When to report phone hacking to authorities is not always obvious. Many people either report too early—before understanding what happened—or too late, after evidence is lost and damage spreads. Reporting is not about panic or punishment; it’s about documentation, protection, and escalation when risk crosses certain lines.
This article explains when reporting makes sense, when it doesn’t, who to report to, and how to prepare so the report actually helps you instead of creating new problems. The goal is informed escalation, not unnecessary stress.
Quick Navigation
What “Reporting” Really Means
Reporting is about record—not instant action.
What authorities usually do
-
Create an official incident record
-
Advise on next legal or safety steps
-
Coordinate with telecoms or institutions if needed
What they usually do NOT do
-
Instantly catch the attacker
-
Perform device cleanup for you
-
Reverse financial loss on their own
Understanding this avoids false expectations.
For the full recovery context, review: If Your Phone Is Hacked: How to Know, What to Do, and How to Stay Safe
Situations Where You SHOULD Report Phone Hacking
Certain thresholds justify escalation.
Strong reasons to report
-
Financial fraud or attempted fraud
-
Identity theft or account takeover with damage
-
Stalking, harassment, or domestic abuse involving spyware
-
Work or client data exposure
-
Phone theft combined with hacking
-
Repeated compromise despite cleanup
In these cases, reporting protects you legally and procedurally.
Situations Where Reporting Is Usually Not Necessary
Not every incident needs authorities.
Reporting may be unnecessary if:
-
The compromise was app-based and resolved
-
No financial, safety, or legal impact occurred
-
You only need technical cleanup
In these cases, structured recovery is enough.
Follow the standard path here: If Your Phone Is Hacked: Step-by-Step Recovery Guide (Android & iPhone)
Who to Report To (It’s Not Always the Police)
The right authority depends on the risk.
Possible reporting channels
-
Police: fraud, stalking, theft, threats
-
Cybercrime units: digital intrusion, online fraud
-
Telecom provider: SIM abuse, IMEI actions
-
Employer or regulator: work-related exposure
Choosing the wrong channel wastes time—choose based on impact.
What to Do Before You Report
Preparation determines usefulness.
Steps to take first
-
Stop using the device if evidence matters
-
Do not reset or uninstall apps
-
Document dates, alerts, and behaviors
-
Capture screenshots and logs if possible
Destroying evidence weakens your report.
For evidence handling, see: Professional phone forensics
Reporting While Recovery Is Still Ongoing
Reporting doesn’t replace cleanup.
How reporting fits recovery
-
Report after containment, not before
-
Continue securing accounts independently
-
Follow authority instructions carefully
Never assume reporting alone makes you safe.
For mistakes to avoid, review: What not to do after phone hacking
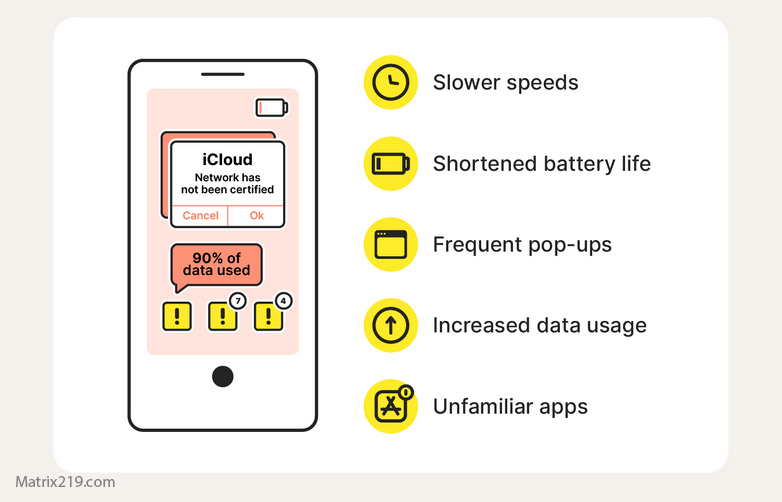
red flags hacked phone
Legal and Personal Considerations
Reporting has side effects.
Things to consider
-
Reports create official records
-
Statements should stick to facts
-
False assumptions can complicate matters
If unsure, consult legal advice before formal statements—especially in sensitive cases.
Reporting and Phone Replacement
Reporting doesn’t negate technical steps.
Key point
-
You may still need to reset or replace the phone
-
Reporting documents the incident—it doesn’t fix it
Replacement context: Is changing phone enough after hacking
When Reporting Becomes Urgent
Do not delay if:
-
You’re being monitored or threatened
-
Financial losses are active
-
Children or vulnerable people are involved
-
Work or legal exposure is growing
In these cases, safety and documentation matter more than convenience.
Law enforcement and cybercrime guidance consistently emphasize that early, well-documented reporting improves protection and legal positioning, even when technical recovery continues separately Cybercrime reporting thresholds and best practices overview
Frequently Asked Questions
Should I report phone hacking immediately?
Only after basic containment. Reporting too early—before understanding the scope—can lead to incomplete or confusing records.
Will reporting stop the hacker?
Not directly. Reporting creates documentation and enables escalation, but technical recovery is still required.
Do I need proof before reporting?
No, but clear observations and timelines help authorities take the report seriously.
Can reporting backfire legally?
It can if statements are speculative or inaccurate. Stick to facts and documented behavior.
Should I report even if no money was stolen?
Yes, if safety, harassment, work exposure, or repeat compromise is involved.





