Recovering encrypted files is one of the most misunderstood topics in data security. In 2026, How to Recover Encrypted Files is searched by users facing urgent situations—forgotten passwords, lost keys, corrupted drives, or failed systems. The hard truth is that recovery depends far more on how encryption was implemented than on any recovery tool or trick.
This article explains when encrypted files can be recovered, when recovery is technically impossible, and what practical steps actually make a difference. The focus is on realistic outcomes, not false hope. By understanding the recovery boundaries upfront, you can respond correctly during incidents—and design encryption workflows that remain recoverable when recovery is legitimately required.
Quick Navigation
What “Recovery” Means in Encrypted File Scenarios
Recovery Is Not Cracking Encryption
Proper encryption cannot be bypassed or broken to regain access.
Recovery Depends on Key Availability
Access is restored only if valid keys, passwords, or escrow mechanisms exist.
Why Expectations Are Often Wrong
Many users confuse encrypted files with locked accounts or compressed archives.
This misunderstanding causes panic and poor decisions during incidents.
When Encrypted Files Can Be Recovered
You Still Have the Correct Key or Password
Recovery is immediate once valid credentials are supplied.
A Key Backup Exists
Securely backed-up keys enable restoration on new or repaired systems.
Managed or Escrow-Based Encryption Is Used
Organizations may recover access through controlled key escrow.
These models are compared in Best File Encryption Software Compared (2026).
When Encrypted Files Cannot Be Recovered
The Key Is Permanently Lost
Strong encryption intentionally provides no fallback.
The Encryption Tool Stores No Recovery Data
Reputable tools do not keep copies of user keys.
The Files Were Encrypted Correctly
Ironically, proper encryption guarantees irreversibility without keys.
This outcome is explained in detail in What Happens If You Lose an Encryption Key?
Common Recovery Scenarios and What Actually Works
System Reinstallation or Hardware Failure
Files are recoverable only if keys were stored separately.
Forgotten Passwords
Password recovery is impossible unless a recovery mechanism was configured.
Corrupted Encrypted Files
Recovery may be possible if corruption occurred outside the encrypted payload.
Each scenario depends on prior preparation.
The Role of Backups in Encrypted File Recovery
Backups Preserve Encrypted Data—Not Access
Without keys, backups do not restore usability.
Key Backups Are More Important Than File Backups
Keys must be protected with the same seriousness as the data itself.
Testing Recovery Before It’s Needed
Untested backups often fail during real incidents.
Backup planning is part of a broader strategy discussed in Best File Encryption and Decryption Software in 2026 (Complete Guide)
Recovery in Business and Enterprise Environments
Centralized Key Management
Organizations can recover access through policy-based controls.
Role-Based Recovery Authorization
Recovery actions require documented approval and logging.
Avoiding Single-Person Dependency
No individual should be the sole holder of critical encryption keys.
Enterprise recovery models are covered in Centralized File Encryption Management Systems.
What Not to Do When Encrypted Files Are Inaccessible
Do Not Trust “Decryption” or “Cracking” Tools
They do not work against proper encryption and may introduce malware.
Do Not Modify Encrypted Files Randomly
This can permanently damage recoverable data.
Do Not Assume Vendors Can Help
Encryption vendors cannot recover user-owned keys by design.
Red flags for fake recovery claims are discussed in Signs Your File Encryption Software Is Fake.
File Corruption vs Encryption Loss
Corruption Outside the Encrypted Payload
Some files can be restored if only headers or containers are damaged.
Corruption Inside Encrypted Data
Recovery is usually impossible without the correct key.
Why Integrity Checks Matter
Tools that verify integrity reduce irreversible damage.
This distinction is often overlooked during panic-driven recovery attempts.
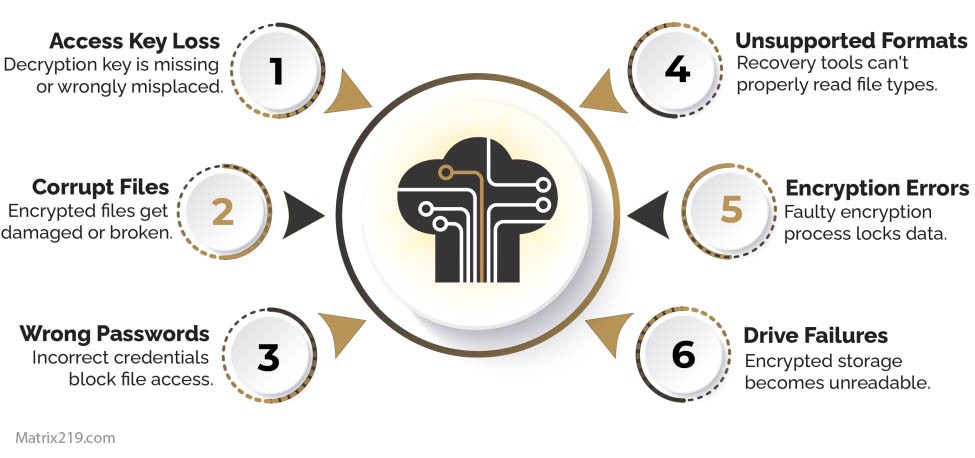
File Corruption vs Encryption Loss
Cloud Storage and Encrypted File Recovery
Client-Side Encrypted Files
Cloud providers cannot assist with decryption.
Account Recovery Does Not Equal File Recovery
Regaining account access does not restore encryption keys.
Backup Copies Share the Same Limitation
All encrypted copies fail together without keys.
Cloud-related risks are explained in File Encryption for Cloud Storage.
How to Design Encryption for Recoverability
Decide If Recovery Is Required
Not all data should be recoverable by design.
Separate Encryption From Access Control
Use recovery mechanisms without weakening encryption.
Document Recovery Procedures
Clear documentation prevents mistakes under pressure.
This planning is essential for professional environments.
Standards and Security Reality
Security frameworks aligned with NIST encryption standards explicitly assume that recovery without keys is impossible and must be addressed through policy—not cryptography.
Frequently Asked Questions (FAQ)
Can encrypted files be recovered without the key?
No. Proper encryption makes this mathematically impossible.
Do recovery tools work on encrypted files?
No. Claims to “crack” encryption are misleading or malicious.
Can backups restore encrypted files?
Only if the encryption keys are also available.
Is key escrow a security risk?
It can be if poorly controlled, but it enables recovery when required.
Should everyone plan for encrypted file recovery?
Yes—either to enable it intentionally or to accept permanent loss.