Remote access risks in energy infrastructure have grown significantly as utilities adopt digital tools to improve efficiency, monitoring, and maintenance. Remote connectivity allows engineers and vendors to manage systems without being physically present, reducing costs and response times. However, it also introduces one of the most exploited entry points in critical infrastructure cyber incidents.
Many major infrastructure breaches begin not with sophisticated exploits, but with poorly secured remote access. When attackers gain remote footholds, they can move quietly through networks that control physical processes. This article explains why remote access is so risky in energy environments, how these risks materialize, and what makes them difficult to control.
Quick Navigation
Why Energy Infrastructure Relies on Remote Access
Energy infrastructure depends on remote access for:
-
Monitoring substations and control centers
-
Vendor maintenance and troubleshooting
-
Emergency response and outage recovery
-
Managing geographically distributed assets
These capabilities are essential, but they also expand exposure across systems already affected by critical infrastructure cybersecurity risks
Common Forms of Remote Access in Energy Systems
Remote access in energy environments typically includes:
-
VPN connections for operators and engineers
-
Remote desktop access to control systems
-
Vendor-managed access portals
-
Cellular and satellite connections to field devices
Many of these pathways intersect directly with environments impacted by industrial control system security failures
Why Remote Access Is a High-Risk Vector
Weak Authentication Practices
Remote access systems often rely on:
-
Single-factor authentication
-
Shared or reused credentials
-
Static passwords that rarely change
Once credentials are compromised, attackers can access systems without triggering alarms.
Overprivileged Access
Remote users frequently receive broader access than necessary to simplify operations. This creates situations where:
-
One account controls multiple systems
-
Access boundaries are poorly defined
-
Compromise leads to disproportionate impact
These conditions make it harder to differentiate between misuse and legitimate activity, complicating power grid failure vs cyberattack
Persistent Access Paths
Remote access channels are often left enabled indefinitely.
This persistence allows attackers to:
-
Maintain long-term access
-
Return after initial detection
-
Bypass perimeter defenses repeatedly
Such persistence plays a role in prolonged incidents that later raise cyberattack attribution challenges
Vendor Remote Access: An Overlooked Risk
Third-party vendors frequently require remote access to:
-
Perform updates
-
Diagnose faults
-
Support legacy systems
However, vendor access is often:
-
Poorly monitored
-
Shared across customers
-
Insufficiently segmented
This creates indirect attack paths into energy infrastructure, especially when vendors themselves are compromised.
Remote Access and Nation-State Threats
Advanced threat actors actively seek remote access pathways because:
-
They provide legitimate-looking entry
-
Activity blends into normal operations
-
Detection thresholds are higher
Remote access exploitation aligns with techniques commonly associated with state-sponsored cyber operations explained
Why Detecting Remote Access Abuse Is Difficult
Energy environments face unique detection challenges:
-
Limited logging in OT systems
-
Lack of baseline behavior profiles
-
Operational constraints that limit monitoring tools
As a result, remote access abuse may go unnoticed until physical effects appear.
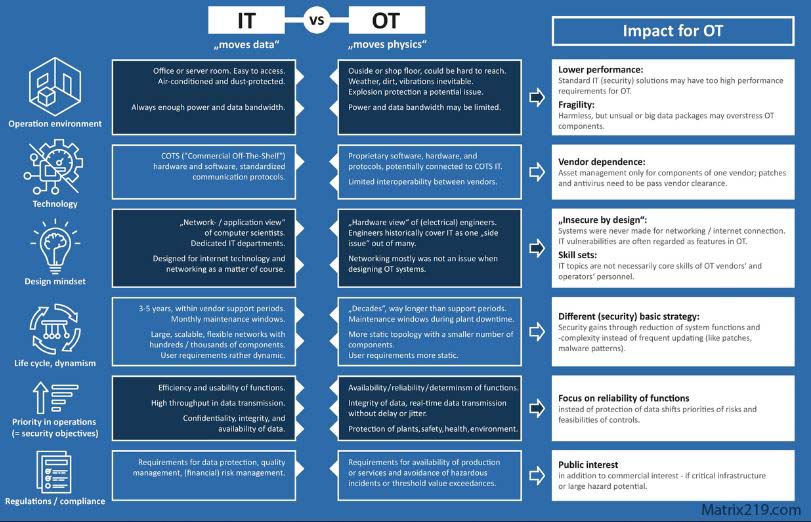
Reducing Remote Access Risks Without Disrupting Operations
Effective mitigation focuses on control rather than elimination.
Key strategies include:
-
Multi-factor authentication for all remote access
-
Time-limited and role-based access
-
Network segmentation between remote access points and OT systems
-
Continuous monitoring of remote sessions
These controls are core elements of critical infrastructure cyber defense strategies
Remote Access as a Risk Multiplier
Remote access rarely causes incidents alone. Instead, it amplifies:
-
Legacy system weaknesses
-
Human error
-
Poor network segmentation
When combined, these factors turn small access issues into large-scale disruptions.
Conclusion
Remote access risks in energy infrastructure represent one of the most practical and dangerous cyber exposure points. While remote connectivity is operationally necessary, unmanaged access creates silent pathways into systems that control essential services.
Understanding and controlling remote access is critical for preventing cyber incidents from escalating into physical outages. In energy environments, visibility and discipline around remote access often determine whether a system remains resilient or becomes vulnerable.