OT vs IT security in critical infrastructure is a distinction that is often misunderstood, yet it plays a decisive role in how cyber risks turn into real-world disruptions. While IT security focuses on protecting data, users, and applications, Operational Technology (OT) security is concerned with controlling physical processes that must operate continuously and safely.
Treating OT environments like traditional IT systems is one of the most common mistakes in infrastructure protection. The differences between the two are not cosmetic—they affect priorities, risk tolerance, incident response, and even how security controls are deployed. This article explains how OT and IT security differ, why those differences matter, and how misalignment creates dangerous gaps in critical infrastructure defense.
Quick Navigation
What Is IT Security?
IT security focuses on protecting information systems that handle:
-
Business data
-
User identities
-
Applications and services
-
Communication networks
Core IT security priorities include:
-
Confidentiality of data
-
Integrity of systems
-
Availability of services
In most IT environments, systems can tolerate downtime, patches can be applied frequently, and security controls can be aggressive without causing physical harm.
What Is OT Security?
OT security protects systems that monitor and control physical processes, such as:
-
Power generation and distribution
-
Water treatment
-
Manufacturing lines
-
Transportation signaling
OT environments rely heavily on industrial control technologies and are deeply affected by industrial control system security failures
In OT, availability and safety take precedence over all other considerations. Even short interruptions can lead to equipment damage or safety risks.
Core Differences Between OT and IT Security
Availability vs Confidentiality
-
IT security often prioritizes protecting sensitive data.
-
OT security prioritizes keeping systems running safely at all times.
Shutting down an OT system to “contain a threat” may create a larger physical incident than the threat itself.
System Lifecycles
IT systems typically refresh every few years.
OT systems may remain in service for decades.
This long lifespan contributes directly to critical infrastructure cybersecurity risks
Patch and Update Constraints
In IT:
-
Patching is routine
-
Downtime is manageable
In OT:
-
Patching may require full shutdowns
-
Updates are delayed to avoid operational impact
This leaves OT environments exposed to known vulnerabilities for extended periods.
Why Applying IT Security Models to OT Often Fails
Traditional IT security tools may:
-
Generate excessive false alerts
-
Block legitimate operational traffic
-
Interfere with real-time control
When misapplied, these tools can cause failures that resemble malicious activity, complicating investigations into power grid failure vs cyberattack
Network Architecture Differences
IT networks are typically:
-
Highly segmented
-
Centrally managed
-
Designed for scalability
OT networks are often:
-
Flat or loosely segmented
-
Designed for reliability
-
Difficult to re-architect
This architectural gap allows breaches in IT environments to cascade into OT systems if not properly controlled.
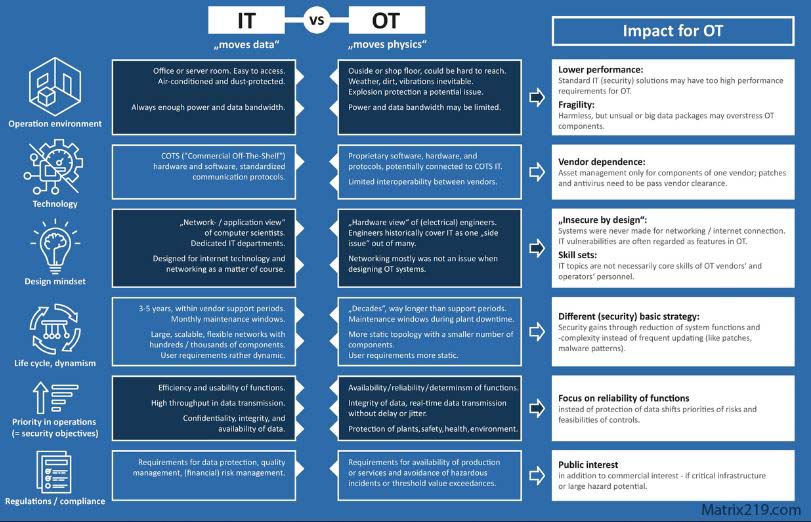
OT vs IT security in critical infrastructure
Incident Response: IT vs OT Reality
In IT incidents, standard responses include:
-
Isolating systems
-
Taking services offline
-
Reimaging affected machines
In OT incidents, these actions may:
-
Disrupt physical processes
-
Create safety hazards
-
Trigger widespread outages
This is why OT incident response must be planned differently and aligned with critical infrastructure cyber defense strategies
OT and IT Security in the Context of Advanced Threats
Nation-state and advanced actors understand these differences and exploit them. OT environments are attractive because:
-
Detection is harder
-
Recovery is slower
-
Impact is higher
This dynamic is consistent with patterns seen in state-sponsored cyber operations explained
Bridging the Gap Between OT and IT Security
Effective protection does not mean merging OT and IT security blindly. Instead, it requires:
-
Clear governance and responsibility boundaries
-
Controlled interfaces between IT and OT
-
Security tools designed specifically for OT
-
Cross-team coordination and training
Bridging this gap reduces both accidental failures and targeted attacks.
Conclusion
OT vs IT security in critical infrastructure is not a theoretical distinction—it defines how cyber risks translate into physical consequences. Treating OT systems like IT environments introduces more danger than protection, while ignoring security altogether is no longer viable.
Understanding and respecting the differences between OT and IT security is essential for building resilient infrastructure defenses that protect both digital systems and the physical world they control.