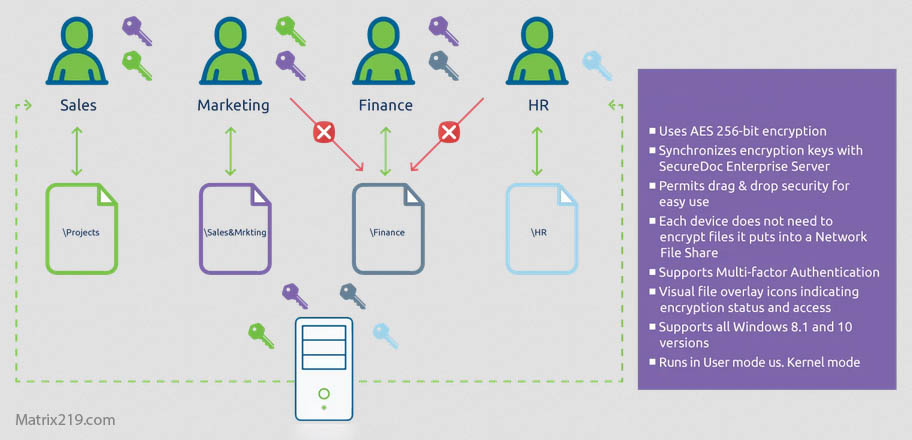
File Encryption Software for Business
Common Compliance Myths About File Encryption
“Using Encryption Automatically Means Compliance”
Encryption supports compliance but does not guarantee it.
“Any Encryption Is Good Enough”
Weak algorithms or poor key handling can still violate regulations.
“Cloud Encryption Solves Everything”
Provider-managed encryption may not meet regulatory expectations.
These misconceptions often lead to compliance failures.
Key Management and Compliance Risk
Who Controls the Encryption Keys
Regulators focus heavily on key custody and access authority.
Key Rotation and Revocation
Stale or shared keys weaken compliance claims.
Backup and Recovery Planning
Key loss can disrupt access to regulated data, creating operational risk.
Key-related failures are detailed in What Happens If You Lose an Encryption Key?
File Encryption in Regulated Cloud Environments
Encrypting Files Before Upload
Client-side encryption ensures providers cannot access regulated data.
Managing Access Across Teams
Compliance requires consistent enforcement of access rules.
Auditability in Cloud Workflows
Organizations must track access to encrypted files across environments.
Cloud-specific challenges are discussed in File Encryption for Cloud Storage.
Documentation and Evidence for Compliance
Proving Encryption Is in Place
Organizations must document how files are encrypted and protected.
Demonstrating Key Control
Evidence should show who can decrypt files and under what conditions.
Incident Response Records
Encryption procedures must be included in breach response plans.
These requirements often determine audit outcomes.
Aligning Encryption With Regulatory Frameworks
Many compliance programs evaluate encryption practices against guidelines such as NIST encryption standards to assess algorithm strength, key management, and operational controls.
When File Encryption Is Not Enough for Compliance
Lack of Access Logging
Encryption without audit trails is insufficient.
Weak Identity Management
Unauthorized access may still occur despite encryption.
Poor User Training
Human error remains a major compliance risk.
Encryption must be part of a broader governance strategy.
How Organizations Should Approach Compliance-Driven Encryption
Start With Data Classification
Identify which files fall under regulatory scope.
Apply Encryption Consistently
Automate encryption for regulated file types.
Review and Update Regularly
Compliance requirements evolve and must be revisited.
A full planning framework is provided in Enterprise File Encryption Solutions Explained.
Frequently Asked Questions (FAQ)
Does GDPR require file encryption?
Not always, but it strongly recommends it for protecting personal data.
Is encryption mandatory under HIPAA?
It is an addressable requirement and often expected for sensitive health data.
Can encrypted files reduce breach penalties?
Yes, if encryption and key control are implemented correctly.
Who should manage encryption keys for compliance?
The organization—not individuals—must retain control.
Is cloud encryption enough for compliance?
Only if key ownership, access control, and auditing requirements are met.





