Mobile Privacy & Spyware Detection has become one of the most critical digital security concerns in 2026. Smartphones are no longer simple communication tools. They store personal conversations, financial data, location history, authentication codes, and intimate details of daily life. This concentration of sensitive data has made mobile devices a prime target for surveillance, spyware, and covert monitoring.
Unlike traditional malware, modern spyware is designed to remain invisible. It operates silently in the background, harvesting data without noticeable performance issues or obvious warning signs. Many users assume that mobile surveillance is rare or limited to high-profile targets, but the reality is that commercial spyware, stalkerware, and data-harvesting apps are increasingly accessible and widely deployed.
This pillar guide explains how mobile surveillance works, how spyware infects phones, how to detect early warning signs, and how users can realistically protect their devices without relying on false promises of total immunity. This topic is closely connected to broader digital tracking and privacy risks.
Quick Navigation
What Mobile Spyware Really Is
Mobile spyware is software designed to secretly monitor activity on a smartphone. Its purpose is data extraction rather than device damage. Unlike typical malware, spyware aims to remain persistent, discreet, and difficult to detect.
Spyware can collect messages, call logs, photos, location data, microphone recordings, camera access, and app usage patterns. Some advanced variants can intercept encrypted messages before encryption or after decryption, bypassing user expectations of secure communication.
How Phones Become Infected With Spyware
Spyware does not always rely on technical exploits. In many cases, infection occurs through social engineering, deceptive apps, or physical access.
Common infection paths include malicious app installations, sideloaded software, compromised app updates, phishing links, and unauthorized physical access to unlocked devices. In some scenarios, spyware is installed intentionally by someone with legitimate access to the phone, such as a partner, employer, or family member.
Understanding these vectors is essential because prevention depends more on behavior and awareness than on tools alone.
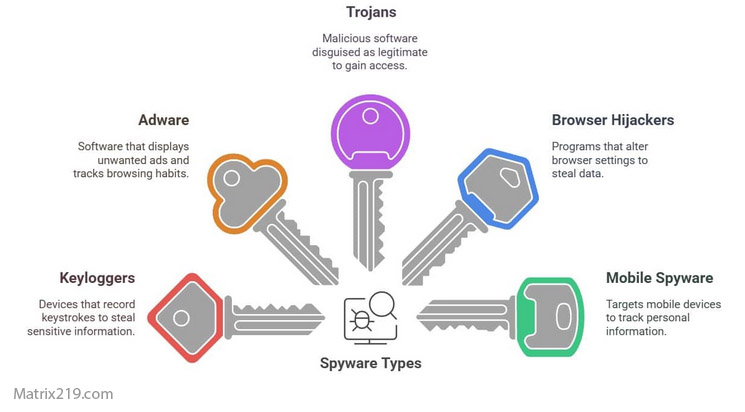
Types of Mobile Surveillance Threats
Not all mobile surveillance is the same. Threats range from consumer-grade stalkerware to highly advanced commercial spyware.
Stalkerware is often marketed as monitoring or parental control software but is misused for covert surveillance. Commercial spyware is more sophisticated and may exploit system-level vulnerabilities. Additionally, some surveillance occurs through excessive app permissions, analytics SDKs, or operating system telemetry rather than explicit spyware.
Distinguishing between these categories helps users assess risk realistically rather than assuming all threats are equal.
Warning Signs of Spyware on a Phone
Spyware is designed to avoid detection, but subtle indicators can appear. These may include unexplained battery drain, abnormal data usage, device overheating during idle periods, or unexpected permission behavior.
Other signs include system settings being altered without user action, unfamiliar apps with generic names, or security features being disabled. However, absence of symptoms does not guarantee absence of surveillance, which is why detection requires structured checks rather than guesswork.
Why Mobile Privacy Is Harder Than Desktop Privacy
Mobile operating systems are more restrictive, which improves security but reduces transparency. Users have limited visibility into background processes, network activity, and system-level behavior.
Phones are also always connected, always carried, and deeply integrated into daily routines. Location tracking, sensor access, and persistent identifiers make mobile devices uniquely valuable for surveillance compared to desktops or laptops.
This combination makes mobile privacy protection fundamentally different from browser-based privacy strategies.
Built-In Protections and Their Limits
Modern mobile operating systems include sandboxing, permission systems, and app store review processes. These protections reduce risk but do not eliminate it.
Permission fatigue, vague consent prompts, and pre-installed system apps weaken practical control. Some spyware abuses accessibility features, device admin privileges, or configuration profiles to maintain persistence without triggering alarms.
Relying solely on default protections creates a false sense of security if users do not actively manage settings.
Spyware Detection: What Actually Works
Effective spyware detection focuses on structural checks rather than single “scan and trust” solutions. Reviewing app permissions, checking device admin access, auditing accessibility services, and monitoring profile installations are more reliable than generic antivirus claims.
Behavioral analysis, system integrity checks, and update verification play a bigger role than signature-based detection alone. Detection is a process, not a one-time action.
This pillar will be supported by detailed cluster articles covering hands-on detection steps for different platforms.
Spyware Installed Through Physical Access
Protecting Your Phone From Surveillance
Mobile protection starts with reducing attack surfaces. This includes limiting app installations, avoiding sideloading, locking devices with strong authentication, and keeping systems updated.
Separating sensitive activity, reviewing permissions regularly, and understanding how apps interact with system features significantly reduces exposure. Physical security matters as much as digital security when it comes to mobile surveillance.
Protection is about reducing feasibility, not chasing impossible guarantees.
High-Risk Scenarios for Mobile Surveillance
Certain situations increase risk significantly. These include shared devices, domestic disputes, workplace monitoring, travel through hostile environments, and use of unofficial app sources.
In high-risk contexts, additional precautions are necessary, including device resets, account hygiene, and reassessment of trust assumptions. Threat models matter more than tools.
Legal and Ethical Boundaries of Mobile Surveillance
Mobile surveillance exists in a complex legal landscape. Some monitoring software is legal under specific conditions, while covert installation often violates privacy laws.
Users should understand that legality does not equal safety. Even legally installed monitoring tools can be abused or misconfigured, leading to serious privacy violations.
Realistic Expectations About Mobile Privacy
No smartphone can be made perfectly private. Hardware, operating systems, and networks impose unavoidable constraints.
The realistic goal is minimizing exposure, detecting abnormal behavior early, and maintaining control over permissions and access. Users who understand these limits are far less likely to fall for exaggerated claims or ineffective solutions.
FAQ
What is mobile spyware in simple terms?
It is software that secretly monitors phone activity to collect data without the user’s knowledge.
Can spyware exist without obvious symptoms?
Yes. Many spyware tools are designed to remain invisible and silent.
Do antivirus apps detect all mobile spyware?
No. Some spyware avoids signature detection and requires manual checks.
Is mobile surveillance only used by governments?
No. Commercial and consumer-grade spyware is widely available.
Can a factory reset remove spyware?
Often yes, but not always if configuration profiles or backups are compromised.



