Supply chain cyber risks in power utilities have emerged as one of the most difficult security challenges to control. Power utilities depend on a complex ecosystem of vendors, contractors, software providers, and hardware manufacturers to operate reliably. Each external dependency introduces potential cyber exposure that sits largely outside the utility’s direct control.
Unlike direct attacks on utility networks, supply chain compromises exploit trust relationships. Attackers target weaker links—vendors, updates, or maintenance providers—to gain indirect access to critical systems. This article explains how supply chain cyber risks affect power utilities, why they are so hard to detect, and how they amplify existing infrastructure weaknesses.
Quick Navigation
What the Supply Chain Looks Like in Power Utilities
Power utilities rely on suppliers for:
-
SCADA and control system software
-
Substation hardware and firmware
-
Maintenance and engineering services
-
Monitoring and analytics platforms
These dependencies are deeply intertwined with environments already affected by industrial control system security failures Each supplier connection expands the attack surface beyond the utility’s internal perimeter.
Why Supply Chain Risks Are Especially Dangerous
Trust-Based Access
Vendors often receive:
-
Elevated system privileges
-
Remote access for maintenance
-
Broad network visibility
Once compromised, vendor accounts can provide attackers with legitimate-looking access into sensitive environments.
Limited Visibility Into Vendor Security
Utilities rarely have full insight into:
-
Vendor security practices
-
Patch management processes
-
Internal access controls
This lack of transparency increases exposure across critical infrastructure cybersecurity risks
Common Supply Chain Attack Paths
Compromised Software Updates
Attackers may inject malicious code into:
-
Legitimate software updates
-
Firmware upgrades
-
Configuration packages
Because updates are trusted, they often bypass security controls entirely.
Third-Party Remote Access Abuse
Vendors frequently use persistent remote access to support legacy systems. These access paths:
-
Are rarely monitored continuously
-
May be shared across multiple customers
-
Can be reused long after contracts end
This overlap reinforces risks discussed in remote access risks in energy infrastructure
Hardware and Firmware Vulnerabilities
Compromised or poorly secured hardware can introduce:
-
Hidden backdoors
-
Insecure default configurations
-
Unpatchable vulnerabilities
Once deployed, these weaknesses are difficult to detect or remove.
Why Supply Chain Attacks Are Hard to Attribute
Supply chain incidents often appear indistinguishable from internal failures.
Challenges include:
-
Blurred responsibility between vendor and operator
-
Delayed discovery of malicious code
-
Incomplete logs across organizational boundaries
These factors complicate investigations and contribute directly to cyberattack attribution challenges
Supply Chain Risks and Nation-State Interest
Advanced threat actors favor supply chain attacks because:
-
They scale across multiple targets
-
They reduce the need for repeated intrusions
-
They exploit long-term trust relationships
These characteristics align closely with tactics associated with state-sponsored cyber operations explained
How Supply Chain Risks Amplify Outage Impact
When supply chain compromises occur:
-
Detection is delayed
-
Recovery requires vendor coordination
-
System trust must be reestablished
These delays increase the likelihood that incidents escalate into events initially perceived as power grid failure vs cyberattack
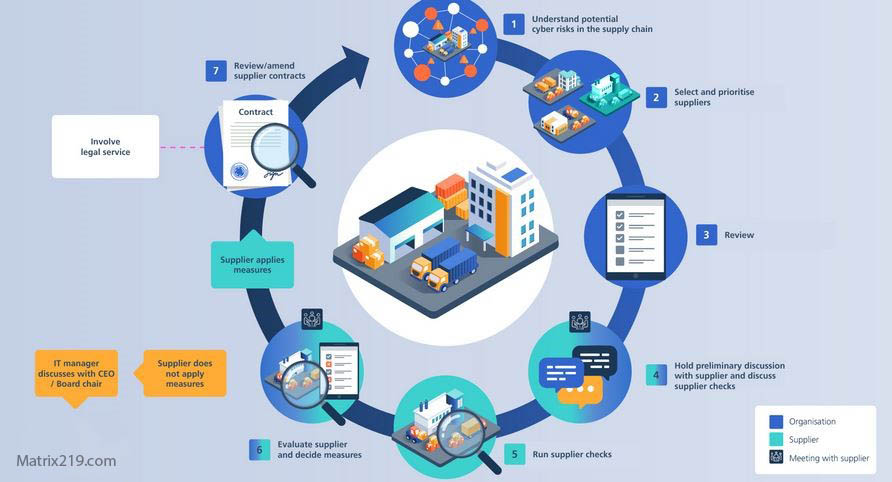
Managing Supply Chain Cyber Risks in Power Utilities
Risk reduction focuses on governance and control rather than elimination.
Key practices include:
-
Strict vendor access segmentation
-
Time-limited and audited third-party access
-
Software integrity verification
-
Contractual security requirements for suppliers
These controls support broader critical infrastructure cyber defense strategies
supply chain cyber risks in power utilities
Building Supply Chain Resilience Over Time
Effective supply chain security is continuous.
Utilities should:
-
Regularly reassess vendor risk
-
Inventory all third-party dependencies
-
Conduct joint incident response planning
-
Monitor supplier-related anomalies
Resilience depends on treating suppliers as part of the security ecosystem, not external exceptions.
Conclusion
Supply chain cyber risks in power utilities represent a shift in how critical infrastructure is targeted. Instead of attacking utilities directly, adversaries exploit trust, complexity, and interdependence.
Understanding and managing supply chain exposure is essential for preventing indirect compromises from escalating into large-scale disruptions. In modern power systems, security is only as strong as the weakest trusted connection.