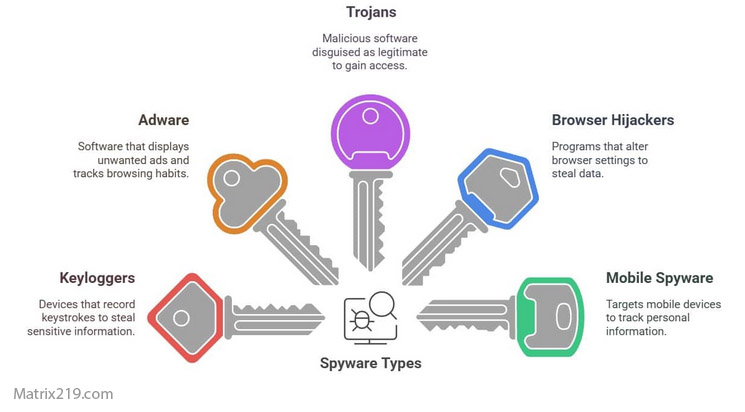
Common Types of Mobile Spyware are often misunderstood because many surveillance tools do not look malicious at first glance. Some are marketed as parental control or employee monitoring software, while others operate quietly as background services with no visible interface.
Understanding the different categories of mobile spyware helps users assess risk realistically. Not all spyware is equally advanced, and not all surveillance requires technical exploits. Many threats rely on misuse, deception, or excessive permissions rather than sophisticated hacking.
This article breaks down the main types of mobile spyware, how they differ, and what makes each category dangerous.
Stalkerware and Covert Monitoring Apps
Stalkerware is consumer-grade surveillance software often marketed for monitoring partners, children, or family members. While some uses may be legal under specific conditions, stalkerware is frequently abused for covert surveillance.
These apps typically track messages, calls, location, and app activity. They often require physical access to the device for installation and rely on powerful permissions to remain hidden.
Stalkerware represents one of the most common real-world mobile surveillance threats because it is inexpensive and widely available.
To understand early warning signs linked to these tools, see: Signs Your Phone Is Being Spied On
Commercial Spyware
Commercial spyware is far more advanced and expensive. It is often sold to governments, law enforcement agencies, or corporate entities under legal frameworks.
This type of spyware may exploit system vulnerabilities, bypass app sandboxing, and operate without obvious installation traces. Some variants can intercept communications at deep system levels.
While less common for everyday users, commercial spyware poses serious risks for journalists, activists, and high-risk individuals.
Spyware Disguised as Legitimate Apps
Some spyware hides inside apps that appear legitimate. These may include fake utilities, modified versions of popular apps, or apps that abuse permissions far beyond their stated purpose.
Once installed, these apps blend into normal device behavior and avoid drawing attention. Users often forget they exist.
Understanding how apps collect and misuse data helps clarify this risk, as explained in: How Apps Track You
Preinstalled and System-Level Monitoring
Some devices ship with preinstalled software that collects extensive usage data. While not always malicious, these components reduce transparency and limit user control.
In rare cases, modified firmware or unauthorized system software may be installed on compromised devices, especially in high-risk environments.
System-level monitoring is difficult to detect and often requires professional analysis.
Spyware Installed Through Physical Access
Many mobile surveillance cases involve physical access rather than remote attacks. Someone with access to an unlocked phone can install spyware in minutes.
This method bypasses many technical protections and highlights the importance of device locks, strong authentication, and physical security.
Understanding this threat shifts focus from “hackers” to trust boundaries.
Spyware Installed Through Physical Access
Differences Between iOS and Android Spyware
Android devices allow more flexibility in app installation, which increases exposure to stalkerware and sideloaded spyware.
iOS devices are more restrictive, but spyware may still operate through configuration profiles, enterprise certificates, or exploited vulnerabilities.
Both platforms face risks, but attack methods differ significantly.
Why Spyware Categories Matter
Knowing the category of spyware helps determine appropriate responses. Consumer-grade stalkerware can often be removed through resets and permission audits.
Advanced spyware may require device replacement or professional support. Treating all threats the same leads to either overreaction or underreaction.
Risk assessment depends on understanding what kind of surveillance is plausible.
FAQ
Is stalkerware legal?
Legality depends on jurisdiction and consent. Covert installation is often illegal.
Can commercial spyware affect regular users?
Rarely, but misidentification or collateral exposure is possible.
Are system apps always safe?
Not always. Some collect extensive data with limited transparency.
Can spyware look like a normal app?
Yes. Many disguise themselves intentionally.
Does removing one app always solve the problem?
Not if other system permissions or profiles remain active.





