Legal and financial documents represent some of the highest-risk data any individual or organization can handle. Contracts, court filings, tax records, bank statements, investment reports, and client financial data are all prime targets for theft, manipulation, and unauthorized disclosure. In 2026, File Encryption for Legal and Financial Documents is no longer a “best practice” — it is a baseline requirement for risk management, confidentiality, and regulatory survival.
This article explains how file encryption should be applied specifically to legal and financial documents, why generic encryption setups often fail in these contexts, and what security characteristics actually matter. The focus is on real-world handling: document sharing, long-term storage, audits, disputes, and recovery scenarios. Understanding these factors helps prevent irreversible mistakes that can lead to legal liability or financial loss.
Quick Navigation
Why Legal and Financial Files Require Special Protection
High Confidentiality and Legal Consequences
Unauthorized access can result in lawsuits, regulatory penalties, or loss of client trust.
Long Retention Periods
Legal and financial documents are often stored for years, increasing key-management risk.
Frequent Sharing With Third Parties
Lawyers, accountants, auditors, courts, and banks regularly exchange sensitive files.
This risk profile is very different from personal or low-sensitivity data.
Common Threats to Legal and Financial Documents
Unauthorized Internal Access
Not all breaches come from outsiders; insider access misuse is common.
Accidental Disclosure
Mis-sent emails and incorrect cloud permissions expose sensitive documents daily.
External Breaches and Account Takeovers
Compromised email or cloud accounts can expose entire document archives.
These scenarios are often underestimated and linked to failures discussed in Is File Encryption Really Secure?
Why File-Level Encryption Is Critical for These Documents
Protection Beyond Devices and Platforms
File encryption keeps documents protected even after they leave secure systems.
Independence From Storage Location
Encrypted documents remain secure whether stored locally, in the cloud, or on external drives.
Legal Defensibility
Proper encryption can significantly reduce liability after an incident.
A foundational comparison is explained in File Encryption vs Disk Encryption.
Encryption Requirements Specific to Legal Documents
Client-Attorney Confidentiality
Encryption helps preserve privilege by preventing unauthorized disclosure.
Secure Document Exchange
Encrypted files protect sensitive filings during transfer between parties.
Court and Regulatory Submissions
Files must remain intact and unaltered while protected.
Encryption workflows for professionals are grounded in File Encryption Software for Business.
Encryption Requirements Specific to Financial Documents
Protection Against Fraud and Identity Theft
Financial files are prime targets for misuse and impersonation.
Regulatory Oversight
Financial data is often subject to audits and retention rules.
Controlled Access and Traceability
Organizations must know who accessed which files and when.
Compliance implications are discussed in File Encryption Compliance (GDPR, HIPAA Explained).
Key Management Challenges in Legal and Financial Contexts
Long-Term Key Retention
Keys must remain accessible for years without being exposed.
Access Revocation Without Data Loss
Access should be removable without re-encrypting entire archives.
Disaster and Recovery Planning
Lost keys can permanently destroy access to critical records.
Key-loss consequences are detailed in What Happens If You Lose an Encryption Key?
Secure File Sharing for Legal and Financial Documents
Encrypt Before Sending
Documents should always be encrypted before email or upload.
Separate Key Distribution
Encryption keys must never travel with the document itself.
Time-Limited Access
Whenever possible, access should expire automatically.
Secure sharing challenges are also covered in File Encryption for Cloud Storage.
Common Encryption Mistakes in Legal and Financial Workflows
Using Consumer Tools for Professional Data
Personal encryption tools lack auditability and recovery features.
Storing Keys With Files
This defeats encryption entirely and increases legal exposure.
Overreliance on Cloud Provider Security
Provider encryption rarely meets professional confidentiality standards.
These mistakes are repeatedly observed in Common File Encryption Mistakes to Avoid.
Performance and Usability Considerations
Handling Large Document Archives
Encryption must scale without slowing retrieval during audits or disputes.
Minimizing Workflow Disruption
Security should not encourage staff to bypass encryption.
Balancing Security With Accessibility
Encrypted documents must remain usable under pressure.
Performance trade-offs are often misunderstood and discussed in Best File Encryption and Decryption Software in 2026 (Complete Guide).
Compliance and Audit Readiness
Demonstrating Encryption Controls
Organizations must prove files are encrypted and access-controlled.
Logging and Evidence
Audit trails are essential for regulatory and legal review.
Key Custody Documentation
Clear ownership of keys determines accountability.
Many compliance evaluations align encryption practices with NIST encryption standards to assess adequacy.
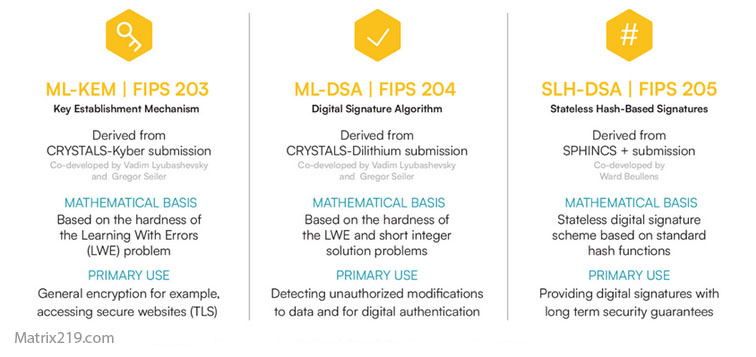
NIST encryption standards
When Stronger Controls Are Required
Large Law Firms and Financial Institutions
High data volume demands centralized encryption management.
Cross-Border Document Handling
Jurisdictional exposure increases risk significantly.
Litigation and Dispute Scenarios
Encryption mistakes can undermine legal positions.
Enterprise-level solutions are discussed in Enterprise File Encryption Solutions Explained.
Frequently Asked Questions (FAQ)
Are legal documents required to be encrypted?
In many jurisdictions and professional contexts, yes—especially during storage and transfer.
Is password protection enough for financial files?
No. Password protection does not provide the same level of security as encryption.
Can encrypted documents be used as legal evidence?
Yes, if integrity and access controls are maintained properly.
What happens if an encryption key is lost?
Access to the document may be permanently lost, creating serious legal risk.
Should encryption be automated for these documents?
Yes. Automation reduces human error in high-risk workflows.





