Identity Theft Scams go beyond immediate financial loss. In 2026, stolen personal data is used strategically—sometimes months or years later—to open accounts, impersonate victims, bypass security checks, and enable long-term fraud.
Unlike one-time scams, identity theft creates ongoing risk. Victims may not realize their identity has been abused until credit problems, legal notices, or account denials appear.
This article explains how identity theft scams work, how data is misused after theft, and how to reduce long-term damage before control is lost.
What Identity Theft Really Means
Identity theft is not just stealing information—it is abusing it.
Criminals use personal data to impersonate victims across financial, legal, and digital systems. Even partial data can be combined with other leaks to construct convincing identities.
Identity theft is cumulative.
How Criminals Obtain Identity Data
Identity data is gathered from many sources.
Common sources include data breaches, phishing, fake job applications, recovery scams, fake websites, and malicious apps. Small pieces from different incidents are often combined.
No single leak tells the whole story.
The Most Abused Types of Personal Data
Certain data points are especially valuable.
These include:
-
Full names and addresses
-
Phone numbers and email addresses
-
National IDs or tax numbers
-
Banking or card details
-
Account recovery information
The more complete the profile, the broader the abuse.
How Stolen Identities Are Used
Once data is collected, criminals act strategically.
They may open credit accounts, apply for loans, take over existing accounts, commit tax fraud, redirect benefits, or impersonate victims in scams targeting others.
Some identities are “aged” before use to avoid detection.
Synthetic Identity Fraud
One growing trend is synthetic identity fraud.
Criminals combine real and fake data to create new identities that pass basic checks. These identities may be used for years before being detected.
Victims may never know their data contributed.
Early Warning Signs of Identity Theft
Identity theft often surfaces indirectly.
Warning signs include unexpected bills, credit denials, unfamiliar accounts, tax notices, benefit disruptions, or authentication alerts for services you never used.
Silence does not mean safety.
What To Do If You Suspect Identity Theft
Immediate containment matters.
Key steps include:
-
Securing primary email and phone accounts
-
Changing passwords and recovery options
-
Reviewing credit reports and account activity
-
Placing fraud alerts or credit freezes where available
Delay increases downstream damage.
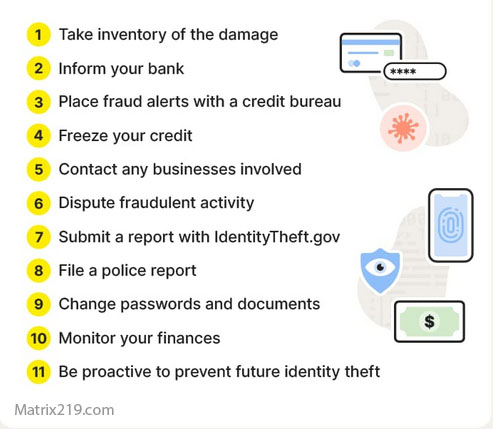
What To Do If You Suspect Identity Theft
Long-Term Recovery and Monitoring
Identity recovery is not instant.
Victims may need to monitor credit, dispute fraudulent accounts, update records, and remain alert for secondary fraud attempts.
Persistence—not panic—drives recovery.
Why Identity Theft Often Leads to More Scams
Once identified as a victim, individuals may be targeted again.
Criminals test what still works—accounts, contacts, payment methods. Awareness after identity theft is critical.
The first incident is rarely the last.
Preventing Identity Theft Proactively
Effective prevention includes:
-
Limiting data exposure online
-
Verifying requests for personal information
-
Avoiding unnecessary form submissions
-
Securing accounts and recovery channels
-
Monitoring financial and identity signals
Prevention reduces surface area—not just threats.
Identity Theft in the Larger Fraud Ecosystem
Identity theft enables many other scams: account takeover, BEC, payment fraud, and impersonation.
Understanding identity abuse strengthens defenses across the entire fraud spectrum.
For the full fraud framework this article supports, see: Online Scams & Digital Fraud: How to Spot, Avoid, and Recover (2026 Guide)
FAQ
Can identity theft happen without financial loss?
Yes. Damage may appear later or indirectly.
Is partial data enough for identity theft?
Often yes, when combined with other leaks.
Should I freeze my credit permanently?
It depends, but freezes are effective risk controls.
Are identity theft services reliable?
Some help with monitoring—not prevention.
Can identity theft be fully reversed?
Rarely. Ongoing management is often required.